Navigating the Cybersecurity Twitterverse | 23 Influential Accounts to Follow in 2023
Since our last post showcasing prominent cybersecurity accounts worth your follow, Twitter has occupied much of the limelight with stories about the tumultuous “takeover” including lawsuits, layoffs, and circulating concerns about free speech. Following Elon Musk’s acquisition in October 2022, many Twitter users flew the coop and migrated to the more decentralized social media platform Mastodon.
Though the open-source and crowdfunded Mastodon saw a huge surge in new accounts last winter, many new Mastodon users struggled to rebuild their complex social networks and have since returned to the blue bird app. For the cybersecurity community, Twitter remains the primary social media channel for all things cyber.
In the spirit of expanding our knowledge and resources, here are 23 hand-selected Twitter accounts we recommend to all those interested in learning about a wide variety of cybersecurity topics, issues, and news!
1. @matrosov | Alex Matrosov
Alex Matrosov is CEO and co-founder of Binarly Inc., where he builds an AI-powered platform to protect devices against emerging firmware threats. Alex has more than two decades of experience with reverse engineering, advanced malware analysis, firmware security, and exploitation techniques. He served as Chief Offensive Security Researcher at Nvidia and Intel Security Center of Excellence (SeCoE).
Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem. It appears that Intel BootGuard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake. Our investigation is ongoing, stay tuned for updates. https://t.co/rkxZIpReE8 pic.twitter.com/fLopw1qeSD
— Alex Matrosov (@matrosov) May 5, 2023
2. @r00tbsd | Paul Rascagnères
Paul Rascagnères is a Principal Threat Researcher at Volexity. He performs investigations to identify new threats, and he has presented his findings in several publications and at international security conferences.
Our team published a post about the #3cx supply chain attack. We describe the Windows & the MacOS backdoors. The timeline: the GitHub repo on December 7 & the infrastructure in November… Few months later a malicious update was sent to the customers : https://t.co/FCb4fTmnXy
— Paul Rascagnères (@r00tbsd) March 30, 2023
3. @silascutler | Silas Cutler
Silas Cutler is a Resident Hacker at Stairwell. He specializes in hunting advanced threat actors and malware developers, nation states and organized cybercrime groups. Prior to Stairwell, Silas was a threat intelligence practitioner at CrowdStrike, Google, Chronicle and Dell Secureworks.
This is wild when you think about it. The rapid mobilization + upskilling (learning to hunt on Shodan) in order to rapidly remediate an issue. https://t.co/rW6itYrahA
— Silas (@silascutler) May 19, 2023
4. @Wanna_VanTa | Van Ta
Van Ta is a Principal Threat Analyst on Mandiant’s Advanced Practices Team, where he leads historical research into the most impactful adversaries facing Mandiant’s customers. His research on various named threat actors FIN11, FIN12, FIN13, and APT41, has been referenced by both private and public organizations.
Really great research here with real world use cases, tooling, and testing at scale.
“…a data set to help cluster files requires a certain set of qualities. The data would need to be extractable, adversary defined, meaningful to functionality, and have ties to code reuse.”
https://t.co/MQytKaKkkW
— Van (@Wanna_VanTa) May 15, 2023
5. @n0x08 | Nate Warfield
After shipping the MS17-010, Spectre/Meltdown and Bluekeep patches in his 4.5-year tenure at the Microsoft Security Response Center, Nate Warfield is currently the Director of Threat Research & Intelligence for Eclypsium. He was featured in WIRED magazine’s “25 people doing good in 2020” for his role in starting CTI League, a volunteer group of InfoSec professionals who provided threat intelligence to hospitals during COVID-19.
