In October 2016, media outlets reported that data collected by some of the world’s most renowned cybersecurity experts had identified frequent and unexplained communications between an email server used by the Trump Organization and Alfa Bank, one of Russia’s largest financial institutions. Those publications set off speculation about a possible secret back-channel of communications, as well as a series of lawsuits and investigations that culminated last week with the indictment of the same former federal cybercrime prosecutor who brought the data to the attention of the FBI five years ago.

The first page of Alfa Bank’s 2020 complaint.
Since 2018, access to an exhaustive report commissioned by the U.S. Senate Armed Services Committee on data that prompted those experts to seek out the FBI has been limited to a handful of Senate committee leaders, Alfa Bank, and special prosecutors appointed to look into the origins of the FBI investigation on alleged ties between Trump and Russia.
That report is now public, ironically thanks to a pair of lawsuits filed by Alfa Bank, which doesn’t directly dispute the information collected by the researchers. Rather, it claims that the data they found was the result of a “highly sophisticated cyberattacks against it in 2016 and 2017” intended “to fabricate apparent communications” between Alfa Bank and the Trump Organization.
The data at issue refers to communications traversing the Domain Name System (DNS), a global database that maps computer-friendly coordinates like Internet addresses (e.g., 8.8.8.8) to more human-friendly domain names (example.com). Whenever an Internet user gets online to visit a website or send an email, the user’s device sends a query through the Domain Name System.
Many different entities capture and record this DNS data as it traverses the public Internet, allowing researchers to go back later and see which Internet addresses resolved to what domain names, when, and for how long. Sometimes the metadata generated by these lookups can be used to identify or infer persistent network connections between different Internet hosts.
