The Good, the Bad and the Ugly in Cybersecurity – Week 51
The Good
The latest dose of justice in the cyber threat landscape: U.S. authorities this week seized 48 internet domains selling “booter” and “stresser” services used by low-level hackers to launch powerful Distributed Denial of Service (DDoS) attacks. The DOJ has charged six individuals with computer crimes for their alleged relations to these services.
DDoS attacks are designed to overwhelm websites with fake traffic until the intended target, ranging from individuals and websites to entire network providers, is eventually rendered offline. According to the DOJ, the services in this action reportedly attacked victims in both the U.S. and abroad, including government agencies, educational institutions, gaming platforms, and millions of individual users.
In a sly effort to offload legal ramifications, the booter websites had attempted to hide behind lengthy terms and conditions which required customers to agree that services would only be used for network stress-testing purposes. The DOJ, however, has dismissed those claims using communications between site administrators and their customers as evidence of their intended malicious use.
Cybercrime-as-a-Service models have multiplied in the threatscape resulting in the number of DDoS attacks climbing in recent years. Booter services especially have created a low barrier to entry to cybercrime. The seized domains allowed purchasers to choose the volume of fake traffic to be sent as well as the number and duration of synchronized attacks that follow. Such services give non-technical users the ability to bombard essential services and critical infrastructure, draining their victims of time and money, as well as causing reputational harm.
Law enforcement have responded with Operation PowerOff; an ongoing coordination between internal agencies to dismantle DDoS-for-hire administrators and users. The takedown this week preempts a new wave of DDoS attacks as cyber criminals often favor the holiday season to launch.
The Bad
Notorious LockBit ransomware group has claimed a cyberattack on the California Department of Finance this week. While LockBit’s leak site posits that they made away with several gigabytes’ worth of confidential data, databases, and both financial and IT documents, California Office of Emergency Services (Cal OES) only confirmed the security intrusion and stated that “no state funds have been compromised”. Officials have given no further specifics except that state and federal security partners are working with threat hunting experts to continue the investigation.
The cyberattack on the Californian finance sector follows the DOJ’s recent arrest of accused LockBit threat actor, Mikhail Vasiliev. The Russian-Canadian’s capture from just last month was the result of a two-year FBI investigation into LockBit’s operations and related ransomware attacks on the U.S. and organizations across several other countries.
LockBit has been described by the DOJ as “one of the most active and destructive ransomware variants in the world.” LockBit associates have, since their first appearance in early 2020, extracted tens of millions of dollars from at least 1000 victims in various countries.
#LockBit has listed the State of California’s Finance Department. It should be noted that not all of LockBit’s past claims have been true. 1/2 #ransomware pic.twitter.com/jmf5ap15xz
— Brett Callow (@BrettCallow) December 12, 2022
Though LockBit’s claim of this week’s attack on the State of California was reportedly accompanied by screenshots of stolen files and a file directory, the ransomware group has been known to fake breaches.
Back in June, LockBit’s claims to have breached cybersecurity firm Mandiant were dismissed after the firm’s internal investigation found no evidence of breach or LockBit ransomware. What is now widely understood to be a PR stunt by LockBit shows that ransomware operators are going to extensive lengths to support their criminal operations, even using public relation plays to adapt and persist in an evolving threat landscape.
The Ugly
PyPI and NPM code repositories are under active attack by malware. This week, software supply chain firm Phylum reported a campaign targeting Python and JavaScript developers after it identified several suspicious Python requests packages. Through the use of fake modules and typosquatting, the campaign is luring victims into downloading malicious pieces of code. PyPI is a prominent code repository for Python programming language hosting over 350,000 software packages while its JavaScript counterpart, NPM, is the hub for more than one million such packages.
The cyber criminals behind the campaign have been reported to leverage typosquatting, a technique that involves delivering malware from files that have been named very similarly to legitimate pieces of code. So far, the typosquatted Python packages are:
dequests, fequests, gequests, rdquests, reauests, reduests, reeuests, reqhests, reqkests, requesfs, requesta, requeste, requestw, requfsts, resuests, rewuests, rfquests, rrquests, rwquests, telnservrr, and tequests
Typosquatted JavaScript modules in NPM have been identified as:
discordallintsbot, discordselfbot16, discord-all-intents-bot, discors.jd, discord-selfbot-v13, discord-all-intents-default, telnservrr.