Included in this update are patches for the MegaRAC SPX vulnerabilities found by my team at @eclypsium https://t.co/OVJTlKQnoU
—
Nate Warfield | @n0x08@infosec.exchange
(@n0x08) March 24, 2023
6. @LittleJoeTables | Joe DeMesy
Joe DeMesy is a Principal at Bishop Fox. Joe is an expert in red teaming, secure development, proficient in several programming languages, and is a leading contributor to various open source projects. Joe is a noted expert in the field of information security, having been quoted in MarketWatch, NPR, InformationWeek, and Dark Reading. He has also presented his research at conferences such as BSidesLV, Kiwicon, BlackHat and private conferences hosted by the US Department of Defense.
.@LittleJoeTables Offensive Wasm prezo from our Discord Live Stream Series is now available on our YouTube channel.
Check it out: https://t.co/uMVFdFEUUr #infosec
— Prelude (@preludeorg) May 19, 2023
7. @greglesnewich | Greg Lesnewich
Greg Lesnewich is senior threat researcher at Proofpoint, working on tracking malicious activity linked to the DPRK (North Korea). Greg has a background in threat intelligence, incident response, and managed detection, and previously built a threat intelligence program for a Fortune 50 financial organization.
Hashing [condenses] an unwieldy data-point into a concise figure that is easily searchable and pivotable. Some permission sets can be incredibly large… Condensing this complex string into unique 64 character value makes the handling of this data more feasible (paraphrased)
https://t.co/lKrRO0ccUZ
— Greg Lesnewich (@greglesnewich) May 15, 2023
8. @hasherezade | Aleksandra Doniec
Aleksandra “Hasherezade” Doniec is a prolific Malware Intelligence Analyst, software engineer, and consultant based in Warsaw, Poland. She is known for bringing valuable information on the infamous NotPetya ransomware to light and for releasing some of the most in-depth analysis on Kronos malware available yet. A Forbes 30 Under 30 alumni, she has written multiple tools and scripts used by security researchers globally today.
Now you can use #PEsieve via Golang & Python: https://t.co/ylIgWYgaUi & https://t.co/DHSKm9pLV3
— hasherezade (@hasherezade) May 22, 2023
9. @stvemillertime | Steve Miller
Steve Miller is a New York-based security researcher focused on adversary tradecraft, operating at the intersection of incident response, threat intelligence, and detection engineering. He is an alumni analyst of Champlain College, Mandiant, the U.S. Department of Homeland Security, U.S. Department of State, U.S. Army Intelligence and Security Command (INSCOM), and the National Security Agency. Currently, Steve is a Senior Threat Intelligence Analyst for MSTIC with particular interest in YARA, Synapse, malware methods, crowdsourcing, terrestrial RF, analogue synthesizers, and emergency management.
FRP FRP FRP https://t.co/C38F0ts9FF
— Steve YARA Synapse Miller (@stvemillertime) May 24, 2023
10. @kyleehmke | Kyle Ehmke
A Threat Intelligence Researcher with ThreatConnect, Kyle Ehmke has garnered ten years of experience as a cyber intelligence analyst. His most recent work with ThreatConnect has shed light on Russian election activity and targeted efforts against Bellingcat, WADA, and others. Kyle largely focuses his research on influence operations to better understand foreign and domestic actors’ information operations infrastructure.
Suspicious domain lebanese-athletes[.]com was registered through THCservers on 5/25 using lockvate@protonmail[.]com. Currently resolves to 185.174.101[.]48. pic.twitter.com/VmzsweHYQo
— Kyle Ehmke (@kyleehmke) May 25, 2023
11. @ophirharpaz | Ophir Harpaz
A Forbes 30 Under 30 alumni, Ophir Harpaz is currently Security Research Team Lead at Akamai Technologies. She is also an active member in Baot; a community supporting women developers, data scientists, and researchers where she co-manages a tech-blogging program. Ophir has presented at many conference events on cryptomining campaigns, attacks on data centers, and financial malware. Most recently, she was awarded the Rising Star category of SC Magazine’s Reboot awards. Ophir is passionate about keeping up reverse engineering skills sharp in her free time.