The DNS strangeness was first identified in 2016 by a group of security experts who told reporters they were alarmed at the hacking of the Democratic National Committee, and grew concerned that the same attackers might also target Republican leaders and institutions.
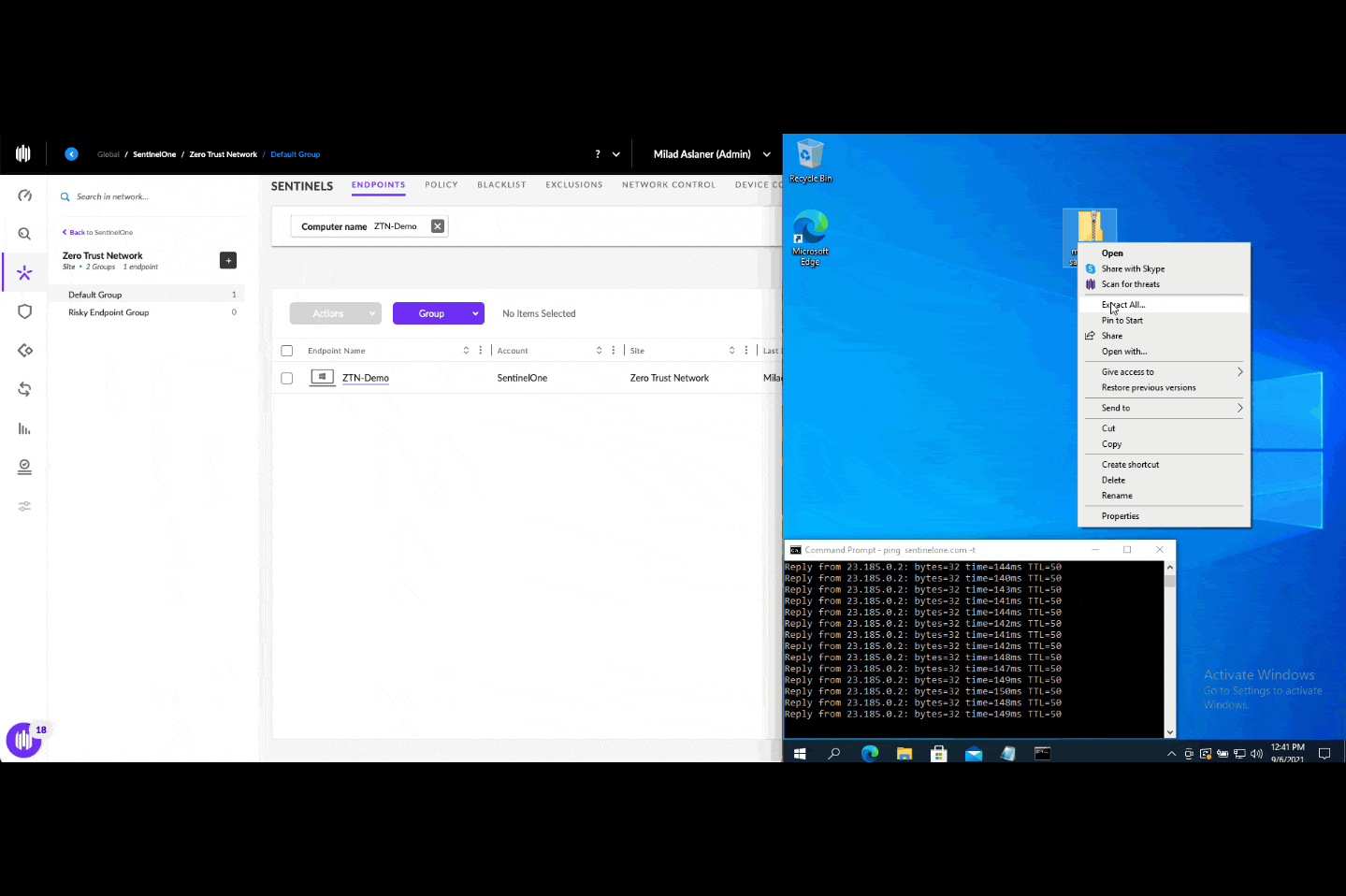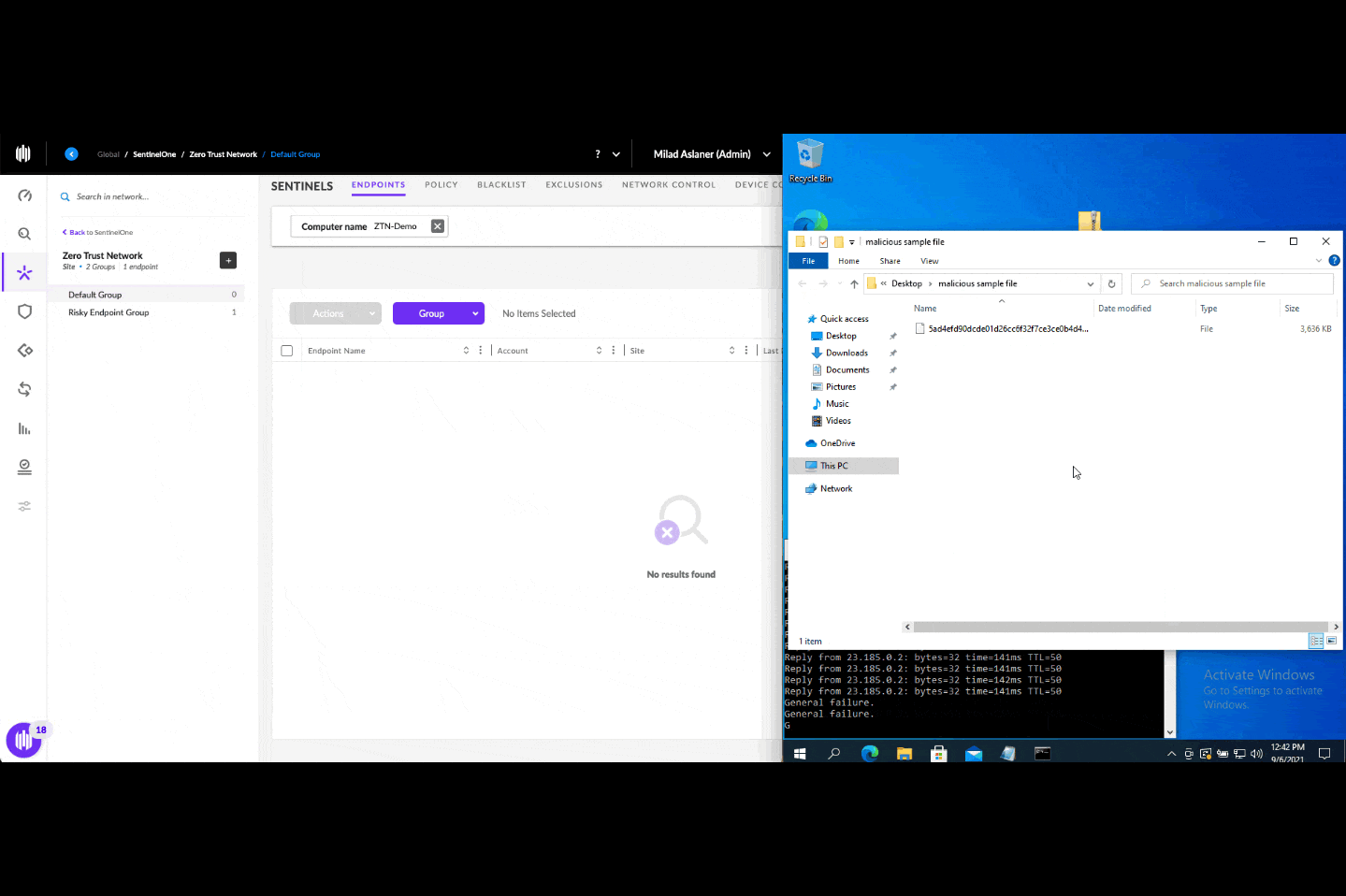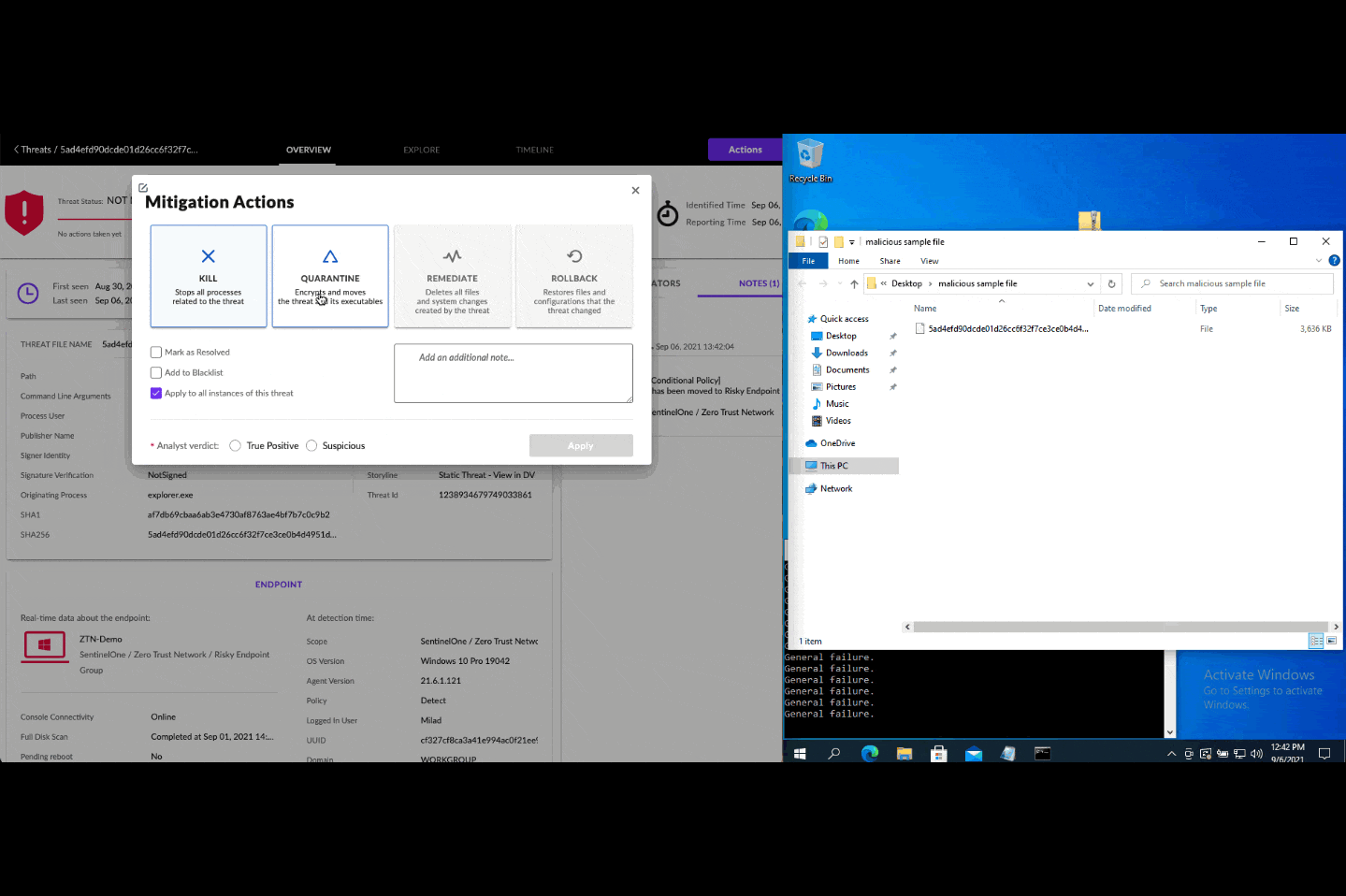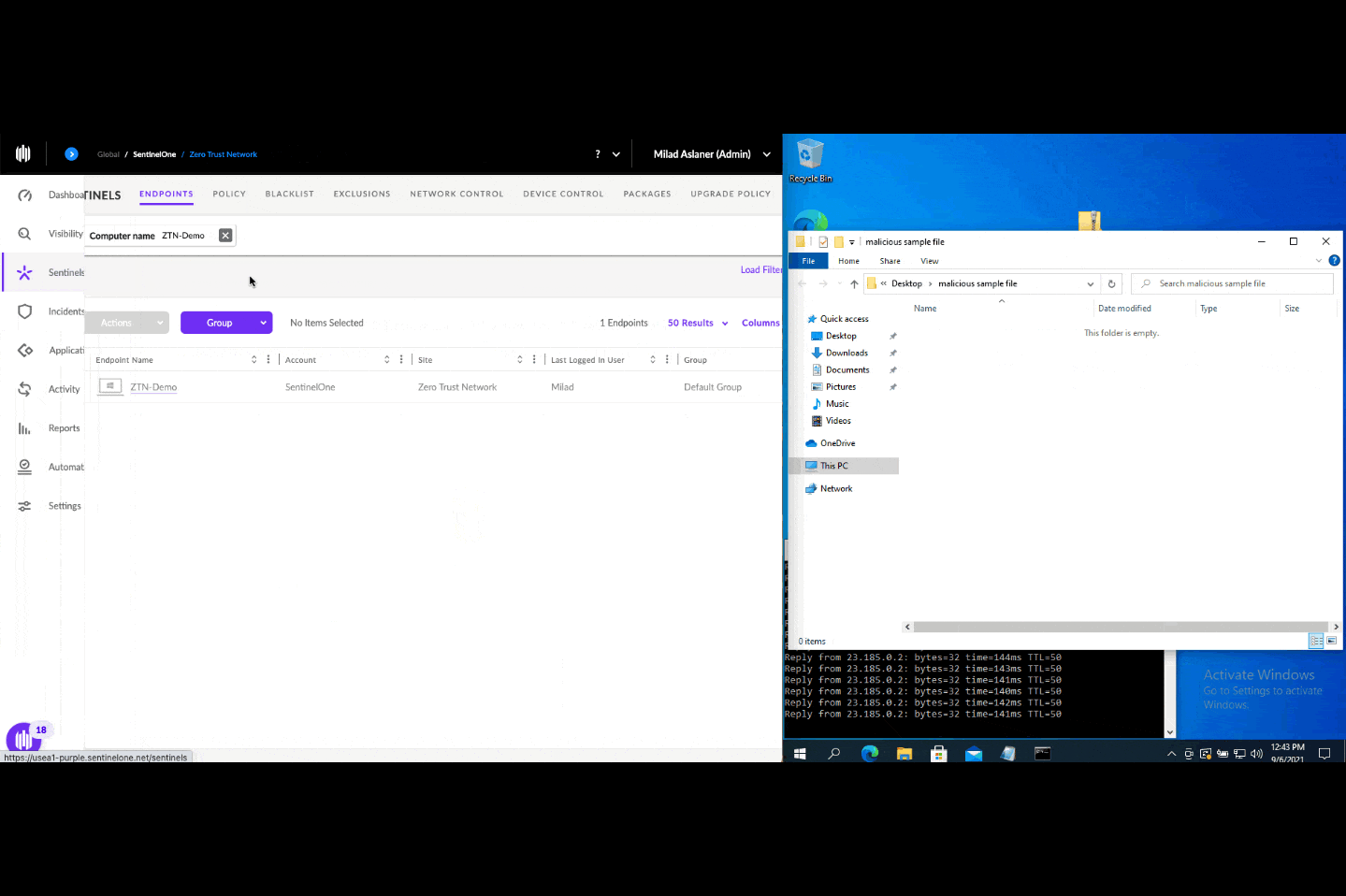
Scrutinizing the Trump Organization’s online footprint, the researchers determined that for several months during the spring and summer of 2016, Internet servers at Alfa Bank in Russia, Spectrum Health in Michigan, and Heartland Payment Systems in New Jersey accounted for nearly all of the several thousand DNS lookups for a specific Trump Organization server (mail1.trump-email.com).

This chart from a court filing Sept. 14, 2021 shows the top sources of traffic to the Trump Organization email server over a four month period in the spring and summer of 2016. DNS lookups from Alfa Bank constituted the majority of those requests.
The researchers said they couldn’t be sure what kind of communications between those servers had caused the DNS lookups, but concluded that the data would be extremely difficult to fabricate.
