Darknet Diaries | 60: dawgyg | How “dawgyg” made over $100,000 in a single day, from hacking was automatically transcribed by Sonix with the latest audio-to-text algorithms. This transcript may contain errors. Sonix is the best audio automated transcription service in 2020. Our automated transcription algorithms works with many of the popular audio file formats.
A quick warning right here at the beginning, this episode does contain some swear words and some bad language, if that’s an issue for you. Well, maybe skip this one.
Hey, it’s Jack. Host of the show. One of the reasons I like making this show is to smash the stereotype of what a hacker looks like. Today’s guest definitely does that.
I don’t know. I’m trying to see. Understand. Get a picture of your vibe here. You’re almost like you almost look like Eminem a little. Not quite. But, you know. Yeah. Yeah. What do you call what would you characterize yourself?
Well, I actually used to take a lot of pride in the fact that I don’t work like the average hacker. I guess what you what most people would say I was was. Do you remember the term wigger? W. H.I.G. are white guys that dressed like black guys. Listen to rap music and stuff like that. My first time in prison. And up until that point, I guess that’s technically what most people would seem. Yes, like I wear baggy clothes, sagging pants, backwards hat and everything like that. I got tattooed pain as well from a roll song on the back of my head. I got the laugh now cry later faces.
These are tattoos he got while in prison.
So my right bicep, I put a little tribal looking face that was smiling and it said, laugh now.
And then on my left side, I had a face that was crying. And it said, Cry later. Federal prison in federal prison. We all have prison numbers. And the last three digits of your numbers show where you were arrested. And my number was 3 8 1 4 1 dash 0 8 3 0 8 3 is the Eastern District of Virginia.
This is Doug.
And his story perplexes me because of stuff he says like October 18th, two thousand eighteen, I was paid a hundred and sixty thousand dollars in that one day.
So what did you do to make one hundred and sixty thousand dollars in one day? Well, he’s a hacker.
These are true stories from the dark side of the Internet.
I’m Jack Reciter. This is Darknet Diaries.
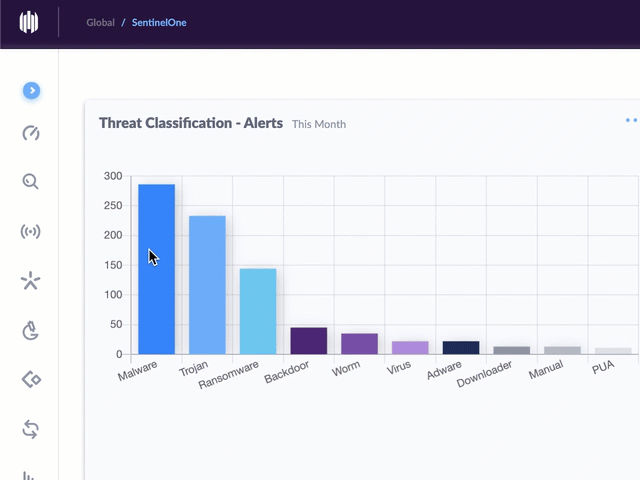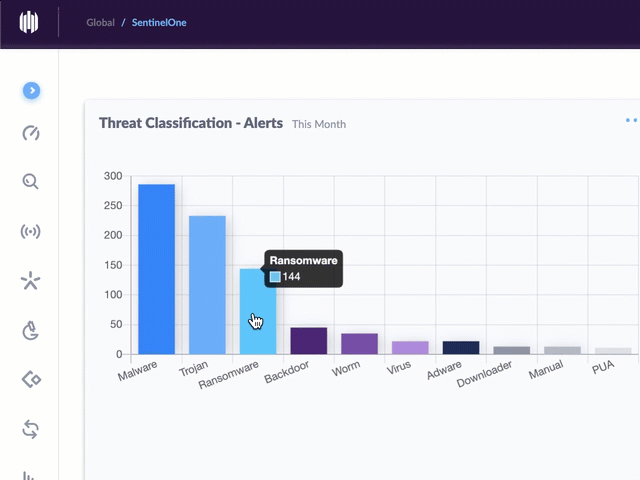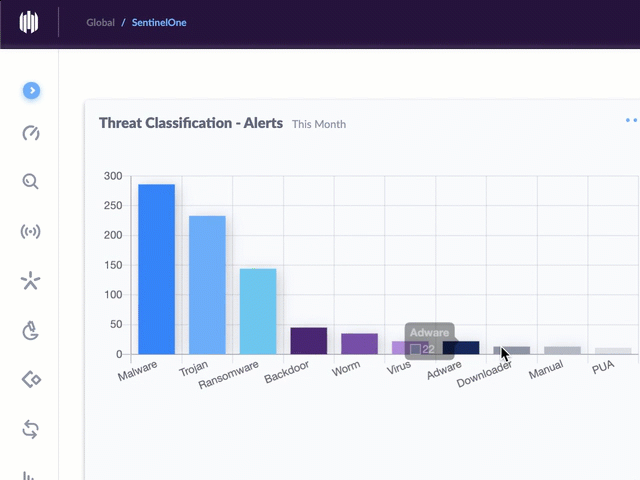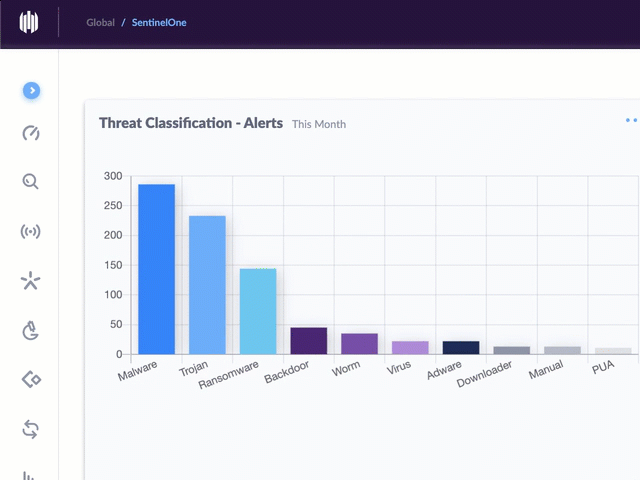
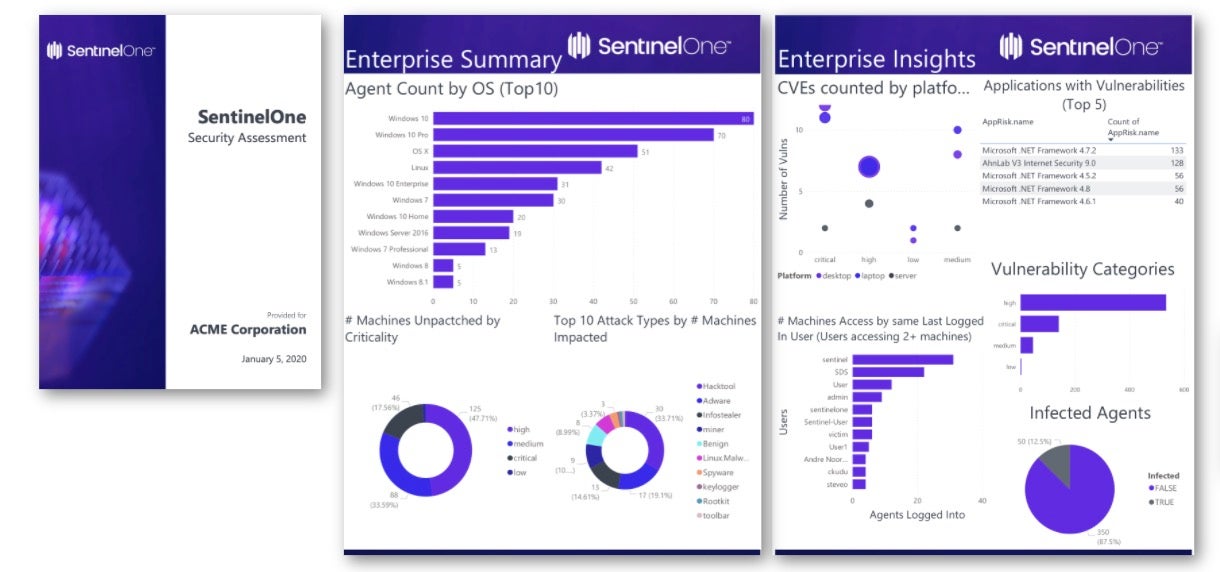
Support for this episode comes from SentinelOne. It’s all too common. A family member or colleague calls asking for help because some kind of ransomware has infected their computer. Bummer. Now imagine this on the scale of an entire organization. This is exactly what set in a one was built to prevent and solve. Besides the ability to prevent ransomware and even rollback ransomware if it is encrypted, Sentinel 1 also has a ransomware warrantee. Visibility in each of these endpoints is available from an easy to use console, allowing security teams to be more efficient without the need to hire more and more people on top of that. Certainly one offers threat hunting, visibility and remote administration tools to manage and protect any IAPT devices connected to your network with Sentinel One. You can replace many products with one if you’re a CSO, a security leader or I.T. manager in the enterprise. Don’t settle to live in the past. Get a personalized demo and a 30 day free trial that allows you to see the benefits up close and personal. Go to SentinelOne dot com slash darknet diaries for your free demo. Your Cyber Security Future starts today with SentinelOne.