Some more work on MS-RPC. Even with unlikely-to-be-exploitable bugs, we love sharing the internal bits and bytes. Great technical post by @nachoskrnl and a nice farewell to the topic
https://t.co/OW1RXG6jMK
— Ophir Harpaz (@OphirHarpaz) May 26, 2023
12. @oxleyio | David Oxley
A Security Engineering Manager at AWS, David Oxley is an experienced leader for cyber espionage threat intelligence teams and specialized in the creation of cloud-first, threat-centric cyber threat intelligence teams in the technology sector. David’s work is driven by the intersection of human rights and cybersecurity. Prior to his work with AWS, David has investigated APT and criminal actors, served as a federal agent, worked as a digital forensic examiner, and taught in both academic and corporate settings.
If you work in cyber threat intelligence, I highly recommend taking a look at this post by Matt Richard about the threat intel biases he’s seen the most over his 25 years in CTI. These are all biases I’ve dealt with in my own work and those of my teams
https://t.co/WspJ3ohhBK
— David Oxley

(@oxleyio) May 8, 2023
13. @malwareunicorn | Amanda Rousseau
Amanda Rousseau is Principal Security Engineer at Microsoft with experience in dynamic behavior detection both on Windows and OSX platforms, reverse engineering, malware evasion techniques, and developing runtime detections. Before Microsoft, Amanda has worked with Facebook, Endgame, and FireEye, lending her skills to DoD forensic investigations and commercial incident response engagements.
What is up with these paypal scams? They are starting to look legit. If it wasn’t for the bogus phone number and invoice link. pic.twitter.com/RGBpfJPZRo
— Malware Unicorn (@malwareunicorn) April 17, 2023
14. @cybersecmeg | Meg West
Meg West is a Cybersecurity Incident Response Consultant for IBM’s X-Force Incident Response team as well as a known SME in SAP security. With over 20,000 subscribers to her cyber education YouTube channel, Meg is passionate about creating free cybersecurity content to share on various platforms and spends her free time mentoring college students as they enter the cybersecurity field. She has spoken at several international Cybersecurity conferences including ISC2’s Security Congress and SAP’s SAPPHIRE NOW.
new youtube video out talking about how to get FREE cybersecurity training and a FREE certification voucher from @ISC2 from their one million certified in cybersecurity initiative!
https://t.co/DIPpbuFSBg#ad
— meg west (@cybersecmeg) May 23, 2023
15. @AmarSaar | Saar Amar
Saar Amar is a security researcher at MSRC with expertise on vulnerability research and exploitation. Focused on reverse engineering, low-level/internals, and cloud security, Saar is well versed in exploiting everything from operating systems to hypervisors and browsers. Saar speaks at various international cyber conferences globally and regularly publishes original research to share with the greater defense community.
Time for a new blogpost! Let’s do a CHERIoT walkthrough – including a straightforward setup, understanding how we kill bug classes and mitigating attacks on our minimal TCB through practical examples, and more fun! https://t.co/GjeX2ntZUK pic.twitter.com/DWMlRIQqnN
— Saar Amar (@AmarSaar) February 28, 2023
16. @ale_sp_brazil | Alexandre Borges
A long-time SME in reverse engineering and digital forensic analysis, Alexandre Borges is currently at Blackstorm Security where he specializes in exploit development, threat hunting, malware analysis, and vulnerability research. He also provides cybersecurity education, training learners around the world on topics such as malware and memory analysis, mobile reversing, and more. Alexandre is the creator and administrator of the Malwoverview triage tool available on GitHub and is a regular speaker at many prominent cyber events including DEF CON USA, DEF CON CHINA, NO HAT Conference, DC2711, HITB, H2HC, and BHACK.
