It’s not the first time we’ve discussed this topic and it almost certainly won’t be the last, but this week’s report by one AV vendor that cyber threats on Mac endpoints have surpassed those on Windows devices, followed by accusations from a prominent Apple evangelist that the vendor was peddling in exaggeration and fear-mongering, have brought the topic into sharp relief once again. Do Macs get viruses? And if so, how do Macs get viruses? Is a Mac safer than a Windows PC? There’s a lot of confusion, misinformation and frankly (sadly) ignorance among so-called ‘Mac gurus’ who should know better. In this post, we’ll spare the fake news and simply lay out the facts. Here’s what we know (and can prove) about macOS malware from publicly verifiable data.

Do Macs Get More Malware Than Windows PCs?
According to a report by Malwarebytes, the average number of threats they detected per endpoint was nearly double on Macs compared to Windows, at 11.0 and 5.8 respectively during 2019. That also represented a huge jump from the 4.8 detections per endpoint that they found on Macs in the year previous to that.
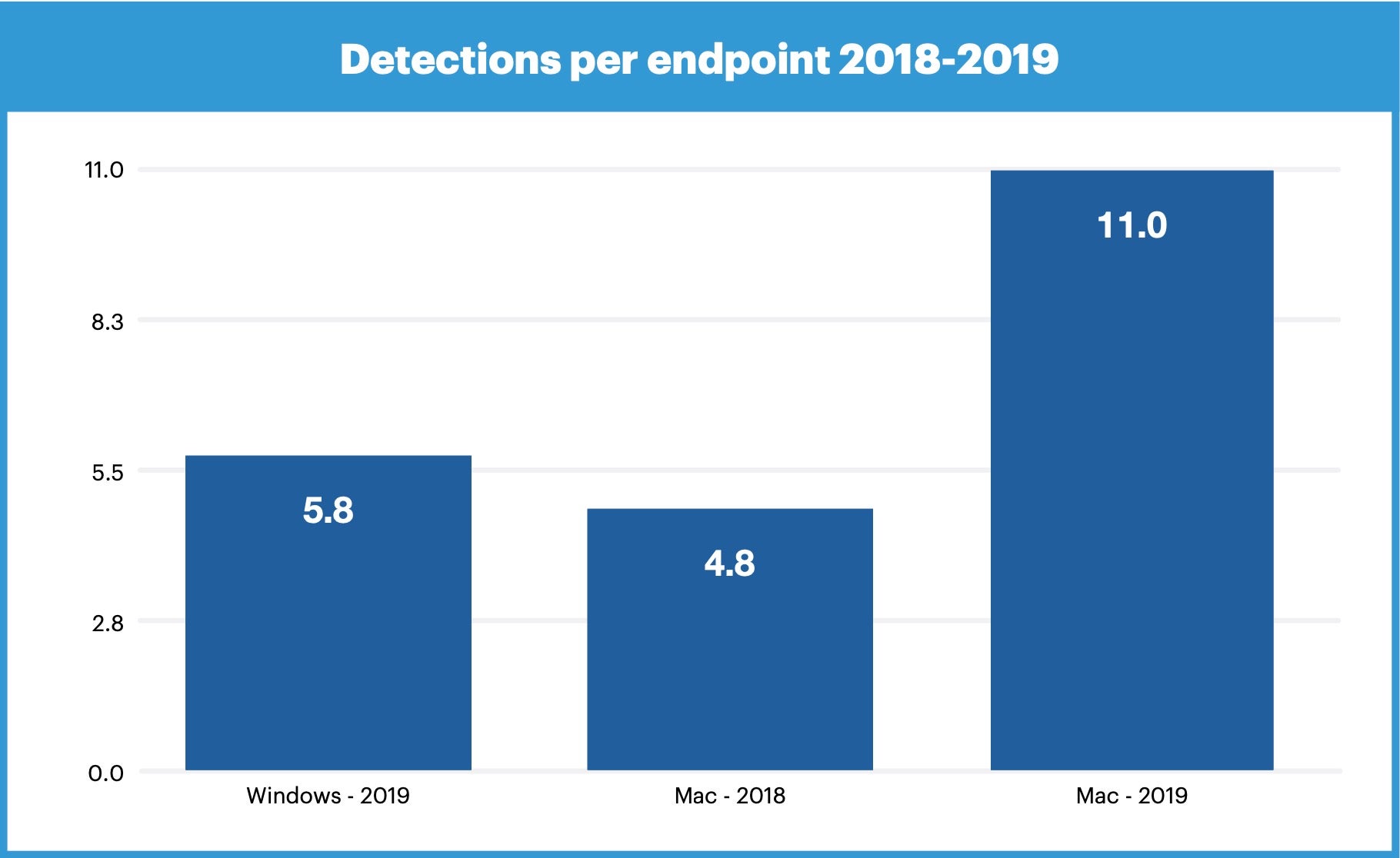
Source
The data led to a flurry of headlines, not least because it was a surprise to many people who’ve long fantasized that Macs have some magical aura that makes them impervious to the same kind of criminal attacks that plague Microsoft Windows machines. One commentator went so far as to accuse the researchers of stoking fears to drum up business for themselves and concluded that, despite unquestionably accepting the data, “the statement that Macs don’t get viruses is still overwhelmingly true”.
