It’s that time of the year again when we’re all doing the two things that cyber criminals love most: spending money and giving generously. Those who seek ill-gotten gains from others have come up with plenty of ways to dupe, manipulate and steal during the holiday season. In this post, we cover seven scams to keep an eye out for.

1. Juice Jacking
The holiday season inevitably involves a lot of us traveling to and from distant friends and relatives, and that can mean visiting unfamiliar public places while in transit as well as seeking out the last drop of battery power from our mobile devices. Los Angeles County District Attorney has warned that criminals are taking advantage of this by loading malware into public USB power charging stations located in places like airports and hotels.
“Juice Jacking”, aka the USB Charger Scam, can take several forms. Fraudsters may install malware onto your device through an infected USB port or cable left hanging in a public charge point, or they may try to give away malicious USB cables as “free gifts” that are loaded with credential-stealing malware. The intent is to export personal data and passwords so that the cybercriminals can drain your bank accounts or commit identity theft.
To stay safe, never use a cable that’s been left in a charging station and don’t accept cables given away as promotional gifts.
Ideally, carry your own cables and a “power bank” charging pack. When charging on the move, find an AC outlet and plug your own charger directly into it.
2. Poisoned Public Wifi
We all love to stay connected while on the move, and retailers, coffee shops and bars know that a free, public wifi hotspot is good for business. Unfortunately, it’s easy for attackers to impersonate these or snoop other users on the same Wifi network.
Snooping means that other users of the network can see your unencrypted traffic – what websites you visit and any clear text data you send through the public hotspot, including what you type into web forms on unencrypted sites. Impersonation occurs when a threat actor sets up a malicious hotspot or rogue access point with an SSID the same as or very similar to the one that you intend to connect to.
In order to stay safe, avoid connecting to public Wifi networks where possible and disable any network discovery settings that allow your device to automatically join public hotspots. Where you do need access, ask staff to confirm the correct Wifi network name (SSID), ensure you’re only browsing sites that begin with https or display the green padlock icon.
Importantly, even if using https, avoid connecting to personal banking or other highly-sensitive, password-protected sites while on public Wifi. Save that kind of work for when you’re connected to a known, trusted network.
3. Holiday Charity Scams
The festive season draws out the best in many of us, but the worst in some, too. There are a number of known scams that target people’s generosity during the holiday season. Some fraudsters spoof the phone numbers of legitimate charities, making it appear on your caller ID that the incoming call is from a charitable organization – and use robocalls and texts to target unwitting consumers. Others go so far as to set up fake charities or pretend to be agents of legitimate organizations.
To stay safe, refuse solicitations from callers either online, on your phone or at your door claiming to represent a charity. If you wish to donate to an organization, approach them directly and check their credentials by visiting their official website.
Never give out personal information to an unsolicited caller, as they may use this to commit identity theft.
4. Seasonal Phishing Scams
The holiday season makes an ideal time for phishing scams as many of us are in a rush and desperate to buy gifts at bargain prices. Meanwhile, genuine online stores are bombarding our inboxes with holiday discounts and special offers. Prime conditions for spammers to hook victims with phishing links to malicious websites that may be clones of the real thing but are really intended to drop malware or phish login and password credentials.
These scams may take the form of special offers, gifts and coupons, or claims that you’ve been invoiced for something you didn’t order and that you need to click a link to “report a problem”. Some bad actors embed malware in images as well as attached documents, while one notorious malware platform has been spotted conducting a seasonal phishing campaign by inviting targets to accept an invitation to the staff Christmas party.