So far I’ve written 559 pages to help the security community:
1. https://t.co/CqJcmTzygA
2. https://t.co/49XWAoYgb9
3. https://t.co/eVgSSSzBhQ
4. https://t.co/5b3zrZMZXk
5. https://t.co/JMqvn2wK67
6. https://t.co/7WKSDijTIb
7. https://t.co/V3rw0gSZfu
8. https://t.co/2Hv0XLMuqU— Alexandre Borges (@ale_sp_brazil) April 26, 2023
17. @maddiestone | Maddie Stone
Maddie Stone is a prominent security researcher on Google’s Project Zero Bug Hunting team, which is focused on identifying zero days used in the wild. Maddie has also held reverse engineering and cyber system engineering roles on Google’s Android security team and John Hopkins University’s Applied Physics Lab, respectively. She has spoken across various cybersecurity conferences and teaches workshops to help develop a new generation of cyber defenders.
New RCA from @5aelo on CVE-2022-3723, a logic issue in Chrome’s Turbofan JIT compiler. https://t.co/2DXg2Ez2yc
— Maddie Stone (@maddiestone) May 25, 2023
18. @cyberwarship | Florian Hansemann
Munich-based Florian Hansemann is the founder of HanseSecure; an established cybersecurity company dedicated to identifying and broadcasting vulnerabilities in hardware and software to educate fellow defenders in the space. Florian has expressed interest in many areas of technical IT security but notes a special passion for red teaming and penetration testing on enterprises.
“Sophisticated DownEx Malware Campaign Targeting Central Asian Governments”#infosec #pentest #redteam https://t.co/bQaIdUCLEI pic.twitter.com/x0t4yKNHo8
— Florian Hansemann (@CyberWarship) May 26, 2023
19. @dinosn | Nicolas Krassas
Nicholas Krassas, Head of Threat & Vulnerability Management for Henkel, has deep experience in malware analysis, forensic data evaluation, system and network security, reverse engineering, and auditing. Prior to Henkel, Nicholas has also worked for Hack the Box, GIG Technology, and Efffortel, holding CSO and CTO positions to handle critical cases and projects. He often shares cyber news affecting multiple industries on his Twitter account to raise awareness on the latest attacks and threat intel.
Hidden Desktop (often referred to as HVNC) is a tool that allows operators to interact with a remote desktop session without the user knowing. https://t.co/mG60DAVANE
— Nicolas Krassas (@Dinosn) May 26, 2023
20. @h2jazi | Hossein Jazi
Hossein Jazi is currently a Senior Cyber Threat Intelligence Specialist at Fortinet with a special interest in tracking advanced persistent threats (APTs), malware analysis, cyber threat intelligence, and machine learning. Prior to his role with Fortinet, he has also worked as a threat analyst for Malwarebytes, Cysiv, Trend Micro, and Bell. Hossein’s current focus is on detecting and tracking APT campaigns in North America as well as developing big data machine learning based models to attribute threat actors.
This is another sample of #Lazarus #APT part of this campaign:https://t.co/HOaKCAmJ6l
It is a malicious PDF reader for #macOS3f6566477e496c573e4e90acd15f242980cfdf5f27903a0eac287b05380b7132
Spirit Blockchain Capital 2023 – Pitch Deck.zip pic.twitter.com/ss5gI6lXyM— Jazi (@h2jazi) May 25, 2023
21. @bushidotoken | Will Thomas
Will Thomas is a prominent cybersecurity researcher who has had his work featured by several well known publications such as The Telegraph, VICE, CyberScoop, BleepingComputer, TheRegister, KrebsOnSecurity, VirusTotal, and more. Currently a CTI researcher and threat hunter at the Equinix Threat Analysis Center (ETAC), he has previously appeared on Darknet Diaries, spoken at multiple conferences like DEFCON29, conINT, and NFCERT’s annual conference, and is the author of the SANS FOR589: Cybercrime Intelligence course.