Central to the argument that “Macs don’t get viruses” is equivocation over what we’re really talking about. “Virus” is a legacy term, and technically there are very few genuine viruses on any platform at all these days, not even Windows. What we’re really talking about is macOS malware and its supposedly less-dangerous cousins adware and coinminers. For businesses and personal users alike, these different threats are all of a piece: they steal data, hog resources, interfere with productivity and – at worst – lead to more serious network intrusions. Our recent posts on Adload, Shlayer and Lazarus APT go into some of the technical details.
Once you stop arguing about what counts as what kind of threat and accept that in all cases, you’re dealing with unwanted, deceptive and possibly dangerous code running on your machine, then what the data shows is that when you look at these categories together, Macs are heavily-targeted, particularly by adware and coinminers, and more Mac users than ever are being infected. Malware campaigns by APTs and other threat actors are also regular occurrences.
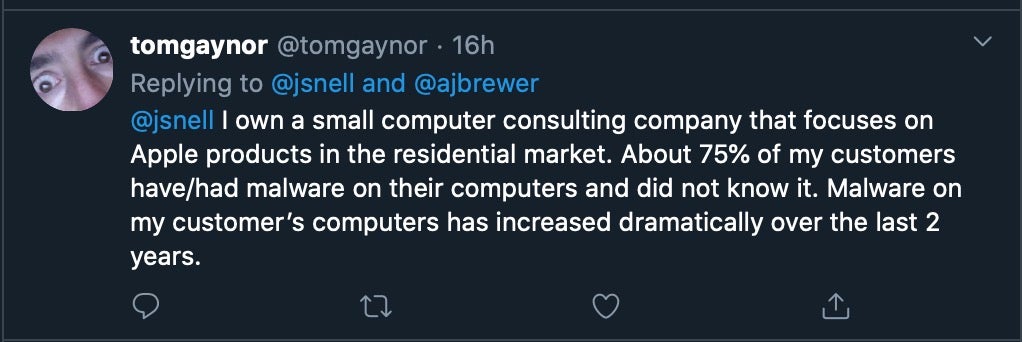
As one Twitter user pointed out, “I own a small computer consulting company that focuses on Apple products in the residential market. About 75% of my customers have/had malware on their computers and did not know it”.
