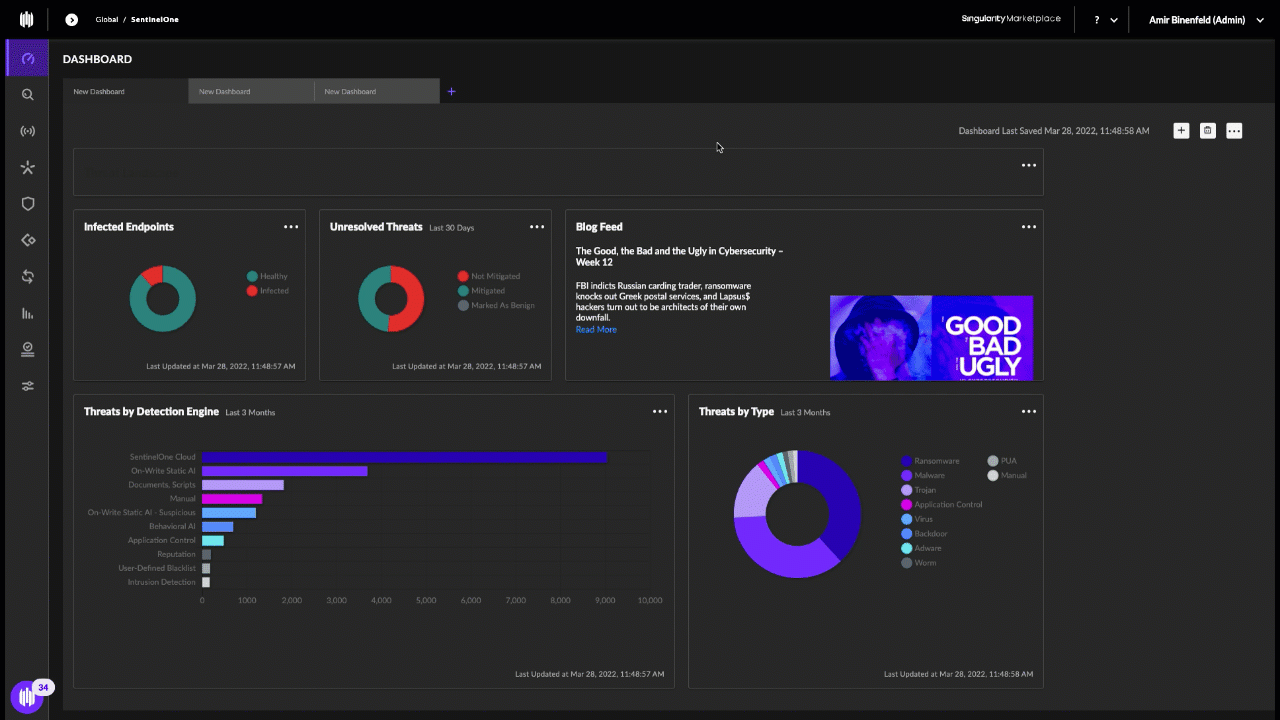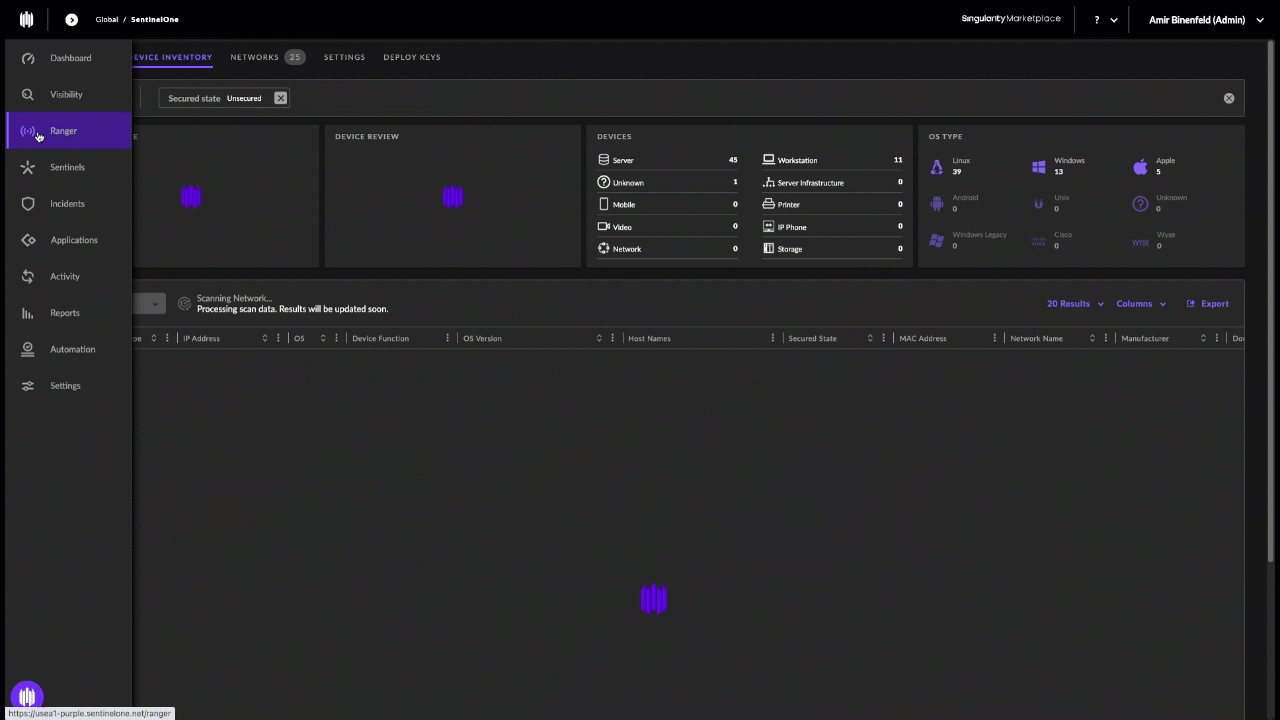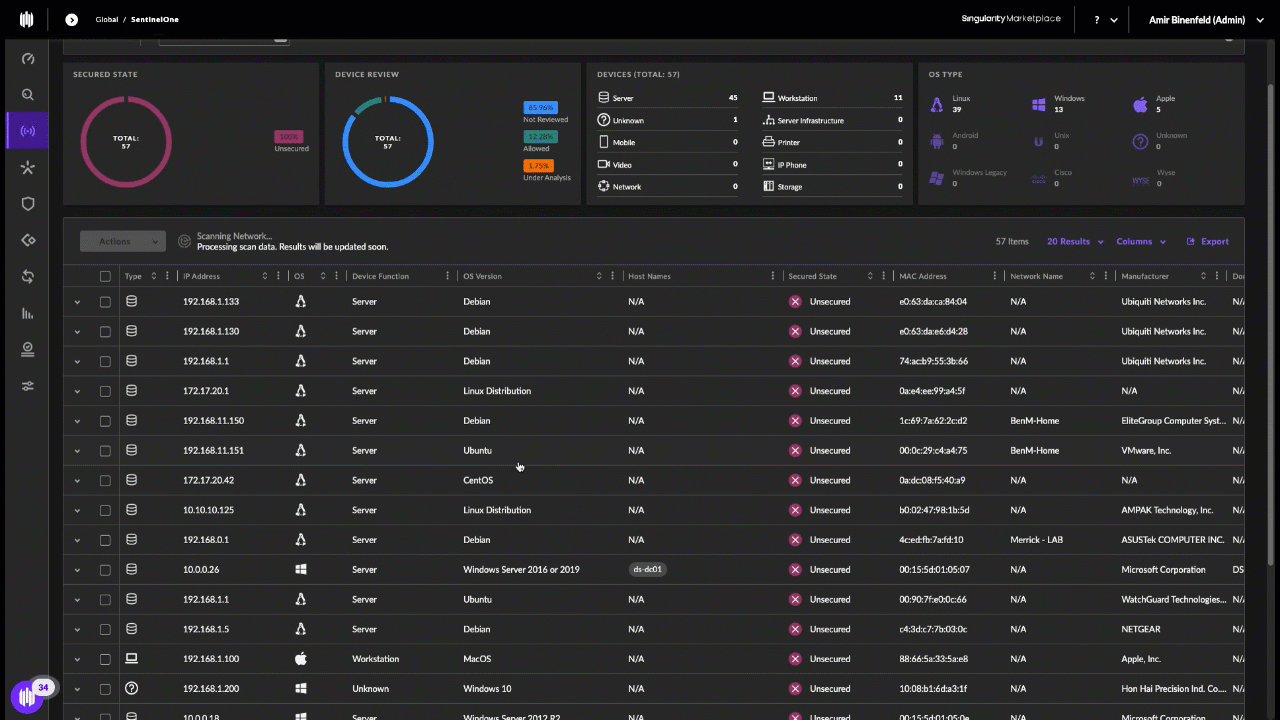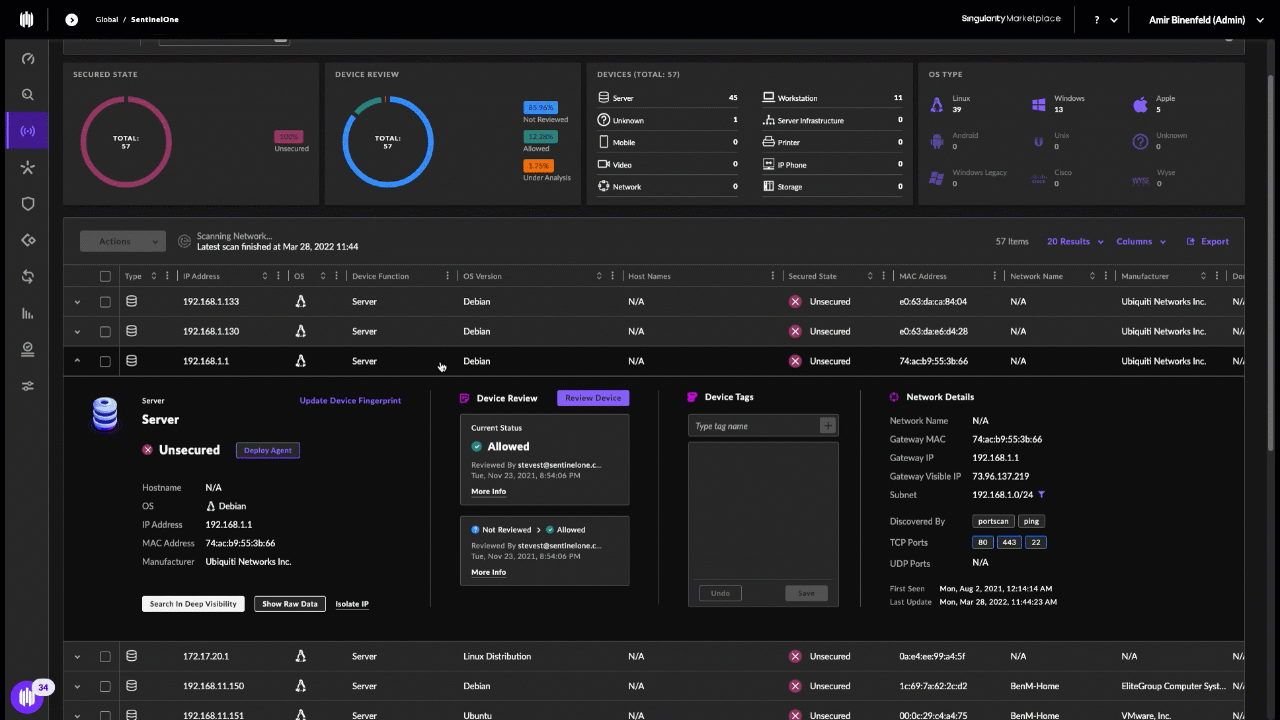
There is a terrifying and highly effective “method” that criminal hackers are now using to harvest sensitive customer data from Internet service providers, phone companies and social media firms. It involves compromising email accounts and websites tied to police departments and government agencies, and then sending unauthorized demands for subscriber data while claiming the information being requested can’t wait for a court order because it relates to an urgent matter of life and death.

