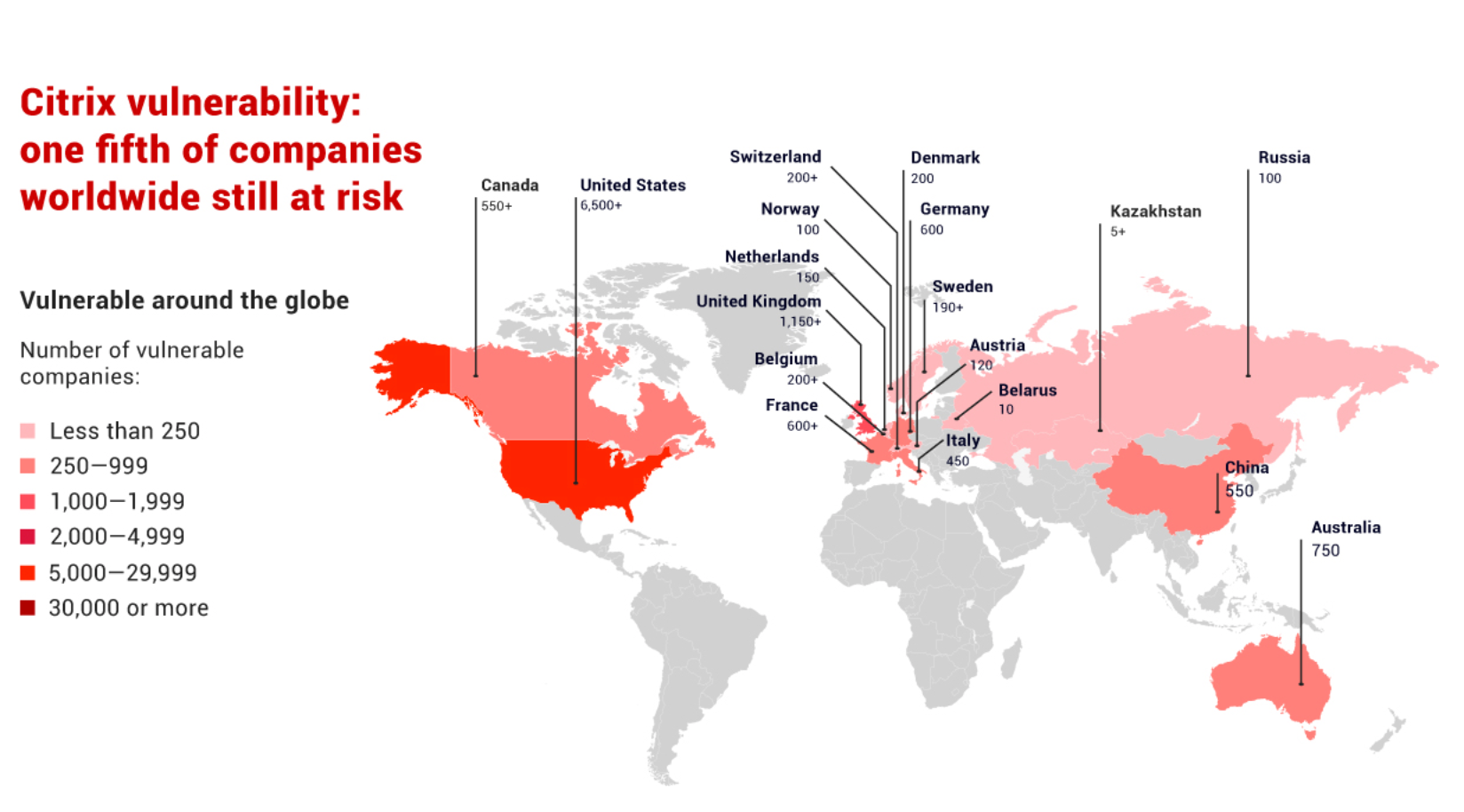
Technical experts, business leaders and state officials agree on one thing about ransomware: it’s a mess. But as we sift through the carnage, there are some good lessons learned from our states, municipalities and healthcare providers.
CEO of Farsight Security Paul Vixie comes at the problem as a researcher. “Ransomware exposes some embarrassing weaknesses in our digital lives. First, our computers and networks are so complicated that only an attacker can understand them — we don’t, and our vendors don’t either. Second, we’re not backing up our critical data at all, or if we are backing it up, we’re using online backup drives or shares — which means a successful ransomware attack will be able to encrypt all our data, including our backups if any. We ought to be ashamed of how little understanding we have and how little care we demonstrate for our digital assets.”