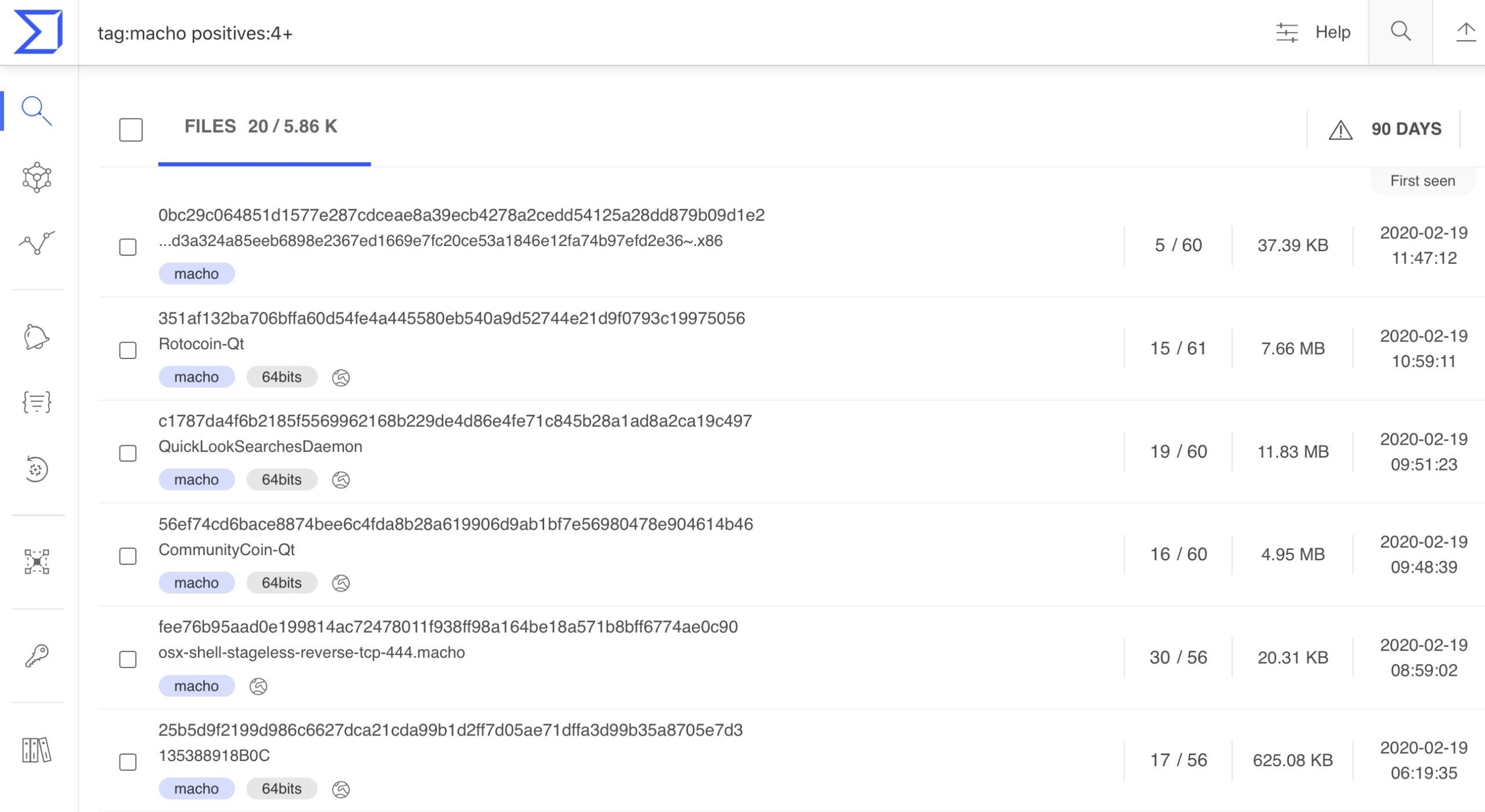
If we look at a public malware repository like VirusTotal and query how many threats have been uploaded that are tagged as ‘macho’ (the native macOS binary, though macOS runs other kinds of executables which are also used in malware) and have more than 4 independent vendors detecting them, then today we’ll get a list of around 5,800 samples. That’s 5,800 individual pieces of malicious software that have been written specifically for macOS in its native binary format over the last 90 days. If malware isn’t a problem on macOS, one might wonder why all these malware authors are wasting their time writing so much of it!