The #Bumblebee MSI that is dropped is this: https://t.co/SOn5C32581
It contains this PS1 that contains the Base64-encoded and compressed payload: https://t.co/q8pHvo22bz https://t.co/niCtBtKKtC pic.twitter.com/FmG9pGGhBL— Tommy M (TheAnalyst) (@ffforward) April 18, 2023
22. @milenkowski | Aleksandar Milenkoski
Aleksandar Milenkoski is a Senior Threat Researcher at SentinelLabs, with expertise in reverse engineering, malware research, and threat actor analysis. Aleksandar has a PhD in system security and is the author of numerous research papers, book chapters, blog posts, and conference talks. His research has won awards from SPEC, the Bavarian Foundation for Science, and the University of Würzburg.
Just days after our #Kimsuky report, @LabsSentinel reveals details on operation Magalenha: A Brazilian threat group targets PII and credentials of Portuguese financial institutions.
Read more: https://t.co/a6f9AbxSZU
— Aleksandar Milenkoski (@milenkowski) May 25, 2023
23. @tomhegel | Tom Hegel
Tom Hegel is a Senior Threat Researcher with SentinelLabs. He comes from a background of detection and analysis of malicious actors, malware, and global events with an application to the cyber domain. His past research has focused on threats impacting individuals and organizations across the world, primarily targeted attackers.