His message is startling. Humans are often to blame for bringing root kits into an environment that leads to all manner of attacks. The weakest entities appear to be state and local governments and healthcare providers. What is the reason for their apparent vulnerability and what groups are racing to their defense?

Elections Are A Ransomware Attack Away from Disaster
In state election land, the Iowa caucus had some technical difficulties and reporting inconsistencies which delayed results. Fingers are pointing at an app used. I spoke with Jeremy Epstein, a veteran volunteer at the polls in Fairfax VA and asked him how exposed we are to attack in a general election.
“Ransomware is a particular threat against elections. While there are no reported cases of ransomware affecting elections and voting systems, there are many points of vulnerabilities including the voter registration systems, electronic poll books, voting machines, and election reporting systems. Election officials work hard to have backup plans in place for any eventuality, but they’re chronically underfunded.”
Jeremy noted potential impacts as “long lines at polling places as voters are checked in by hand, inability to cast votes, loss of votes or delays in results — any of which might reduce public confidence in the election results, even if the election results are not manipulated. What election official would want to go on TV and announce ‘it’ll take a few weeks before we can tell you the results because our systems are out of commission due to ransomware’?”
What function is more essential to our state and local governments than voting? Yet with all of the recent infections, we focused on those services we rely on daily. The DMV, 911 services, land transfers, courthouse services, policing, have all been interrupted by ransomware.
How Vulnerable Are We to Ransomware Attacks?
So just how bad is it? There were 104 ransomware attacks against administrative systems in schools and governments in 2019. This means your children’s data is likely for sale on the darkweb and presents a clean credit profile. One group that is fighting hackers from the ground up is CyberUSA. With 28 member states and over 10,000 member companies, they are focusing on education, software access and coordination with federal resources.
I spoke with CyberUSA member Laura Baker, co-founder of CyberWyoming, and she shared a story about the largest hospital in Caspar WY that was shut down due to ransomware. “Campbell County Health was a blow to all of Wyoming. It felt like a personal attack to our entire state. The IT team at CCH is top notch, the systems they use are excellent, the administration is very proactive about cybersecurity and other issues, and the employee training program is substantial. We all felt ‘how could this happen to CCH?’ The bad guys are attacking our communities and our infrastructure.”
Mississippi chose to conduct a statewide audit of 125 state agencies, boards, commissions, and universities. Although results were mixed, the assessments are similar to SEC guidance. Combine that approach with new legislation calling for a DHS Cyber Coordinator to be appointed in all 50 states and we may be seeing a blueprint emerging. State mandated audits with reporting to state legislators combined with federal technical and financial resources to address the states’ shortcomings are good first steps.
Tom Scott, Executive Director of CyberSC commented, “A ransomware attack is the most prevalent cyber threat to state and local governments and most of the public are oblivious to the potential impact until they are unable to access governmental services. Identification of mission essential functions and assets is the first step to ensuring that the most critical services are made resilient.” Tom noted that there is high demand for DHS CISA assessment services and that there is “limited interaction and coordination between state and local governments beyond SLED’s SCCIIC program and the FBI’s Infragard program.”
Reputations Are At Risk When Ransomware Strikes
Marcus Ranum, CSO at Tenable Security has been dealing with these problems for longer than he would like to admit. “I think ransomware is a tax coming due on IT security incompetence. If you’ve got basic host-side controls and edge controls in place, you should be able to resist the attacks. If you’ve got basic data reliability (backups and business resumption) in place, you can respond effectively to the attacks. The organizations that cut costs and said “it’s not going to happen to us” turn out to be wrong and the money they thought they were saving has been un-saved. They gambled and they lost. It’s just basic incompetence.”
Is he right? Perhaps. It’s worth noting that in all the chaos recently, we haven’t seen a lot of ransomware incidents at financial services entities, and we know they are rigorous about preventing phishing, blocking malware and ensuring they have good backup policies in place. Contrast that with what happens where such cyber hygiene is lacking. The 850-store Wawa breach impacted some 30 million people and credit card issuers. And ransomware gives the victim little choice: pay up or suffer. The latest attacks involving Maze ransomware enable the hacker to exfiltrate data before they encrypt it, and then (optionally) publicly post the data in a shaming process to accelerate payment. Reputation is important, especially for publicly traded companies.
