Two CISO insights about obtaining certifications in the information security industry – a guest post by Rachel Arnold
Obtaining certifications in Information Security is one of the many ways professionals are choosing to use their time wisely these days. SecureNation asked some of our favorite Tulsa, Oklahoma CISOs (Chief Information Security Officers) about their experiences as information technology and security professionals. Jonathan Kimmitt, serves as CISO at the University of Tulsa as well as a member of the local ISSA board where Pedro Serrano serves as ISSA Oklahoma Chapter President and is the CISO at the Grand River Dam Authority. Both are very passionate about their roles not only professionally but also as leaders.

“It matters![That] may sound canned or out of a self-deployment book, but the real meaning is you are making an impact on the day to day activities of the company.”-Pedro Serrano, Grand River Dam Authority CISO
We had the pleasure of meeting these gentlemen last year and find their insights invaluable here at SecureNation. They mold who we are and what we do within the Information Security Community.
How did you connect with one another professionally?
Pedro: After being in Oklahoma City for 15 years we moved to Tulsa and I meet Jonathan when I was the IT chair for one of the local universities. It’s been 10 years since then and Jonathan and I have been involved in the local Information System Security Association (ISSA) group where I serve as the president and he is the communication officer.
Jonathan: The first time I met Pedro was at the very first BSides Oklahoma many years ago. I remember I stopped by his presentation and one of my work colleagues was there, so I sat down to talk. This colleague knew Pedro because they taught together at a college here in Tulsa. So, stories were shared, and my respect for Pedro grew.
Pedro and I crossed paths again at the local ISSA meetings. After a few months of meetings, he asked me to join the ISSA Board. Since then we have done presentations together, hosted events together, and generally became close colleagues in IT Security. He is a great sounding board and can always make me feel better when it has been a rough day at work.
Tell us a little about your journey, how did you each come to be passionate about security and privacy?
Pedro: My background is military communications, 20 years serving in the Air Force installing, upgrading and managing infrastructure as well as ground network systems. It [Information security] matters because you matter. There is great personal fulfillment in truly moving knowledge forward for all things cyber.
Jonathan: In the early 2000’s, after college, I had been offered a temporary position as Help Desk Supervisor at the University of Tulsa. The previous supervisor had quit, and they were needing someone to cover until a search committee could find a replacement. After a few months, they offered me the position full time. After a year or two, IT Security was becoming more popular in higher education. The university did not have a CISO, and probably didn’t even know what a CISO was at the time, but they knew they needed volunteers to be part of a security team.
How did you gain the knowledge you would need for that new role?
Jonathan: There was a system administrator from one of the colleges that was leading the team, so we did a lot of investigations, training, and incidents together. He was the one that started me down the CISSP(Certified Information Systems Security Professional) path originally.
Jonathan is currently one of the first in the industry to obtain the Certified Data Privacy Solutions Engineer certification launched earlier this year by ISACA. He has over 10 certifications combined from IAPP, (ISC)2, GIAC, and more, to name a few.
After a few years, he [system administrator] decided to take a position outside the University, so I was asked to take leadership of the CSRT. I ran the team for many years, dealing with all kinds of investigations and incidents on campus. Around 2013-2014, I was the only member of the CSRT, as everyone else had moved on or quit the team. This was the same time we had gotten a new CIO in IT, and one of his objectives was to create a formal IT Security department. Since I had been part of or managing the CSRT for 12+ years, they offered the additional title of Chief Information Security Officer and a new position for a security analyst. Unfortunately, this was alongside my role as Chief Services Officer. Within 2 years, the needs of IT Security had grown significantly, investigations and incidents had exploded. So, the university transitioned the Help Desk Services responsibilities over to another officer, and my role became solely CISO.
There must have been challenges, what were they and what resources did you rely on?
Jonathan: As a newly formed CISO, one of my first duties was to determine what we needed in terms of security, and start building resources. Before I came to the university, I was in law enforcement for a short time, so the idea of protecting people was always at the forefront of my mind. Not having a specific starting point for security at the university, I started looking at the safety of our people and working out from there. While I did not know it at the time, this was effectively building privacy concepts into the security foundation. To this day, my primary goal in security is about protecting people.
Not only is Jonathan viewed as an expert among his colleagues, but he also has experience providing IT Security expert testimony and evidence in criminal and civil proceedings.
Additionally, but quite separately, PCI (Payment Card Industry Data Security Standard) had become an issue on campus, and I was volunteered to be the PCI coordinator, mostly due to nobody else wanting to do it. I am quite grateful because learning the PCI-DSS allowed me to use it as the framework for IT Security on campus. To this day, I use the 12 requirements of PCI-DSS for anybody that needs to start an IT Security Program in their own organization.
After attaining PCI-compliance that first year, and enjoying the process of working with the auditors, the university leadership added GLBA (Gramm-Leach-Bliley Act), GDPR (General Data Protection Regulation), some FERPA(Family Educational Rights and Privacy Act), some HIPAA(Health Insurance Portability and Accountability), and a few others to my compliance list. I quickly found that a strong foundation of security concepts would meet many of the compliance requirements. Each time a new compliance was added, I was able to strengthen our security stance a little bit more, overall helping protect more people on campus.
I like formal frameworks for learning new things or skillsets. While I agree that at times it is appropriate for many of us to ‘google it’ and figure stuff out, I think that process can limit people in what they learn. A formal framework may let people learn about things that may not be needed right now, but in the future, they will remember and know where to look for more information.
What would you say to those that do not see the value of obtaining certifications?
Jonathan: I think that everyone has a different way of doing things. This process has worked for me. It has also worked for many people that I have helped along in their careers.
Training and certification are my preferred method. I enjoy the time and effort that I put in, and the value it has given me over the years. My plan is to continue with that process.
I recommend that everyone finds their best method that meets their requirements. I also recommend, that people at least try (and be successful) at different methods before they decide which one is NOT for them. I equate to my daughter not liking mustard when she has never tried it. How do you know there is not value when you have never been successful at it?
Pedro: For me, it’s the ability to show that you are teachable. In my mind, it takes effort to pass a certification and it means that you have to study and apply yourself. In information security, if you are not learning constantly you WILL be behind!
What advice would you give to incoming security professionals and current security professionals about which certifications to pursue as a part of continuing education and building skillsets?
Jonathan: My personal belief is that in the beginning, you should start with a generalized training & certification such as Security + or SANS SEC401. This will give you a wide view of different aspects of IT Security. People say it is a mile wide and an inch deep.
Then based on your job or your interest, you should begin deepening your knowledge and skillsets in the areas that make sense. If you are interested in the pentesting/vulnerability assessment side, then CEH( Certified Ethical Hacker), GPEN(GIAC Certified Penetration Tester), and OSCP(Offensive Security Certified Professional) may be your path. If you are interested in engineering secure systems, then working on your Microsoft or CISCO engineer certs may be more appropriate. If you are working in compliance, then maybe HIPAA and PCI certifications might be a good idea.
I am a huge supporter of constantly learning. I personally spend upwards of 8 hours a week on training, podcast, webinars, etc. I feel like if you are not learning in Security or Privacy that you are falling behind. With trying to absorb that much information, for myself, it’s important to have goals and frameworks to help me keep things organized.
Pedro: Start where you are today. Here is my thinking- I would pursue the CompTIA Security + certification. It’s very generic and it exposes you to all the domains in security. You want to be comfortable and happy with what you do, there are so many ramifications of security that you can specialize in and be very successful.
Together, we are exploring community voices through meaningful conversations about all things information security. We look forward to following Pedro, Jonathan, and other security professionals on their journeys. People make the process and technology can help make it possible here at SecureNation.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
![]()