In the United States, when federal, state or local law enforcement agencies wish to obtain information about who owns an account at a social media firm, or what Internet addresses a specific cell phone account has used in the past, they must submit an official court-ordered warrant or subpoena.
Virtually all major technology companies serving large numbers of users online have departments that routinely review and process such requests, which are typically granted as long as the proper documents are provided and the request appears to come from an email address connected to an actual police department domain name.
But in certain circumstances — such as a case involving imminent harm or death — an investigating authority may make what’s known as an Emergency Data Request (EDR), which largely bypasses any official review and does not require the requestor to supply any court-approved documents.
It is now clear that some hackers have figured out there is no quick and easy way for a company that receives one of these EDRs to know whether it is legitimate. Using their illicit access to police email systems, the hackers will send a fake EDR along with an attestation that innocent people will likely suffer greatly or die unless the requested data is provided immediately.
In this scenario, the receiving company finds itself caught between two unsavory outcomes: Failing to immediately comply with an EDR — and potentially having someone’s blood on their hands — or possibly leaking a customer record to the wrong person.
“We have a legal process to compel production of documents, and we have a streamlined legal process for police to get information from ISPs and other providers,” said Mark Rasch, a former prosecutor with the U.S. Department of Justice.
“And then we have this emergency process, almost like you see on [the television series] Law & Order, where they say they need certain information immediately,” Rasch continued. “Providers have a streamlined process where they publish the fax or contact information for police to get emergency access to data. But there’s no real mechanism defined by most Internet service providers or tech companies to test the validity of a search warrant or subpoena. And so as long as it looks right, they’ll comply.”
To make matters more complicated, there are tens of thousands of police jurisdictions around the world — including roughly 18,000 in the United States alone — and all it takes for hackers to succeed is illicit access to a single police email account.
THE LAPSUS$ CONNECTION
The reality that teenagers are now impersonating law enforcement agencies to subpoena privileged data on their targets at whim is evident in the dramatic backstory behind LAPSUS$, the data extortion group that recently hacked into some of the world’s most valuable technology companies, including Microsoft, Okta, NVIDIA and Vodafone.
In a blog post about their recent hack, Microsoft said LAPSUS$ succeeded against its targets through a combination of low-tech attacks, mostly involving old-fashioned social engineering — such as bribing employees at or contractors for the target organization.
“Other tactics include phone-based social engineering; SIM-swapping to facilitate account takeover; accessing personal email accounts of employees at target organizations; paying employees, suppliers, or business partners of target organizations for access to credentials and multi-factor authentication (MFA) approval; and intruding in the ongoing crisis-communication calls of their targets,” Microsoft wrote of LAPSUS$.

The roster of the now-defunct “Infinity Recursion” hacking team, from which some members of LAPSUS$ allegedly hail.
Researchers from security firms Unit 221B and Palo Alto Networks say that prior to launching LAPSUS$, the group’s leader “White” (a.k.a. “WhiteDoxbin,” “Oklaqq”) was a founding member of a cybercriminal group calling itself the “Recursion Team.” This group specialized in SIM swapping targets of interest and participating in “swatting” attacks, wherein fake bomb threats, hostage situations and other violent scenarios are phoned in to police as part of a scheme to trick them into visiting potentially deadly force on a target’s address.
The founder of the Recursion Team was a then 14-year-old from the United Kingdom who used the handle “Everlynn.” On April 5, 2021, Everlynn posted a new sales thread to the cybercrime forum cracked[.]to titled, “Warrant/subpoena service (get law enforcement data from any service).” The price: $100 to $250 per request.

Everlynn advertising a warrant/subpoena service based on fake EDRs. Image: Ke-la.com.