Can We Legislate Our Way Out of Ransomware?
Recently, two NY state senators authored legislation that would prevent municipal governments from using tax dollars to pay ransom to hackers. The US Conference of Mayors issued a similar resolution, denouncing ransom payments. This might work if the program to establish back-ups can be implemented, but this approach does little on the prevention side of the equation. Presumably, cyber insurance could still pay ransom demands if the municipality had purchased a policy.
When an organization buys cyber insurance, they are transferring the risk that could not be addressed through a technology solution. But cyber insurance must be coupled with a strong security stack. Much of the growth in cyber insurance policies has been in sectors which have less funds and fewer resources to handle an inbound attack.
And, with the latest “dumbed down” ransomware kits, any criminal can invest in ransomware as a service and start infecting businesses for $195. That package delivers a return of $7,500 because they cap the number of infections and the amount of ransom to be collected at $250! They must have determined that ransom amount is likely to be paid. And when you combine troves of leaked personal data with automated phishing programs, the hackers will succeed across a wide swath of businesses, with or without insurance.
Lessons From the Tidelands Health Lawsuit
Last week, Tidelands Health in South Carolina was sued in a class action for the loss of thousands of patient data records that resulted from a ransomware attack. One patient had her nuclear stress test cancelled and another patient was given food she couldn’t eat because of no access to medical records. They say that their data was exposed and that Tidelands did not give notice to HHS or to the affected patients. For their part, Tidelands claims no data was exposed, but the latest ransomware strains offer so many “features”, who can really know?
HHS requires reporting of ransomware events because unauthorized control of the data occurs when it is encrypted and is considered a ‘disclosure’ under the HIPAA Privacy Rule. It may be difficult for Tidelands to show that their data was not altered or exfiltrated during the ransomware incident. But with 764 healthcare breaches in 2019 and a Vanderbilt University report stating “breach remediation efforts were associated with deterioration in timeliness of care and patient outcomes,” it seems hospitals are on notice and should have proper back ups.
Health providers hosting data and applications with MSPs should be safer than those trying to manage their own security, but due diligence is required. When Virtual Care Provider Inc. (VCPI) was hit with Ryuk ransomware in December demanding $14 million, 2400 nursing homes and acute care facilities in 45 states were unable to get medicine for patients, access records or conduct business with Medicaid. The true costs of a ransomware attack go beyond the merely financial, which can be devastating enough.
The Ryuk ransomware has not only increased the average cost of a ransom demand; hackers will sell access to compromised MSP’s and open the doors to less skilled hackers. The Albany International Airport was hit with Sodinokibi ransomware, paid a ransom fee and then sued its MSP Logicalnet, claiming they were responsible for the breach. Cyber insurance paid all but $25,000 of the demand, which was the deductible on the policy. Counties and small businesses outsource their data and apps to an MSP because they are ‘experts’ at security but — buyer beware!
Strength Lies in Sharing Our Knowledge
Perhaps the best model I have seen is the public-private partnership model developed between Healthcare Sector Coordinating Council and the Government Coordinating Council. The HHS Cybersecurity program (HICP) falls under the Cybersecurity Act of 2015 and focuses on managing threats and protecting patients. They will identify the top five threats for healthcare and then the top 10 security controls to address those threats. Last, they will help organizations prioritize and implement those controls.
Former CISO of MarinHealth, Jason Johnson helped to put this in context. “While frameworks like NIST are incredibly useful, those in under-funded industries, like healthcare, might not have the expertise to fully digest and implement everything in them. The HICP was created exactly for this reason — it is an easily digestible walk through of the must-do controls from multiple frameworks. If you’re a healthcare security professional, especially at a smaller physician practice or hospital, their set of documents must be on your reading list today.”
So Where Do We Go From Here?
HICP is a voluntary, industry-led initiative supported by federal resources. Broader participation in this program could stem the crisis our healthcare providers are experiencing. Maybe a similar program could be implemented for our state and local governments. Along with state mandated audits and federal technical and financial resources, plus collaborations like CyberUSA and more public-private partnerships like HICP, we may be able to see the beginning of the end in sight. Public-private partnerships can help us clean up some of the mess that cyber criminals so easily exploit and bring a halt to the disruption that ransomware causes to businesses, healthcare providers and our other vital public services.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
![]()