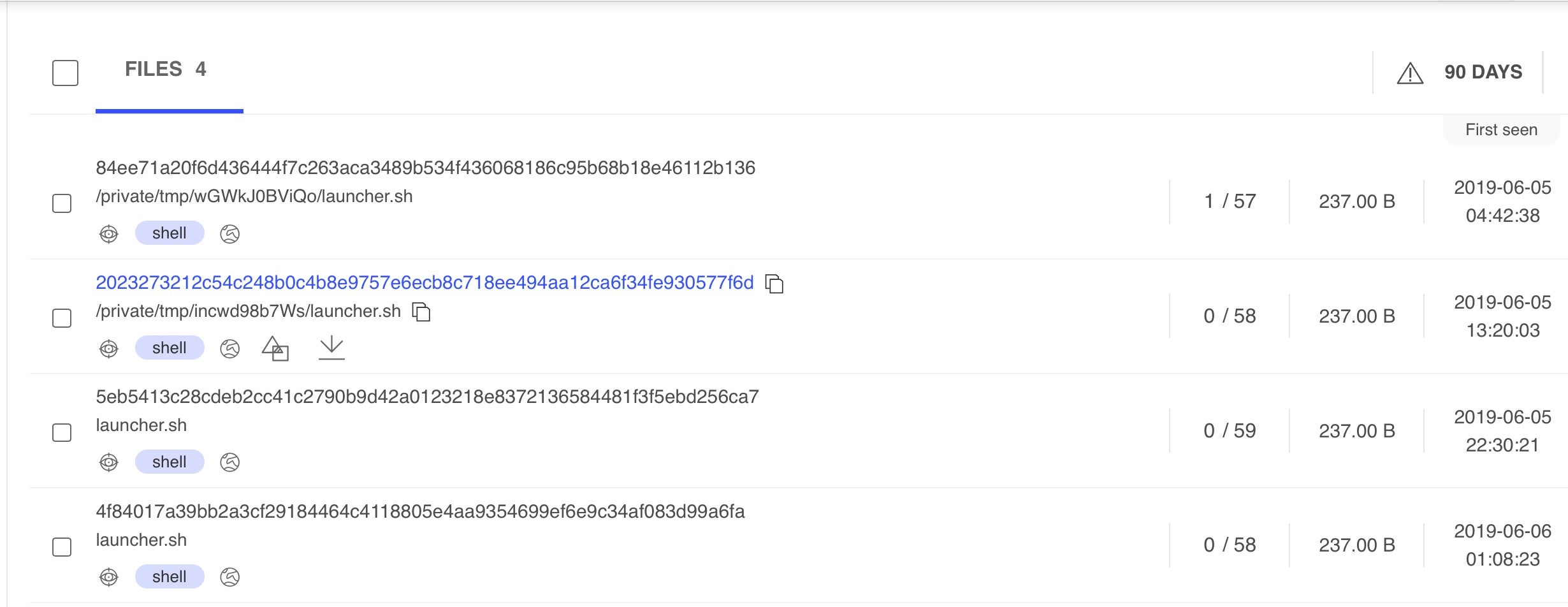
That number is but a small sample. It doesn’t include malware that we’re aware of that doesn’t register on VirusTotal, such as this launcher script for OSX.DarthMiner, a threat that appeared in late 2018. This script was uploaded to VT 8 months ago and is still barely detected by the static engines there, to give but one example:
How Do Macs Get Infected?
So, how do Macs get infected, then, given that the data categorically disproves the myth that Macs don’t get malware?
Macs, of course, are just Unix-based general purpose computers. Apple do not possess some secret sauce that makes them impervious to malware and that Microsoft and other OS vendors have failed to invent. In fact, Apple’s built-in security tools rely on outdated-technology similar to legacy AV products – file hashes, hardcoded path searches and Yara rules – as well as a few proprietary Apple technologies like Gatekeeper, Notarization and code signing, which we’ll say a little bit more about below.
Importantly, all the Mac’s detection and malware removal capabilities are historical – meaning, they are updated to detect threats that have been seen to infect Mac users in the past. There is no predictive or heuristic threat detection built-in to macOS and indeed, the observation by one commentator that Apple have stepped up their game (something we’ve noted also) in terms of adding more detection rules is only a result of the fact that Apple are responding to the increased number of threats that they are actually seeing infecting Apple Mac computers. Those who follow Apple security issues will recall the lament during much of 2018 that XProtect hardly saw a single update, despite lots of new threats appearing during that year. In contrast, we’ve seen three updates to XProtect since the start of 2020. The takeaway there, if it isn’t obvious, is that Apple’s behavior mirrors what we’re seeing at SentinelOne and what Malwarebytes report pointed out: more threats than ever before are targeting macOS users.
And yet, despite all the evidence, we still find Mac gurus who believe and spread the myth that Macs don’t get malware and users don’t need additional security protections. Aside from a lack of awareness about the threats that are actually out there, it seems there are two related misconceptions that inform this kind of thinking:
1. Apple’s built-in tools are sufficient to protect users
2. Anyone who does get infected have themselves to blame for making ‘bad decisions’.
Neither of those beliefs are helpful, and propagating them only serves to do what malware authors most want: keep Mac users unprotected and believing in a false sense of security.
Let’s look at those two claims individually and see how they cash out.
Why Apple’s Tools Won’t Stop All Malware
Are Apple’s built-in tools sufficient to protect users? As we’ve already noted, Apple’s security tools rely on historical data – an attack needs to have happened to someone, some Mac, somewhere, before Apple will add a detection rule for it. But even when Apple add detection rules for a particular piece of malware, that still doesn’t mean they will catch every instance of it.