“Services [include] Apple, Snapchat, Google (more expensive), not doing Discord, basically any site mostly,” read Everlynn’s ad, which was posted by the user account “InfinityRecursion.”
A month prior on Cracked, Everlynn posted a sales thread, “1x Government Email Account || BECOME A FED!,” which advertised the ability to send email from a federal agency within the government of Argentina.
“I would like to sell a government email that can be used for subpoena for many companies such as Apple, Uber, Instagram, etc.,” Everlynn’s sales thread explained, setting the price at $150. “You can breach users and get private images from people on SnapChat like nudes, go hack your girlfriend or something haha. You won’t get the login for the account, but you’ll basically obtain everything in the account if you play your cards right. I am not legally responsible if you mishandle this. This is very illegal and you will get raided if you don’t use a vpn. You can also breach into the government systems for this, and find LOTS of more private data and sell it for way, way more.”
Last week, the BBC reported that authorities in the United Kingdom had detained seven individuals aged 16 to 21 in connection with LAPSUS$.
TAKING ON THE DOXBIN
It remains unclear whether White or Everlynn were among those detained; U.K. police declined to name the suspects. But White’s real-life identity became public recently after he crossed the wrong people.
The de-anonymization of the LAPSUS$ leader began late last year after he purchased a website called Doxbin, a long-running and highly toxic online community that is used to “dox” or post deeply personal information on people.
Based on the feedback posted by Doxbin members, White was not a particularly attentive administrator. Longtime members soon took to harassing him about various components of the site falling into disrepair. That pestering eventually prompted White to sell Doxbin back to its previous owner at a considerable loss. But before doing so, White leaked the Doxbin user database.
White’s leak triggered a swift counterpunch from Doxbin’s staff, which naturally responded by posting on White perhaps the most thorough dox the forum had ever produced.
KrebsOnSecurity recently interviewed the past and current owner of the Doxbin — an established hacker who goes by the handle “KT.” According to KT, it is becoming more common for hackers to use EDRs for stalking, hacking, harassing and publicly humiliating others.
KT shared several recent examples of fraudulent EDRs obtained by hackers who bragged about their success with the method.
“Terroristic threats with a valid reason to believe somebody’s life is in danger is usually the go-to,” KT said, referring to the most common attestation that accompanies a fake EDR.
One of the phony EDRs shared by KT targeted an 18-year-old from Indiana, and was sent to the social media platform Discord earlier this year. The document requested the Internet address history of Discord accounts tied to a specific phone number used by the target. Discord complied with the request.
“Discord replies to EDRs in 30 minutes to one hour with the provided information,” KT claimed.
Asked about the validity of the unauthorized EDR shared by KT, Discord said the request came from a legitimate law enforcement account that was later determined to have been compromised.
“We can confirm that Discord received requests from a legitimate law enforcement domain and complied with the requests in accordance with our policies,” Discord said in a written statement. “We verify these requests by checking that they come from a genuine source, and did so in this instance. While our verification process confirmed that the law enforcement account itself was legitimate, we later learned that it had been compromised by a malicious actor. We have since conducted an investigation into this illegal activity and notified law enforcement about the compromised email account.”
KT said fake EDRs don’t have to come from police departments based in the United States, and that some people in the community of those sending fake EDRs are hacking into police department emails by first compromising the agency’s website. From there, they can drop a backdoor “shell” on the server to secure permanent access, and then create new email accounts within the hacked organization.
In other cases, KT said, hackers will try to guess the passwords of police department email systems. In these attacks, the hackers will identify email addresses associated with law enforcement personnel, and then attempt to authenticate using passwords those individuals have used at other websites that have been breached previously.
“A lot of governments overseas are using WordPress, and I know a kid on Telegram who has multiple shells on gov sites,” KT said. “It’s near impossible to get U.S. dot-govs nowadays, although I’ve seen a few people with it. Most govs use [Microsoft] Outlook, so it’s more difficult because theres usually some sort of multi-factor authentication. But not all have it.”