So Duggie, his real name is Tommy de Vos. And like many hackers, his story starts out when he was a young boy in a chat room.
I actually joined the wrong chat room by mistake. It was just like somebody else’s private room, and it was run by a guy that used the alias Deez Nuts.
D.e. And UTC. But I just did this last joint pound Deasey by mistake and this brought him to a chat room full of hackers.
I kind of just hung out in there. I would just keep joining that same crew every day after school for a couple of weeks. So I started like asking him questions. They’re like, who the hell is this kid? Blah, blah, blah. And I got banned like several times.
There’s something magical about being in a chatroom as a teenager. They’re fun and addicting. And even though he was banned, he figured out ways to get back in.
Well, I would just disconnect, reconnect and then go back in again. And after going and spending. I don’t know. Several months of just keep going back in there repeatedly and asking just pretty much begging the guy to teach me stuff.
Because Tommy saw this chat room was full of hackers, people breaking into computers and networks that they weren’t supposed to. And Tommy thought this was cool. And he wanted to get in on the action, too. And he went to learn what these hackers were doing. And even though they kept banning him, he just kept finding a way back into the channel and was asking them to teach him how to hack. And eventually they gave in and threw him a bone.
And like the first thing that he told me was go to Yahoo! AltaVista. He was like, read everything that you can find about hacking.
I want to say this would have been happening in about 90 4ish. So actually, in 1994, Tommy would have only been 12 years old, a pre-teen still. Well, after bouncing in and out of all these chatrooms. He finally landed on a name. Duggie G is what he would be known as online, and that’s Doggy’s spelled DEA w.g. Y. And so he starts learning some basic hacking techniques by reading up on it. At that time, Frack was a free online hacking magazine, so he probably dove into that and started reading it from like the first issue and slowly going through it, reading every issue. And he learned a few things here and there, but he’s just twelve.
So he was just starting out and wasn’t very good. But he eventually joined an Irish Sea hacker crew called TDK.
Tdk was stood for those damn kids. The main focus of TDK was piracy EPP networks. We would build botnets to go and check every single out in our target room and find a server that didn’t have anybody from that server on it. That was an operator.
And then we would detox that server to split it off in the network and then date basically just take over the channel. Damn you. You’re the one. So there was so much back in the day. Yeah, I remember that.
I remember that because I was also hanging out in I.R.S. channels in nineteen ninety four. UNEF net the exact place where dog was trying to do server splits and take over the channels. I remember channels getting taken over by young kids, but at the time I thought it was kind of funny and didn’t really take these chat rooms too seriously. And when Tommy started calling himself Doug e.g. trying to take over these chat rooms, I think this is where he starts trying on his black hat. That is, he’s trying to conduct hacks that are causing destruction and grief. Maybe taking over a chat room isn’t illegal, but this would be the beginning of his lifelong hacking career. What led you up to getting suspended at high school?