A cache of emails, documents, and photos from a cloud storage account belonging to… APT31 operator
holy spice, and its only a Tuesday https://t.co/dOBFAr5Pm7
— Tom Hegel (@TomHegel) May 16, 2023
Conclusion
It will likely be some time before the dust settles on the futures of Twitter and other microblogging platforms, but the cybersecurity community will continue to build on shared knowledge and new research. For this post, we’ve sifted through such a small corner of Twitter to highlight 23 accounts covering a variety of malware research, reverse engineering tactics, cyber news, and more.
Don’t forget to check out our previous lists here and here and if you’re a fan of all things Apple, we even have a dedicated list of great Twitter accounts for iOS and macOS.
If you think we’ve missed any essential accounts, connect with us on Twitter by following @SentinelOne! You can also keep up to date with all of the latest threat intel coming from our SentinelLabs team on Twitter as well – we’ll be glad to meet you there.










 Cloud
Cloud
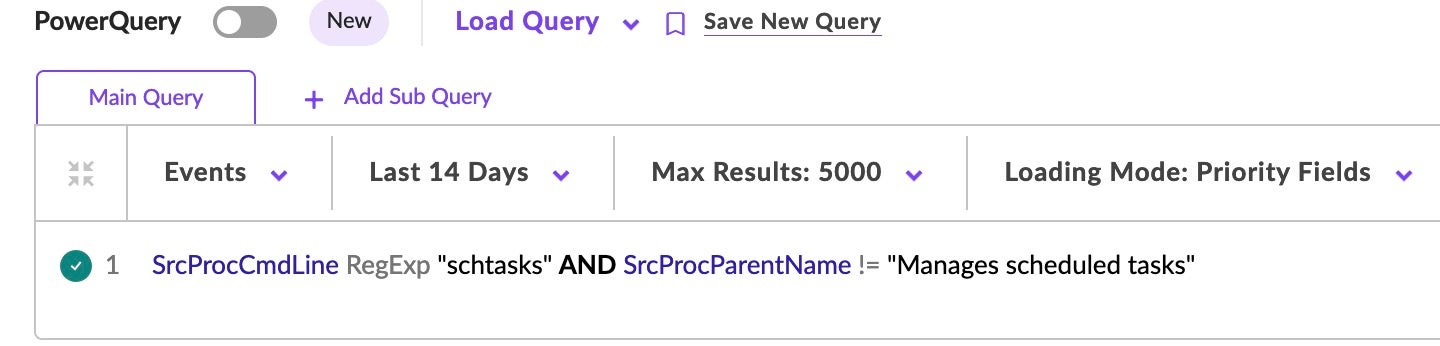
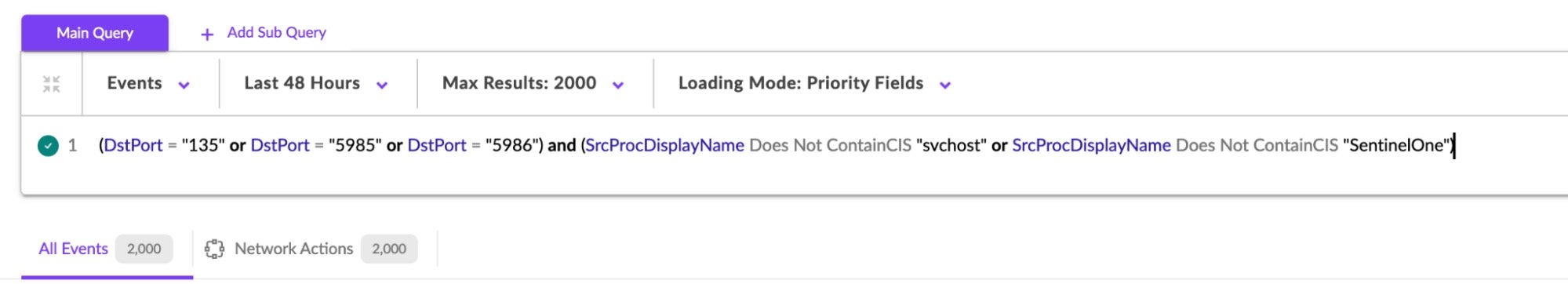
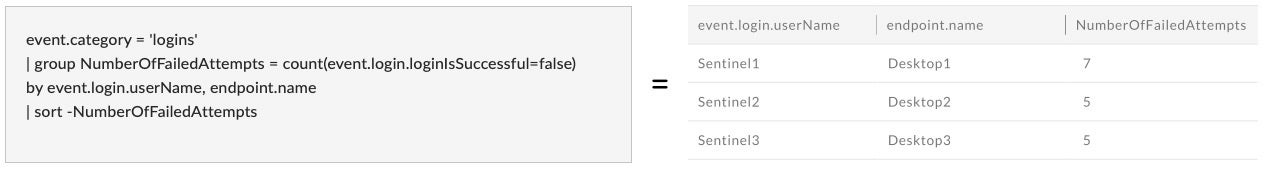
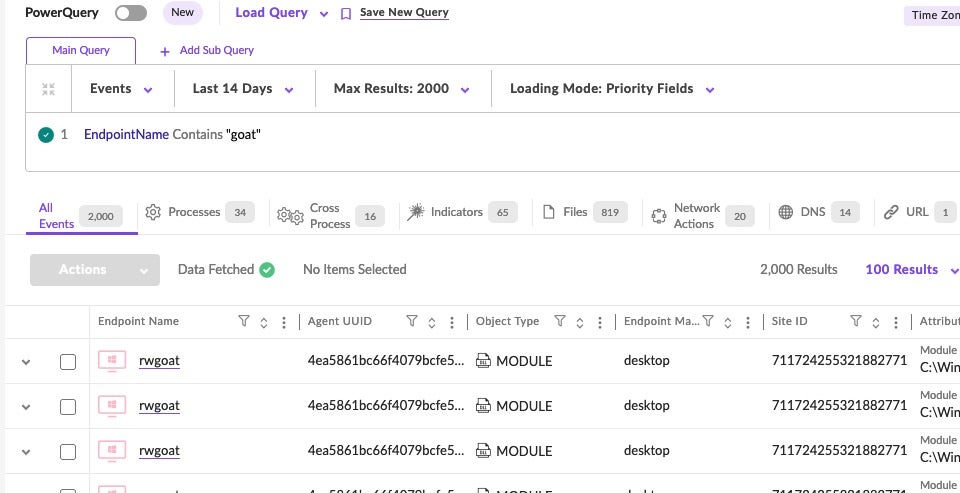
 Additional Methods/DV Queries.
Additional Methods/DV Queries.