As recounted in this 2018 New Yorker story, New York Times journalist Eric Lichtblau met with FBI officials in late September 2016 to discuss the researchers’ findings. The bureau asked him to hold the story because publishing might disrupt an ongoing investigation. On Sept. 21, 2016, Lichtblau reportedly shared the DNS data with B.G.R., a Washington lobbying firm that worked with Alfa Bank.
Lichtblau’s reporting on the DNS findings ended up buried in an October 31, 2016 story titled “Investigating Donald Trump, F.B.I. Sees No Clear Link to Russia,” which stated that the FBI “ultimately concluded that there could be an innocuous explanation, like marketing email or spam,” that might explain the unusual DNS connections.
But that same day, Slate’s Franklin Foer published a story based on his interactions with the researchers. Foer noted that roughly two days after Lichtblau shared the DNS data with B.G.R., the Trump Organization email server domain vanished from the Internet — its domain effectively decoupled from its Internet address.
Foer wrote that The Times hadn’t yet been in touch with the Trump campaign about the DNS data when the Trump email domain suddenly went offline. Odder still, four days later the Trump Organization created a new host — trump1.contact-client.com — and the very first DNS lookup to that new domain came from servers at Alfa Bank.
The researchers concluded that the new domain enabled communication to the very same server via a different route.
“When a new host name is created, the first communication with it is never random,” Foer wrote. “To reach the server after the resetting of the host name, the sender of the first inbound mail has to first learn of the name somehow. It’s simply impossible to randomly reach a renamed server.”
“That party had to have some kind of outbound message through SMS, phone, or some noninternet channel they used to communicate [the new configuration],” DNS expert Paul Vixie told Foer. “The first attempt to look up the revised host name came from Alfa Bank. If this was a public server, we would have seen other traces. The only look-ups came from this particular source.”