So you used to get bored a lot. While I was taking a computer class or it was cute basic in school.
So a lot of times I’d get bored and it wouldn’t have anything to do because I would write my program for the class really fast and I would actually $d my school’s IP address to take our Internet down because then we couldn’t do class. So we get to go outside and play.
Yeah. He crashed the school’s internet because he would rather go outside and play.
Well, I actually got in trouble for doing that. They suspended me the first time. Three days for that.
That was his first suspension from high school, but it wasn’t his only one. Soon after that, he got suspended again.
I got expelled from school because I broke into a military base in Korea and use their computer systems. I hijacked the AOL account that the general of the base was using. And I sent an email from his email address, from his AOL account to the superintendent of Hanover County that one of the high schools in his county was going to blow up at 10:30 in the morning.
A convoluted scheme, but it was done for the same reasons as the first one. He just didn’t want to be in school.
He wanted to be able to skip school, go to the river, smoke weed and just have one for the day.
It worked. Sort of. School was canceled, but he didn’t get away with it.
I went to school the next day. There was a guy in a suit on each side of the door and they were like, you need to come with us.
I got expelled. So how did he get cut? Did that military base in Korea do some forensic investigation and traces back to a teenager in West Virginia? No.
Did the police track his online connections? No. Again. What happened is that he told someone that he’s the one who got school canceled that day and that person went and told someone at the school that Tommy is who sent in this bomb threat.
And because I had used the Internet to do it, the FBI ended up raiding my house about two weeks after it happened to take my computers. And that was the first time that I was charged with computer crimes. I was actually charged with violating the Computer Fraud and Abuse Act, being a minor, a sophomore, one of those damn kids in the eyes of the law.
This could get bad pretty quick. The feds took his computers, but let him go free. As they investigated the case, well, this gave him more time, more time to hack more stuff. He got a new computer and slipped on his blackhat again. But forget about TDK at this point. He was onto more ambitious adventures.
So I started talking to a bunch of other hacking groups and I came. I got in contact with a guy named Rotha who was a member of Rodolfo, and he was telling me about. They had rules for the group where you were only allowed to hack Unix systems.
You are allowed to target windows because windows was too easy and they like to only attack government, military and Fortune 500 companies.
This was great. Doug Gidgee liked everything about this. The rules, the people, the stuff he was learning.
So he started hacking with world of how so? Then in June of 2001, I defaced my first Web site as part of World. And it was actually the Virginia. I broke into the Virginia Department of Information Technology and defaced w w w dot state, dot V.A. dot us, which was our main state Web site. Just from that point on, I just was defacing stuff with Warnaco or nonstop for about six to nine months.
Oh, here’s your wondering defaces. Just a term used to change what’s written on a Web site so you can like swap the photo that’s on the front page as some mouse or just change what’s said there to whatever you want. In this case, he probably had to prove himself that he was the guy who hack this site. So he probably wrote something on there like Hacked by Duggie G or hacked by World of Hell or something like that. What were some of the sites that you knew that you were hitting or world of hell was hitting?
Yahoo! Dot com dot P.H., Nokia, dot com Sony.
Dot com Dotson’s Dunhill Epson Fujifilm it hacking is a drug. Mercedes Benz Duggie G was getting addicted world online. The car company AOL was loving.
This hacking in the world of hell hacker group HP.
But the problem with addiction’s is that you can overdose.
United Airlines, Casio, Motorola.
And you can fall into a world of pain.
One day, Sony Music, Toshiba, Opel, Volvo, E.A. Sports.
After the break, the party ends for doggie Rolex.
Pfizer oblige a Chinese government systems. The US Department of Energy. U.S. Court Systems.
Venezuelan military.
Working remotely can be a challenge, especially for teams that are new to it. How do you deal with your work environment being the same as home while staying connected and productive? And then there’s your newest co-worker, the cat. Well, your friends at Trello have been powering remote teams globally for almost a decade, at a time when teams must come together more than ever to solve big challenges. Trello is here to help Trello, part of that Larsons collaborative suite as an app with an easy to understand visual format, plus tons of features that make working with your team functional and just plain fun. Chelo keeps everyone organized and on the same page, helping teams communicate, focus and connect teams of all shapes and sizes at companies like Google, Fender, Costco and likely your favorite neighborhood coffee shop. All use Trello to collaborate and get work done. Try Trello for free and learn more at Trello dot com. That’s tr e l dot com. Trello dot com.
Creative Dot, Audi, Kenwood, Acer, Highschooler Doug e.g. was still hunched over his monitor, wearing a black hat and defacing Web site after Web site, Xerox, Packard Bell Compact, 3Com doing all he could before he turned 18, which was an adult in the eyes of the law.
So I turned 18 in November of 2001. I actually stopped hacking for a few weeks, but then I got bored again. So I started doing it again. I hacked consistently until June 12th of 2002.
In the year 2002, on June 11th that night, Milin Black 2 had just come out in theaters.
So that night before I went to bed, I downloaded Men in Black to plan was I was gonna go to work the next day and then I was gonna come home from work early, smoke weed with my sister.
Don’t bother calling the CIA.
Forget the FBI and we were gonna watch that movie.
He got out of work for the same reasons he wanted to get out of school so he could go play. In this case, to play an illegally downloaded movie. So he goes home to his apartment with his sister and they watch Men in Black 2.
But the real men in black were knocking on his door.
And I went to push the door open, but it was yanked open in front of me and an M-16 was in my face. So there is somewhere between 20 and 30 agents inside of my apartment. My sister was sitting on my couch crying. My dad was standing in the living room next to her. And just like when he saw me walk through the door, he just looked at me and shook his head. They took everything in the house that was related to computers are all floppy disk. Any C.D. that was in there, every computer, every computer component, every piece of paper that had notes handwritten on them.
And what was going on? I mean, what was your emotional level at that point where you like freaking out about this? So how how are you feeling?
I was I was scared shitless at the time because I was an adult at that point and I was on probation still for the hacking and voluntary two years before.
Once again, they took all his electronics and computers and he had two weeks before his court date.
This is it. I’m sorry. I’ve got two weeks of freedom. They’re going to lock me up in two weeks. So I was like, screw it. I’m just gonna have fun and do whatever.