According to KT, Everlynn and White recently had a falling out, with White paying KT to publish a dox on Everlynn and to keep it pinned to the site’s home page. That dox states that Everlynn is a 15-year-old from the United Kingdom who has used a variety of monikers over the past year alone, including “Miku” and “Anitsu.”
KT said Everlynn’s dox is accurate, and that the youth has been arrested multiple times for issuing fake EDRs. But KT said each time Everlynn gets released from police custody, they go right back to committing the same cybercrimes.
“Anitsu (Miku, Everlynn), an old staff member of Doxbin, was arrested probably 4-5 months ago for jacking government emails used for EDR’ing,” KT said. “White and him are not friends anymore though. White paid me a few weeks ago to pin his dox on Doxbin. Also, White had planned to use EDRs against me, due to a bet we had planned; dox for dox, winner gets 1 coin.”
A FUNDAMENTALLY UNFIXABLE PROBLEM?
Nicholas Weaver, a security specialist and lecturer at the University of California, Berkeley, said one big challenge to combating fraudulent EDRs is that there is fundamentally no notion of global online identity.
“The only way to clean it up would be to have the FBI act as the sole identity provider for all state and local law enforcement,” Weaver said. “But even that won’t necessarily work because how does the FBI vet in real time that some request is really from some podunk police department?”
It’s not clear that the FBI would be willing or able to take on such a task. In November 2021, KrebsOnSecurity broke the news that hackers sent a fake email alert to thousands of state and local law enforcement entities through the FBI’s Law Enforcement Enterprise Portal (LEEP). In that attack, the intruders abused a fairly basic and dangerous coding error on the website, and the fake emails all came from a real fbi.gov address.

The phony message sent in November 2021 via the FBI’s email system.
KrebsOnSecurity asked the FBI whether it had any indication that its own systems were used for unauthorized EDRs. The FBI declined to answer that question, but confirmed it was aware of different schemes involving phony EDRs targeting both the public and the agency’s private sector partners.
“We take these reports seriously and vigorously pursue them,” reads a written statement shared by the FBI. “Visit this page for tips and resources to verify the information you are receiving. If you believe you are a victim of an emergency data request scheme, please report to www.ic3.gov or contact your local FBI field office.”
Rasch said while service providers need more rigorous vetting mechanisms for all types of legal requests, getting better at spotting unauthorized EDRs would require these companies to somehow know and validate the names of every police officer in the United States.
“One of the problems you have is there’s no validated master list of people who are authorized to make that demand,” Rasch said. “And that list is going to change all the time. But even then, the entire system is only as secure as the least secure individual police officer email account.”
The idea of impersonating law enforcement officers to obtain information typically only available via search warrant or subpoena is hardly new. A fictionalized example appeared in the second season of the hit television show Mr. Robot, wherein the main character Elliot pretends to be a police officer to obtain location data in real time from a cellular phone company.
Weaver said what probably keeps fraudulent EDRs from being more common is that most people in the criminal hacking community perceive it as too risky. This is supported by the responses in discussion threads across multiple hacking forums where members sought out someone to perform an EDR on their behalf.
“It’s highly risky if you get caught,” Weaver said. “But doing this is not a matter of skill. It’s one of will. It’s a fundamentally unfixable problem without completely redoing how we think about identity on the Internet on a national scale.”
The current situation with fraudulent EDRs illustrates the dangers of relying solely on email to process legal requests for highly sensitive subscriber data. In July 2021, a bipartisan group of U.S. senators introduced new legislation to combat the growing use of counterfeit court orders by scammers and criminals. The bill calls for funding for state and tribal courts to adopt widely available digital signature technology that meets standards developed by the National Institute of Standards and Technology.
“Forged court orders, usually involving copy-and-pasted signatures of judges, have been used to authorize illegal wiretaps and fraudulently take down legitimate reviews and websites by those seeking to conceal negative information and past crimes,” the lawmakers said in a statement introducing their bill.
The Digital Authenticity for Court Orders Act would require federal, state and tribal courts to use a digital signature for orders authorizing surveillance, domain seizures and removal of online content.