THE THEORIES
Both the Trump organization and Alfa Bank have denied using or establishing any sort of secret channel of communications, and have offered differing explanations as to how the data gathered by the experts could have been faked or misinterpreted.
In a follow-up story by Foer, the Trump Organization suggested that the DNS lookups might be the result of spam or email advertising various Trump properties, and said a Florida based marketing firm called Cendyn registered and managed the email server in question.
But Cendyn told CNN that its contract to provide email marketing services to the Trump Organization ended in March 2016 — weeks before the DNS lookups chronicled by the researchers started appearing. Cendyn told CNN that a different client had been communicating with Alfa Bank using Cendyn communications applications — a claim that Alfa Bank denied.
Alfa Bank subsequently hired computer forensics firms Mandiant and Stroz Friedberg to examine the DNS data presented by the researchers. Both companies concluded there was no evidence of email communications between Alfa Bank and the Trump Organization. However, both firms also acknowledged that Alfa Bank didn’t share any DNS data for the relevant four-month time period identified by the researchers.
Another theory for the DNS weirdness outlined in Mandiant’s report is that Alfa Bank’s servers performed the repeated DNS lookups for the Trump Organization server because its internal Trend Micro antivirus product routinely scanned domains in emails for signs of malicious activity — and that incoming marketing emails promoting Trump properties could have explained the traffic.
The researchers maintained this did not explain similar and repeated DNS lookups made to the Trump Organization email server by Spectrum Health, which is closely tied to the DeVos family (Betsy DeVos would later be appointed Secretary of Education by President Trump).
FISHING EXPEDITION
In June 2020, Alfa Bank filed two “John Doe” lawsuits, one in Pennsylvania and another in Florida. Their stated purpose was to identify the anonymous hackers behind the “highly sophisticated cyberattacks” that they claim were responsible for the mysterious DNS lookups.
Alfa Bank has so far subpoenaed at least 49 people or entities — including all of the security experts quoted in the 2016 media stories referenced above, and others who’d merely offered their perspectives on the matter via social media. At least 15 of those individuals or entities have since been deposed. Alfa Bank’s most recent subpoena was issued Aug. 26, 2021.
L. Jean Camp, a professor at the Indiana University School of Informatics and Computing, was among the first to publish some of the DNS data collected by the research group. In 2017, Alfa Bank sent Camp a series of threatening letters suggesting she was “a central figure” in the what the company would later claim was “malicious cyber activity targeting its computer network.” The letters and responses from her attorneys are published on her website.
Camp’s attorneys and Indiana University have managed to keep her from being deposed by both Alfa Bank and John H. Durham, the special counsel appointed by the Trump administration to look into the origins of the Russia investigation (although Camp said Alfa Bank was able to obtain certain emails through the school’s public records request policy).
“If MIT had had the commitment to academic freedom that Indiana University has shown throughout this entire process, Aaron Swartz would still be alive,” Camp said.
Camp said she’s bothered that the Alfa Bank and Trump special counsel investigations have cast the researchers in such a sinister light, when many of those subpoenaed have spent a lifetime trying to make the Internet more secure.
“Not including me, they’ve subpoenaed some people who are significant, consistent and important contributors to the security of American networks against the very attacks coming from Russia,” Camp said. “I think they’re using law enforcement to attack network security, and to determine the ways in which their previous attacks have been and are being detected.”
Nicholas Weaver, a lecturer at the computer science department at University of California, Berkeley, told KrebsOnSecurity he complied with the subpoena requests for specific emails he’d sent to colleagues about the DNS data, noting that Alfa Bank could have otherwise obtained them through the schools’ public records policy.
Weaver said Alfa Bank’s lawsuit has nothing to do with uncovering the truth about the DNS data, but rather with intimidating and silencing researchers who’ve spoken out about it.
“It’s clearly abusive, so I’m willing to call it out for what it is, which is a John Doe lawsuit for a fishing expedition,” Weaver said.