So I spent two weeks racing, I used to street race a lot, so I spent two weeks street racing going to the beach about hanging out with as many of my friends as I could, trying to sleep with as many different girls as I could.
Now, 19 years old, black hat hacker Tommy Device Doggy stands in front of a judge two weeks later. Hats were not allowed in court.
I ended up pleading guilty in October of 2003 to one count of violating the CFA for breaking into a computer system that controls interstate commerce. I had broken into a Web site called Bank Coehlo B A in K C O L o dot com and deface the Web site. And turns out it was for the Colorado Bank and Trust Company.
Yeah, messing with a banking website was probably a bad move. I mean, they’re federally regulated and insured, which means that crimes involving a bank are probably going to be investigated by federal law enforcement.
The judge asked me to stand up and he looked at me and he said, Mr. Wells, I do not believe that you’re sorry for anything that you’ve done. I think the only reason that you are showing any remorse whatsoever is because of the fact that you got caught.
He ended up sentencing me to 27 months in federal prison.
Banning me from computers for 10 years.
And giving me five years of probation. And I want to say it was one hundred thousand dollars of restitution. So then after he pronounced my Senate, he said, I now place you in the custody of the U.S. Marshals to serve your sentence. A My knees pretty much gave out on me. I was just I walked in there expecting to walk back out that day for at least 30 days. And now all of a sudden, I’m.
Getting locked up for almost two and a half years.
The fun was over, Doggy’s hacking spree was done back to being Tommy with no had to wear in prison. What were some of the tattoos you got?
My first tattoos in prison. I got a tribal on each one of my biceps. One on each side. I was just small or tribal and one had a T for my initial and the other one had a C for the girl I was dating at the time. I got three dots on my right wrist, which is a Hispanic gang tattoo for Punto SOCOs crazy life. I had the words crazy life put on. I don’t know what it’s called. It’s not my forearms, but it’s like the back of my arms between my elbow and my risk.
Crazy was put on one side. Life was put on the other side. I went in with like five or six tattoo’s and came out with like twenty five or thirty total.
Tommy served his two years in prison and got out. And at this point is 2006. He’s 22, but still has to serve probation. So you your real probation had 10 years.
No computers, no computers, cell phones, game systems, fax machines, anything that could communicate with other people. Aside from an actual phone, I could make phone calls.
I wasn’t allowed to touch a cell phone or anything like that, even when I would go and get a job. A lot of jobs would have you clock in on a computer. I wasn’t allowed to do that. I had to have another co-worker call me in and out for the first 30 days or so. When I got out of prison the first time, I didn’t do any drugs and I didn’t get on a computer or anything for the first 30 days.
This doesn’t sound good, but let’s not forget Tommy was once addicted to hacking. It was all he could think about. Not to mention being high. So even though he went two years without doing any of this, how long could he hold out? Now that he’s sort of free again?
It turns out 30 days I actually started defacing websites again because of how my bedroom was set up in the house.
I used to sit at my computer and I was sitting next to a window that I could see out, but you couldn’t see into it. So I just would always sit there. And if I saw Coracle in my driveway that I didn’t recognize, I would jump up and take my desktop computer completely apart by different parts of it in various places of the house. So it couldn’t be found. And then go and answer the door.
His probation officer would visit sometimes, come by and check on Tommy, talk to him, look around his room and make sure he wasn’t using a computer because that wasn’t allowed on his probation. And one day when his probation officer did come by, Tommy quickly shut down the machine, took it all apart and hid it all over his room. But he forgot to hide one thing. And when the P.O. came into his room, he saw a keyboard on Tommy’s bed, busted. This was a violation of his probation.
He had to go back to prison to do more time. Eventually, he came back home again. Again, his probation was that he could not use computers. Tommy just couldn’t keep his fingers off them. He didn’t want to hack anymore, but he was just addicted to computers and would use it for other things. But the FBI was interested to see if he was going to go back to being a hacker.
The FBI actually watched me for six months. They rented the house across the street from mine, took pictures of every person that came to my house. The FBI actually collected our choice to go through it, looking for evidence that I was on a computer hacking again.
As Tommy tells the story, his parents wanted to sell the house and a couple of FBI agents came over posing as potential buyers of the house. And that’s when they saw Tommy on his computer, in his room. And this was a direct violation of his probation, again, which was all the evidence they needed. The FBI went and got their arrest warrant and came back and knocked on the door.
And when I opened it, they bust through the door. And it was the FBI, I guess, which is the defense criminal investigative service. It’s kind of like the Department of Defense Defense’s version of the FBI, the Secret Service and state police for Virginia.
And they locked me up for violating probation and failing drug test. They gave me 14 months in prison that time, which was the maximum they were allowed to give me. They gave me what they called diesel therapy. They put me in solitary confinement for three weeks in Petersburg. Then they shipped me from there to USP Atlanta, which is a maximum security prison in Atlanta, Georgia. They put me in solitary confinement.
Therefore, I want to say it was another three weeks. And then they sent me from there to a medium high prison in Williamsburg, South Carolina, where they put me in solitary one for a couple of weeks before putting me on the actual compound.
I think going back to prison again really did change, Tommy. He didn’t like it there. He didn’t want to ever come back. So I spent a long time waiting, which was worth more to him. The high you get from hacking or his freedom. Now, each time he went to court, he ended up in front of the same judge every time. And that judge’s name was Judge Payne.
And Judge Payne said something to him which had a lasting impact.
So the last time I was in court on October twenty eight of 2009, I had Judge Payne for every time I went to federal court, I had the same judge. And he told me that if he ever sees me in his courtroom again for a computer crime. He was gonna give me life in prison. Yeah, he made it. So I don’t know. I don’t want to hack it legally anymore. I got a daughter that would be really mad at me if I went to prison for the rest of my life.
So Tommy gets out of prison and does good on probation. No violations. In fact, he does all the time he’s supposed to do. And on November 3rd, 2010, his probation is done and he’s a free man once again.