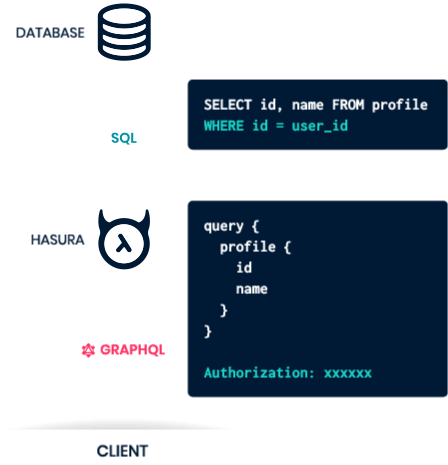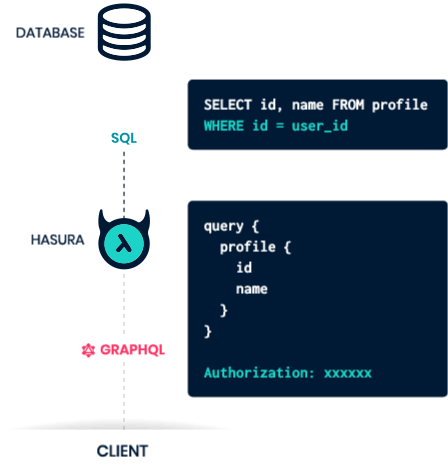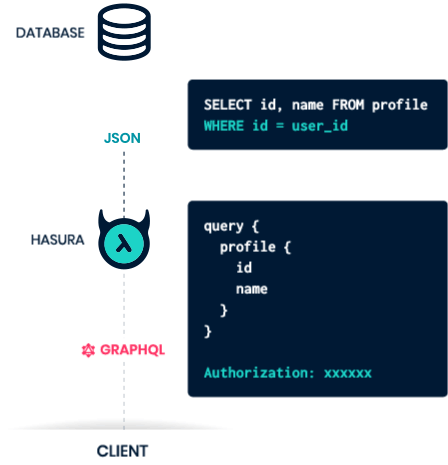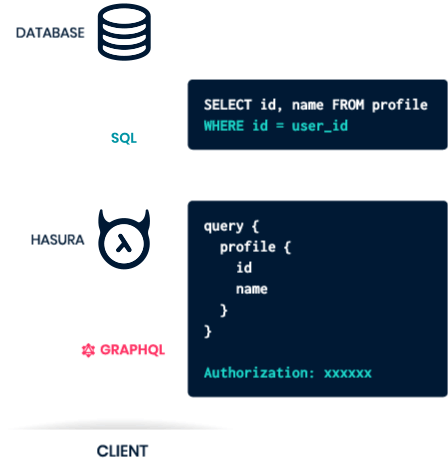







 On June 16, authorities in Michigan arrested 29-year-old Justin Sean Johnson in connection with a 43-count indictment on charges of conspiracy, wire fraud and aggravated identity theft.
On June 16, authorities in Michigan arrested 29-year-old Justin Sean Johnson in connection with a 43-count indictment on charges of conspiracy, wire fraud and aggravated identity theft.