TURNABOUT IS FAIR PLAY
Among those subpoenaed and deposed by Alfa Bank was Daniel J. Jones, a former investigator for the FBI and the U.S. Senate who is perhaps best known for his role in leading the investigation into the U.S. Central Intelligence Agency’s use of torture in the wake of the Sept. 11 attacks.
Jones runs The Democracy Integrity Project (TDIP), a nonprofit in Washington, D.C. whose stated mission includes efforts to research, investigate and help mitigate foreign interference in elections in the United States and its allies overseas. In 2018, U.S. Senate investigators asked TDIP to produce and share a detailed analysis of the DNS data, which it did without payment. That lengthy report was never publicly released by the committee nor anyone else.
That is, until Sept. 14, 2021, when Jones and TDIP filed their own lawsuit against Alfa Bank. According to Jones’ complaint, Alfa Bank had entered into a confidentiality agreement regarding certain sensitive and personal information Jones was compelled to provide as part of complying with the subpoena.
Yet on Aug. 20, Alfa Bank attorneys sent written notice that it was challenging portions of the confidentiality agreement. Jones’ complaint asserts that Alfa Bank intends to publicly file portions of these confidential exhibits, an outcome that could jeopardize his safety.
This would not be the first time testimony Jones provided under a confidentiality agreement ended up in the public eye. TDIP’s complaint notes that before Jones met with FBI officials in 2017 to discuss Russian disinformation campaigns, he was assured by two FBI agents that his identity would be protected from exposure and that any information he provided to the FBI would not be associated with him.
Nevertheless, in 2018 the House Permanent Select Committee on Intelligence released a redacted report on Russian active measures. The report blacked out Jones’ name, but a series of footnotes in the report named his employer and included links to his organization’s website. Jones’ complaint spends several pages detailing the thousands of death threats he received after that report was published online.
THE TDIP REPORT
As part of his lawsuit against Alfa Bank, Jones published 40 pages from the 600+ page report he submitted to the U.S. Senate in 2018. From reviewing its table of contents, the remainder of the unpublished report appears to delve deeply into details about Alfa Bank’s history, its owners, and their connections to the Kremlin.
The report notes that unlike other domains the Trump Organization used to send mass marketing emails, the domain at issue — mail1.trump-email.com — was configured in such a way that would have prevented it from effectively sending marketing or bulk emails. Or at least prevented most of the missives sent through the domain from ever making it past spam filters.

Nor was the domain configured like other Trump Organization domains that demonstrably did send commercial email, Jones’ analysis found. Also, the mail1.trump-email.com domain was never once flagged as sending spam by any of the 57 different spam block lists published online at the time.
“If large amounts of marketing emails were emanating from mail1.trump-email.com, it’s likely that some receivers of those emails would have marked them as spam,” Jones’ 2018 report reasons. “Spam is nothing new on the internet, and mass mailings create easily observed phenomena, such as a wide dispersion of backscatter queries from spam filters. No such evidence is found in the logs.”
However, Jones’ report did find that mail1.trump-email.com was configured to accept incoming email. Jones cites testing conducted by one of the researchers who found the mail1.trump-email.com rejected messages with an automated reply saying the server couldn’t accept messages from that particular sender.
“This test reveals that either the server was configured to reject email from everyone, or that the server was configured to accept only emails from specific senders,” TDIP wrote.
The report also puts a finer point on the circumstances surrounding the disappearance of that Trump Organization email domain just two days after The New York Times shared the DNS data with Alfa Bank’s representatives.
“After the record was deleted for mail1.trump-email.com on Sept. 23, 2016, Alfa Bank and Spectrum Health continued to conduct DNS lookups for mail1.trump-email.com,” reads the report. “In the case of Alfa Bank, this behavior persisted until late Friday night on Sept. 23, 2016 (Moscow time). At that point, Alfa Bank ceased its DNS lookups of mail1.trump-email.com.”