It was really nice to know that I could on computers again and not like have to worry that I was gonna go to prison or get caught ornament or anything. I didn’t have to hide them anymore. I was allowed to get cell phones. And the biggest thing to me was the fact that I was allowed to go to school now while I was on probation. I wasn’t allowed to go to college because you can’t go through college without having to use a computer for something. Especially when I wanted to go through computer stuff and I was allowed to try to find a computer job at that point. So that was like the biggest difference for me.
He could go to college, use computers, but of course, he was not allowed to do any illegal hacking.
No matter how tempting it might be, finding a legit job in the tech industry is really hard when you have a federal conviction on your record, especially for fraud.
I spent three years from 2010 to 2013 trying to find a computer job period. I kept working as a cook and doing construction, but I couldn’t find any company that would hire me doing computers because of my background and everything. They automatically think you were stealing money or identities.
Tommy would sometimes get that itch to beat dog e.g. the black hat hack into something again, but he controlled his temptation’s no matter how strong they were. The truth was he was really good at hacking. When you’re really good at something, you like doing it. But then he heard about something new, something that would change his life and start a new chapter for him. Bug bounties.
There are two main Web sites that do this. Hacker 1 and bug crowd companies will go to these Web sites and say something like, hey, if anyone can find a security issue on our Web site, we’ll give them a reward. Tommy came across Hacker 1 and decided to check it out. He saw the Web site Yahoo! Had a bug bounty program and he was already really familiar with the way Yahoo! Work. He’d been poking at it and hacking on it throughout his whole teenage life. So he was kind of flabbergasted. Now that Yahoo! Was willing to pay anyone who could find a security problem in their Web site. So you start hacking around on their site and found something.
I reported my first bug on hacker one to Yahoo! In March of 2016. And I found that a lot of Yahoo! System admins and developers were using just to share information and they were forgetting to make them private or delete them after the fact. So I found a bunch of them that were leaking like internal passwords, database credentials on network maps and stuff like that.
So that was my first blog. Yahoo! Reported it to them and they gave me like three hundred bucks for as in Yahoo!
Was thinking, Tommy, for hacking their site and telling them about a security problem they had. And we’re so happy they gave him three hundred dollars for this.
So I was like, oh, shit. So maybe this is real. I made very little money in the first couple of months because it was all like really low level things that I was finding. And then in May of 2016, image, tragic image, magic, remote code, execution, vulnerability was published at that time.
The image magic bug was a vulnerability where Web sites let you upload an image, but you could send a malicious image to it and then you can get access to the Web site just by uploading a malicious image.
And I actually got remote code execution on two of Yahoo! Servers using that and got the first one was a thousand dollar bounty. And then the following week I found the same RC on a different server, reported that they gave me the full four thousand dollars.
And with that, Duggie was back, this time completely legal, this time waving a white hat because all this was legit and paid up by Yahoo! The company he hacked. But because they have a bug bunny program, it explicitly allows this kind of hack if you’re participating in the program and they’ll pay you for it. So he was basically given the green light to hack once again. Doggie G was in somewhat disbelief. Is this even real? But it was. So he sat up straight, cracked his knuckles, and began going to town looking for more bugs that would pay out.
So in my first year, doing bug bounties in 2016, I think I only made him say somewhere between like thirty and fifty thousand dollars somewhere. Almost all of it was on hacker one. And then in 2017, I had me. I ended up making like I set the goal to make a hundred thousand dollars in 2017 from bugs bounties and made somewhere between one hundred and fifteen two hundred thousand dollars for 2017.
The white hat hacker move was working for him, but what looked even better? What he really wanted was a green hat. Green as in money.
Two thousand eighteen. I think I made combined across all three platforms somewhere between six and seven hundred thousand dollars for Duggie G.
Money looked best when it was turned into cars. Men in Black 2 got him in real trouble, but Fast and Furious truly inspired him.
So the Fast and Furious movies started coming out. What was it like? Ninety nine or so and fell in love with the skyline?
Rs So tell me about what happened to you in January 2018 and January 2018.
I got one hundred and seventy five dollar bounty on a Friday afternoon on a hacker one program and I was kind of mad about the bounty because it should have been quite a bit more. But the program paid really bad and I put one hundred and seventy five dollars on a bet on basketball, international basketball a lot. But that seventy five dollars on there at about seven o’clock on that Friday night. And by Monday afternoon, 4:00 or 5:00 in the afternoon, I turned one hundred and seventy five dollars into one hundred and thirty three thousand dollars.
So I went through like fifty thousand of it and I went and bought my first skyline.
It was a nineteen ninety two or thirty to PTSD.
Right. That was technically my dream car. It was at the GCR model, but it was still at Skylight. So I was like extremely happy.
In 2018, Dog kept finding and submitting bugs on hacker one two hundred dollars here, one thousand dollars, they’re five thousand dollars there. He was racking up one bounty after another. Slowly but surely fattening his stack, earning his green hat. And then he scored the biggest bounty yet again.
So October 2018, I set the record for the most the highest amount of bounties paid in a single day to a single researcher. I was playing with the Sara and I found a bypass for their blacklist that they had used. And I ended up being able to bypass the blacklist in a total of fifteen or sixteen different endpoints. caressa. Sara.
I know some of you don’t understand what he’s saying. That’s OK. All you need to know is that he found a vulnerability 16 times on a single company’s Web site and ended up getting new bugs for all 16 of them.
And each one of them was ten thousand dollars.
So it was like October 18th or something like that. Two thousand eighteen. I was paid one hundred and sixty thousand dollars worth of bounties in that one day.
What is that feeling like to get one hundred and sixty thousand in a day’s work?
Unreal. It was just like it still seems too good to be true. That’s my sealed day. Highest payout, but I’ve had at least five or six single days where I’ve made six figures in one day. Ask any race in any real race.
It don’t matter. You win by an entire on my winnings winning.
It’s unreal to know that 10 years ago. Right now I was sitting in federal prison. Now I am one of six people on hacker one that have made a million dollars just on the hacker one platform.
I’m pretty sure I’ve made over eight hundred thousand dollars in 2019 just from Hacker.
I’ve confirmed all this, by the way. I’ve read through his court cases. I’ve listened to his mother talk and Hacker One themselves has announced that Tommy was the sixth hacker on their site to make one million dollars. And in 2019, he made nine hundred and ten thousand dollars total just missing his goal of 1 million dollars in bug bounties in one year. What did your parents think when you started using Hacker One to hack again?