The typosquatting used in the campaign leads to packages embedded with Golang binaries detected as malware. Once unsuspecting developers execute the binaries, the malware encrypts files in the background, and updates the device’s desktop background with an image impersonating the CIA that instructs the victim to pay for a decryption key.
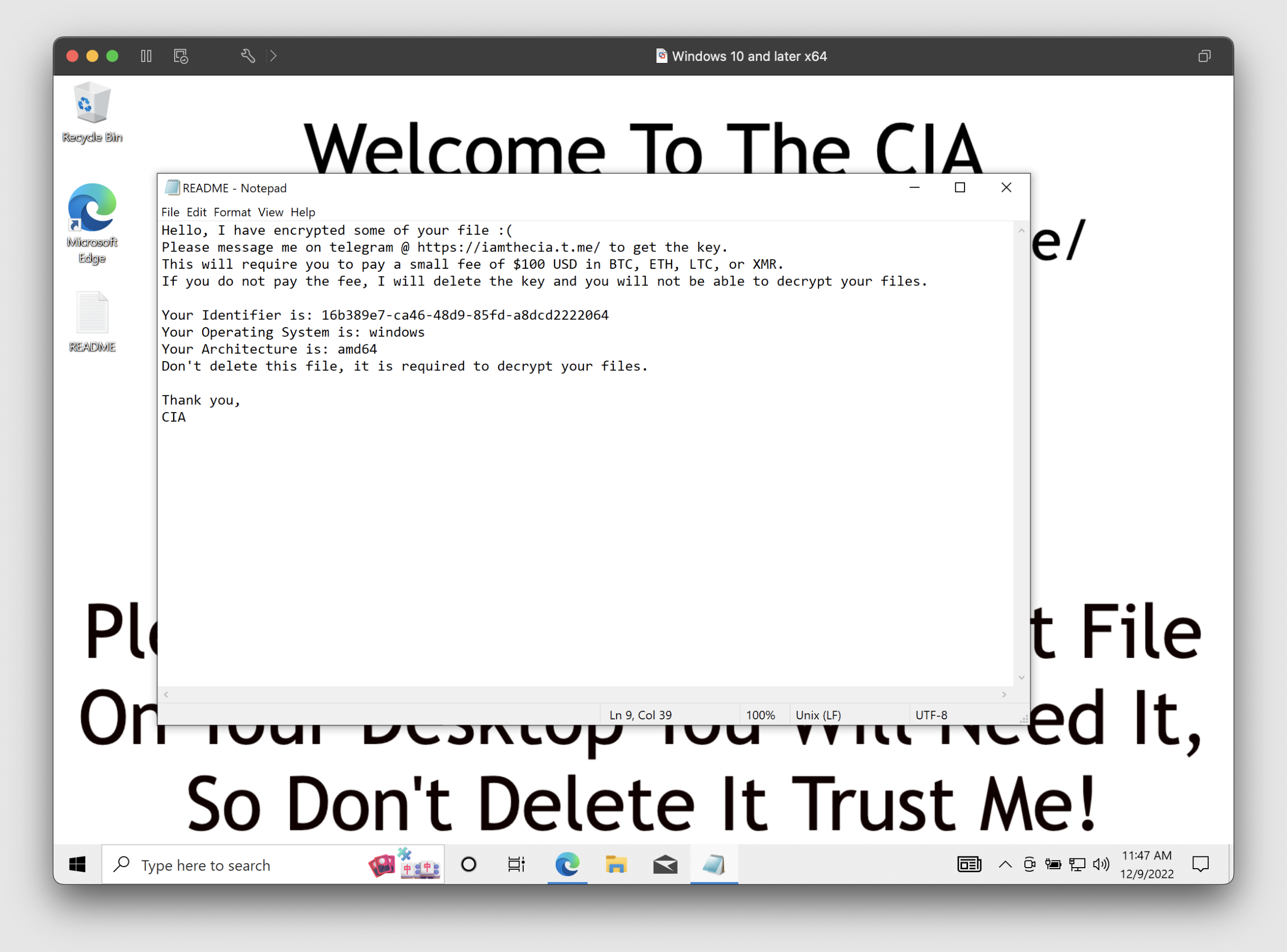
Phylum notes that attacks have continued throughout this week and that a newer version of the attacker’s ransomware has been released since the initial discovery. This attack on PyPI and NPM is the latest in a string of software supply chain attacks this year and is a trend that is likely to continue into 2023.



Leave a Reply
Want to join the discussion?Feel free to contribute!