Less than ten minutes later, a server assigned to Alfa Bank was the first source in the DNS data-set examined (37 million DNS records from January 1, 2016 to January 15, 2017) to conduct a DNS look-up for the server name ‘trump1.contact-client.com.’ The answer received was 66.216.133.29 — the same IP address used for mail1.trump-email.com that was deleted in the days after The New York Times inquired with Alfa Bank about the unusual server connections.
“No servers associated with Alfa Bank ever conducted a DNS lookup for trump1.contact-client.com again, and the next DNS look-up for trump1.contact-client.com did not occur until October 5, 2016,” the report continues. “Three of these five look-ups from October 2016 originated from Russia.”
A copy of the complaint filed by Jones against Alfa Bank is available here (PDF).
THE SUSSMANN INDICTMENT
The person who first brought the DNS data to the attention of the FBI in Sept. 2016 was Michael Sussmann, a 57-year-old cybersecurity lawyer and former computer crimes prosecutor who represented the Democratic National Committee and Hillary Clinton’s presidential campaign.
Last week, the special counsel Durham indicted Sussmann on charges of making a false statement to the FBI. The New York Times reports the accusation focuses on a meeting Sussmann had Sept. 19, 2016 with James A. Baker, the FBI’s top lawyer at the time. Sussmann had reportedly met with Baker to discuss the DNS data uncovered by the researchers.
“The indictment says Mr. Sussmann falsely told the F.B.I. lawyer that he had no clients, but he was really representing both a technology executive and the Hillary Clinton campaign,” The Times wrote.
Sussmann has pleaded not guilty to the charges.
ANALYSIS
The Sussmann indictment refers to the various researchers who contacted him in 2016 by placeholder names, such as Tech Executive-1 and Researcher-1 and Researcher-2. The tone of indictment reads as if describing a vast web of nefarious or illegal activities, although it doesn’t attempt to address the veracity of any specific concerns raised by the researchers. Here is one example:
“From in or about July 2016 through at least in or about February 2017, however, Originator-I, Researcher-I, and Researcher-2 also exploited Internet Company-1′ s data and other data to assist Tech Executive-I in his efforts to conduct research concerning Trump’s potential ties to Russia.”
Quoting from emails between Tech Executive-1 and the researchers, the indictment makes clear that Mr. Durham has subpoenaed many of the same researchers who’ve been subpoenaed and or deposed in the concurrent John Doe lawsuits from Russia’s Alfa Bank.
To date, Alfa Bank has yet to name a single defendant in its lawsuits. In the meantime, the Sussmann indictment is being dissected by many users on social media who have been closely following the Trump administration’s inquiry into the Russia investigation. The majority of these social media posts appear to be crowdsourcing an effort to pinpoint the real-life identities behind the placeholder names in the indictment.
At one level, it doesn’t matter which explanation of the DNS data you believe: There is a very real possibility that the way this entire inquiry has been handled could negatively affect the FBI’s ability to collect crucial and sensitive investigative tips for years to come.
After all, who in their right mind is going to volunteer confidential information to the FBI if they fear there’s even the slightest chance that future shifting political winds could end up seeing them prosecuted, threatened with physical violence or death on social media, and/or exposed to expensive legal fees and depositions from private companies as a result?
Such a perception could give rise to a sort of “chilling effect,” discouraging honest, well-meaning people from speaking up when they suspect or know about a potential threat to national security or sovereignty.
This would be a less-than-ideal outcome in the context of today’s top cyber threat for most organizations: Ransomware. With few exceptions, the U.S. government has watched helplessly as organized cybercrime gangs — many of whose members hail from Russia or from former Soviet nations that are friendly to Moscow — have extorted billions of dollars from victims, and disrupted or ruined countless businesses.
To help shift the playing field against ransomware actors, the Justice Department and other federal law enforcement agencies have been trying to encourage more ransomware victims to come forward and share sensitive details about their attacks. The U.S. government has even offered up to $10 million for information leading to the arrest and conviction of cybercriminals involved in ransomware.
But given the way the government has essentially shot the all of the messengers with its handling of the Sussmann case, who could blame those with useful and valid tips if they opted to stay silent?