At first they were super leery of it.
After, like, my mom finally accepted it. Actor Like the first year or so when she saw it, I was able to make money and I was making decent money and not get in trouble. My dad still doesn’t accept it. He actually won’t talk to me because he thinks that I’m wasting my life and wants me to get a normal 9 to 5 job and everything.
And last time I actually spoke to him was in February of this year and he was disowning me and telling me that I needed to stop wasting my life and get a real job before I lose my life or something along those lines.
And that’s because he thinks this isn’t legit work.
Yeah.
I’m hoping that he’s seeing it now. In the last in 2018, I’ve bought cars for my two nieces that are 17 years old, about both of them, their first car. I bought my baby sister, who is about to turn 18. I bought her her first car.
I bought my one. But I’ve got a set of twin sisters a year younger than me. One of them lives in port. I bought her a truck earlier this year. I bought her twin sister a car and a truck a few months ago. I bought my mom a Mustang back in October of this year, and I bought myself this year. I bought my cell phone, Infiniti, g37. I’m planning to buy my dad a brand new truck. I’m planning on buying him a truck within the next month or two and then just buying it, taken it to his house, put it in his driveway with the keys and the title and just leave it there and let them come home from work to find a brand new truck in his driveway for.
There’s an update here. I recorded this interview like months ago, but I check with Tommy just before airing this and he’s slowly getting on talking terms with his dad again. And when he pitched this idea to him, his dad had another plan. Remember the car Tommy bought his 18 year old little sister? Well, she didn’t drive it right. And she blew the engine. So Dad said, instead of buying me in your truck, why don’t you buy another new car for your little sister? So that’s what Tommy’s planning on doing. And also, at this point, Doug has earned so much money that he’s been able to buy two of his dream cars. And both of them are the classic Nissan Skylines from 2 Fast 2 Furious. What did the license plates on your cars?
On my home r32 GST.
I’ve got an antique tag on it that says Hacker H4 S.K. 3 are on my 92 r32 GCR. It says Baladi, please. And then I have on my Infiniti g37. I have the license plate. Thank you. Hacker 1. Earlier this year, I actually a couple of months ago, I actually was sent to D.C. by hacker one and I spoke at a little cyber security leaders meet up between the government and government military agencies. So going from a black hat, being sent to prison for hacking the government to actually being invited to speak to government leaders about my experience hacking them.
This is the weird new future we’re living in. Ten years ago, when Duggie G was hacking, bug bounties didn’t exist and the government was chasing him. Now Douggie is doing the same kind of hacking, but now companies are paying him to do it and the government is asking him to come teach them. Sort of like if he can’t beat them, join them.
Yeah, exactly. And the good thing, one of the things that I love about the D.O.D program so much is that it’s their scope. Tons of companies start up a bug bounty program and they have an extremely limited, limited scope.
And it’s like we only want information about these and everything. And as a former blackhat, I know that I don’t give two shits about a scope if I’m a black cat.
So yeah, Tom is now helping the feds secure their networks. It’s weird how it all turned out, isn’t it? And even though the bug bounties are bringing him a great income, he’s actually been looking for a day job lately.
I don’t have anybody to talk to that when I make a really cool hack or anything like that.
Aside from the people online, I see hacking as kind of an addiction. I’m just as much addicted to hacking as I ever was addicted to any drug or anything like that. I’ll never stop hacking. They’re actually the only reason I’m looking for a full time job is because I miss working with the team.
I just want to have a little bit of structure to my day so that I’m not just like I sit around bored out of my mind a lot and there’s only so much X-Box you can play and all online games and stuff you can play before even they get boring.
Tommy did in fact recently get a job with one of the biggest banks in the US doing research on the threats they see there. He applied, interviewed, they liked him, he passed, got the job and he had a start date in January. But when they ran a background check on him, they got worried and so they decided not to bring him on board. And this was a bummer, since another reason he wants a day job is to prove to his dad that he’s doing good work.
I think you’ll be happier then. I’ll still be doing my book, bounties and stuff, but I’ll have what he sees in his eye as a real job.
Ok. So if Tommy’s story is inspiring to you, you can get started earning money, finding bugs, too.
And this is what Tommy suggests you do to get started just doing hacker one to one dot com, which is kind of like Hacker University where it’s capture the flags and stuff to show you some real world examples of things that bug hunters are bound to give you a hands on experience doing pen tester labs. I always suggest when somebody ask me where to start is reading every blog post you can find from all corners about what they found and everything. So it gives you an idea.
Last thing I asked Tommy, former criminal, is if he has any advice for the next generation who might be thinking of trying on that black hat?
A It’s not worth doing the stuff illegally. Thanks to Edward Snowden’s leaks back in 2013, we know that everything we do online is monitored by the US government and anybody that thinks that they can do things illegally and get away with it is mistaken. Anybody that has been doing things illegally and has gotten away with it, it’s it’s only because they haven’t wanted to look at you yet, but they can. You’re not gonna hide yourself completely. Everybody makes mistakes. And the amount of money that you can make doing this legally far outweighs the money you’re gonna make illegally. Because, I mean, if you’re good enough to do this as a black cat, you’re good enough to do this as a white and you can make Life-Changing money doing it.
Just before airing this episode, Tommy attended the H 1 4 1 5 hacking event. This is a nine hour hackathon put on by Hacker 1 in San Francisco. And the goal is to see how many bug bounties can be claimed within nine hours. A bunch of people showed up. Tommy went and he was finding bug after bug and reporting them. And within the nine hours given for the event, he earned one hundred and one thousand dollars, which gave him the coveted M V H most valuable hacker.
I get a little jealous listening to this story because I was one of those people who did everything right. I have never been arrested for hacking. I never went to prison. I went to university and got a computer science degree. And then I spent 10 years working as a security engineer. I mean, nothing close to a million dollars. Yet here is Tommy breaking all the rules and getting scarred again and again, failing repeatedly and still coming out, not just okay, but with all the toys. But I guess it just reminds me of that. Fast and Furious quote. You know, no.