The reasons are technical and we’ve gone into them elsewhere, but a short summary here should suffice. First, Apple’s blocking technology, Gatekeeper, is easily overridden by users (yup, those same users making those same ‘bad decisions’). Regardless of the “why”, and particularly in an enterprise context where social engineering is well understood, all that matters is that they do, and that that they do in sufficient numbers to make it a worthwhile enterprise for bad actors.
Second, Apple’s detection technology, XProtect, relies on very simple, lightly-obfuscated, string and data pattern matching YARA rules. Threat actors can see how Apple detect their malware within minutes of Apple updating these rules, and in most cases it’s a simple thing for these actors to refactor existing code to avoid Apple’s rules. In all versions of macOS except the new Catalina, XProtect will also fail to scan code that does not have a quarantine bit.
Third, notarization – Apple’s new demand that all 3rd party apps need to be vetted by Apple for malware before they can run on macOS – doesn’t apply in certain situations. Neither Gatekeeper nor Notarization apply if the app is installed without a quarantine bit, even on Catalina. This can happen by design (if the application is installed through MDM software like Jamf), and also by user override or by an unsandboxed process removing the quarantine bit. Astoundingly, removal of this essential attribute doesn’t require admin privileges, so even standard users (and processes running as standard users) can accomplish a bypass of the built-in Apple security tools. Finally, notarization doesn’t come into play even under the latest “strict policy” if the malware payload is downloaded via Curl or similar networking transfer tool by a first stage installer. Such first stage installers are typically either signed with valid Apple developer signatures (until Apple discover them and revoke them) or socially engineer the user to launch them as described above.
In short, the built-in tools are there to block and detect some of the most commonly known families of malware; they are not built to stop anything even mildly advanced or targeted at a particular business. Gatekeeper, XProtect and Notarization are also not going to find or block novel malware, nor are they much use against actively developed malware that iterates regularly.
Are Users to Blame for Risky Behaviour?
There’s a lot of macOS malware that preys on people who insist on risky behavior, it’s true. Torrents, cracked software and websites of dubious legality are all favorite hunting grounds for malware authors on macOS, just as they are on Windows. Whether such users “deserve what they get” is a matter of one’s personal opinion, but what is undoubtedly true is that the methods used by such malware are viable – and reliable – infection vectors that could equally be used against anyone.
Some would argue that users should stick to Apple App Store products to stay safe, but that both concedes the point that Macs are vulnerable to malware if used ‘out of the box’, and it limits users’ ability to exploit the full power of their Mac devices.
On top of that, Apple’s App Store has had its own problems with malware, adware and spyware, so there’s no guarantee that what you download from there will be safe; the only guarantee is that if something is discovered to be harmful after-the-fact, Apple have the power to remove it pretty rapidly.
<span style="font-weight: 400;"What's more, the "stick to the App Store" dictum ignores the reality that if you need a computer (as opposed to say a phone or a tablet), particularly in a business environment, you're going to want to use it for tasks that simply don't fall in line with the kind of feature-lite offerings found in the macOS App Store.
So, blame the users if you want (and if they are employees, you probably should!), but the blame game isn’t going to keep you safe. If there’s one thing we know about malware authors it’s that they are just like any other software developer: they will code what they need to get the job done and nothing more, nothing less. If you’re looking for an answer to the question: why don’t we see more sophisticated malware on macOS like on Windows?’, you’ll find it in the fact that most macOS users don’t run security software and are not security conscious. Why build something complicated when something as simple as this will do?
Conclusion
Sometimes people take an ideological position based on faith, interest or just coherence with other things that they hold to be true or wish to be true, and no amount of data is going to convince them otherwise. But for those with the eyes to see, there’s no question that threat actors have placed increasing attention on macOS, not least because the belief that Macs are “more secure” plays into the hands of malware authors by encouraging complacency about the need for protection.
As we have seen, the built-in security technologies are not keeping Mac users malware free – Apple’s own increased efforts are evidence of this, as is the other data we’ve mentioned above. Meanwhile, cyber criminals are making a nice living out of running coinminers, adware, scamware, backdoors and, yes, malware on unsuspecting users’ macOS devices. And as a final thought for those who don’t have visibility into what’s happening on their Macs: exactly how do you know there isn’t any malware running on any of your Macs, right now? What tools are you using that give you that confidence?
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
![]()