One of the things everyone knows is not I stand by your side, your race.
A very big thank you to Tommy de Vos, a.k.a. Doggie G. Great story, but stay out of trouble. OK. Oh. Have you listened to the five bonus episodes of Ducted Diaries yet? They’re out there, but they’re only four pages on supporters. If this show brings you value, please consider giving to The Dark Knight Diaries Patriarch. You can also get an ad free version of the show there, too. The show is made by me, the Tokyo drifter Jack Reciter. This episode was produced by the turbo charged Jake Warga editing help. This episode by the windblown Damian and our theme music is by the electric powered brake master cylinder. And even though a Marai botnet is launched somewhere in the world, every time I see it, this is Darknet Diaries.
![]()




 At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the
At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the 
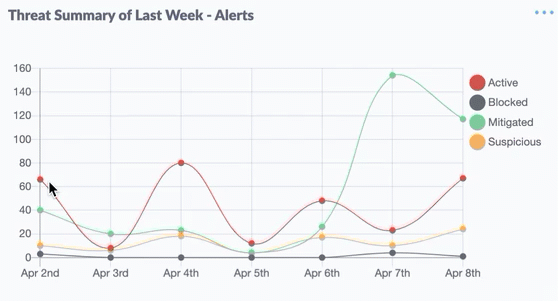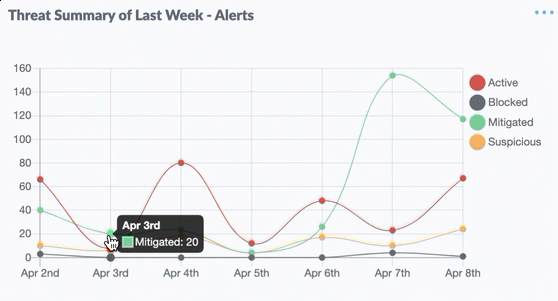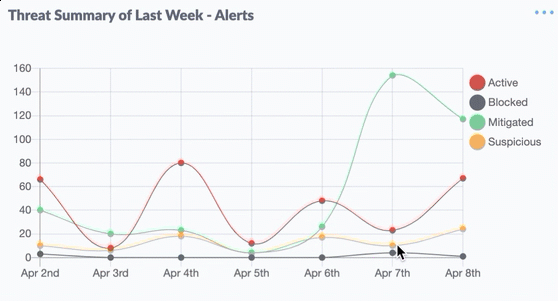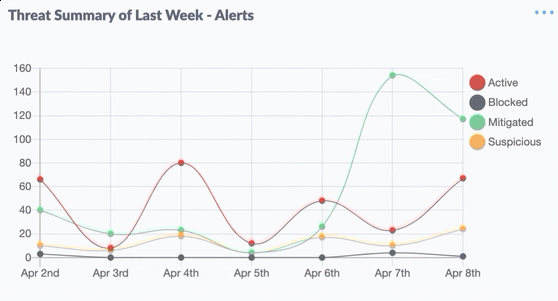
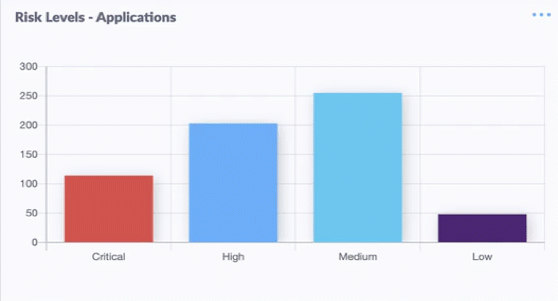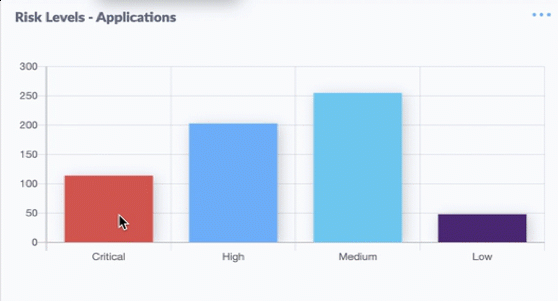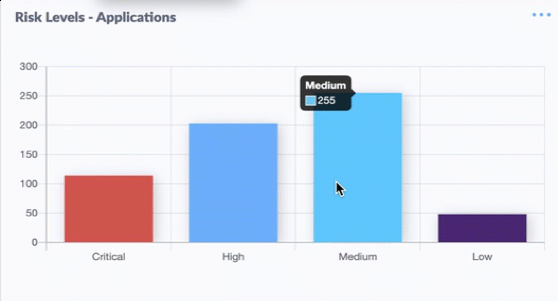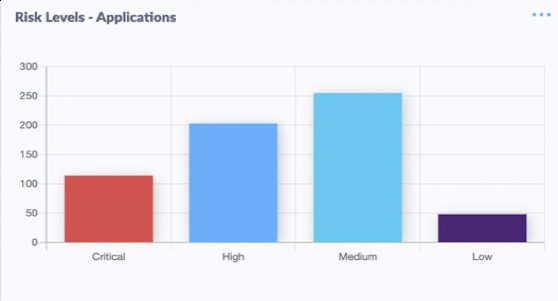
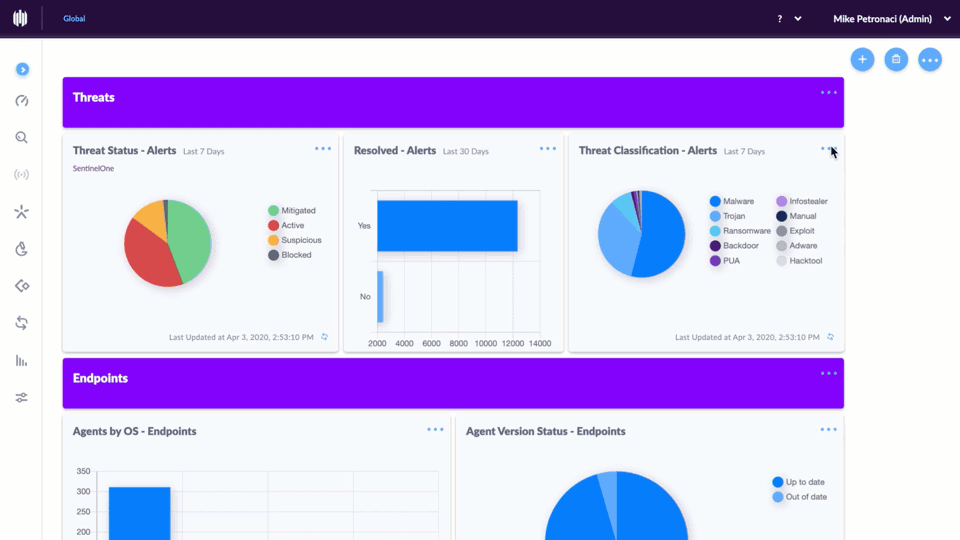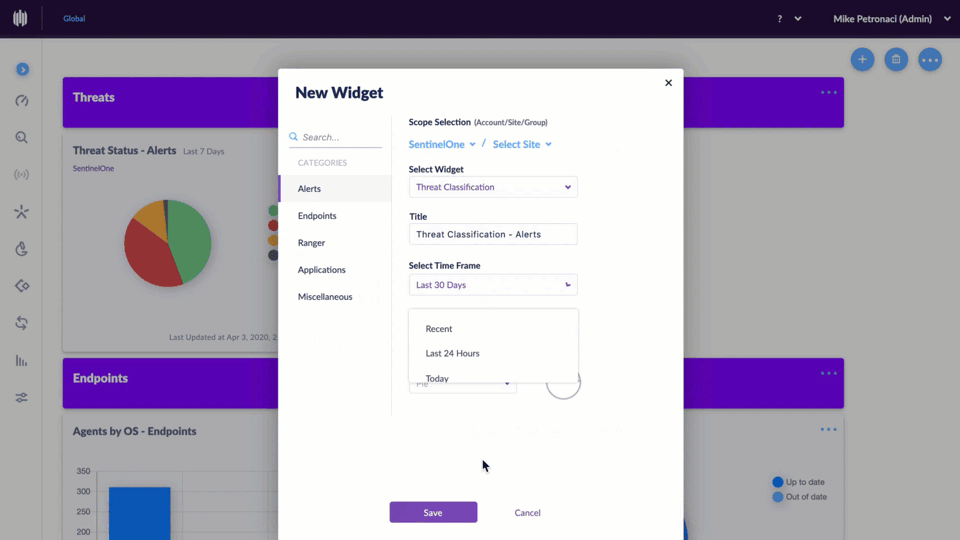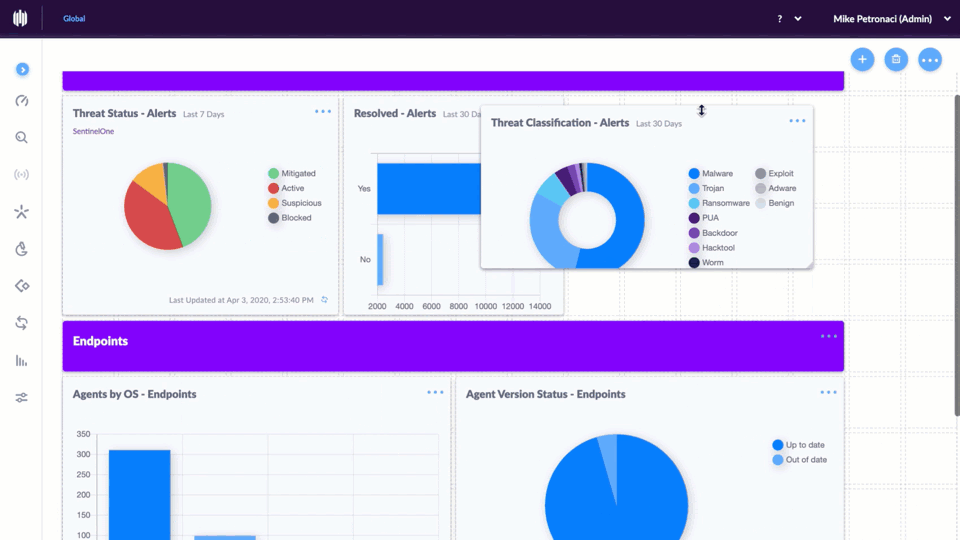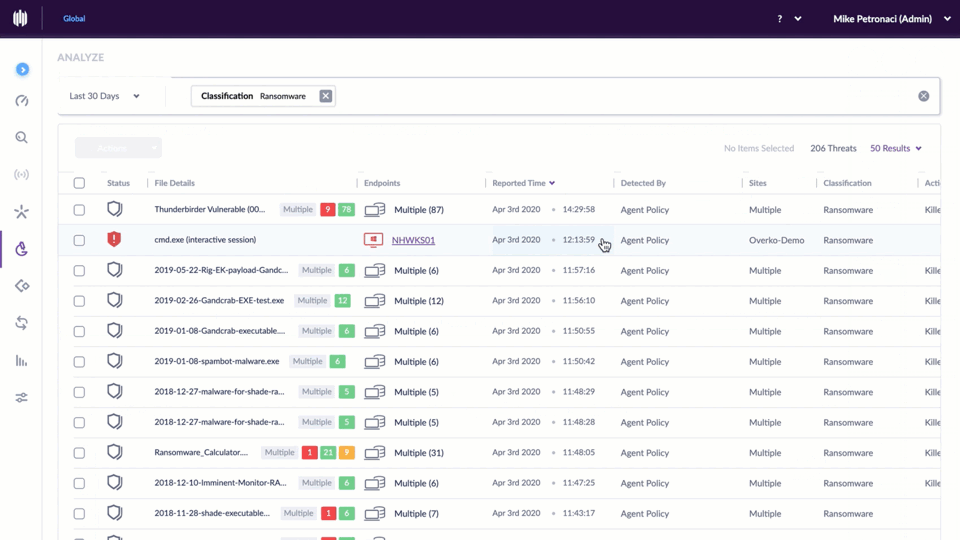


 Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.
Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.