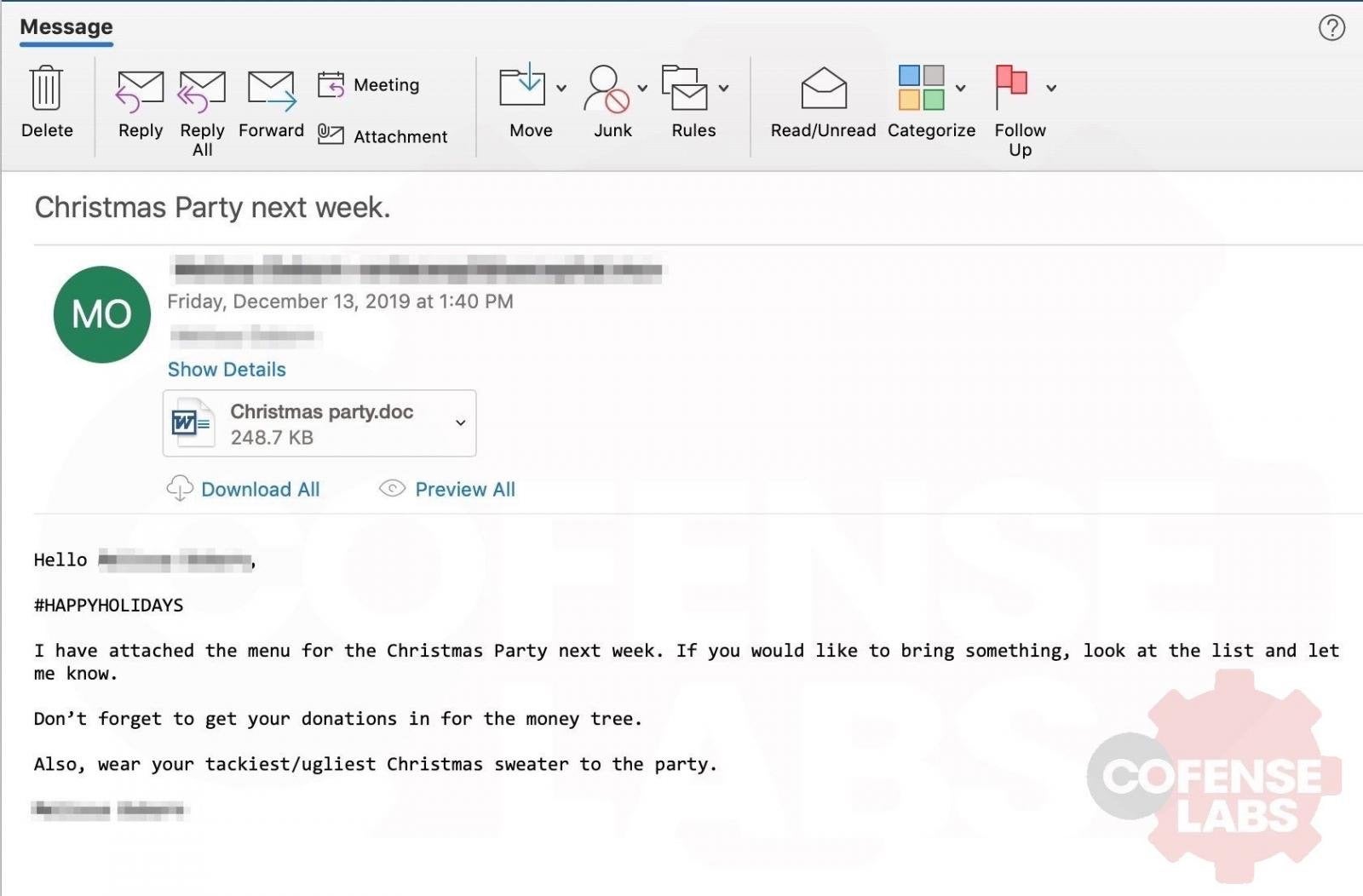
Of course, all these are just prompts to get the user to either download a malicious file, click a fraudulent link or enter credentials on a fake website.
To stay safe, use trusted security software to block malware. Disable the loading of remote content in your email client preferences, and inspect link addresses before clicking on them. Look out for simple tricks where the scammer users what looks like a real address, say google.com and replaces one or more letters with a homograph or punctuation, like go0gle.com or goo.gle.com. Such tricks may seem obvious on inspection, but are easily overlooked when only glanced at. When you do land on a website, pay attention to what’s in the address bar.
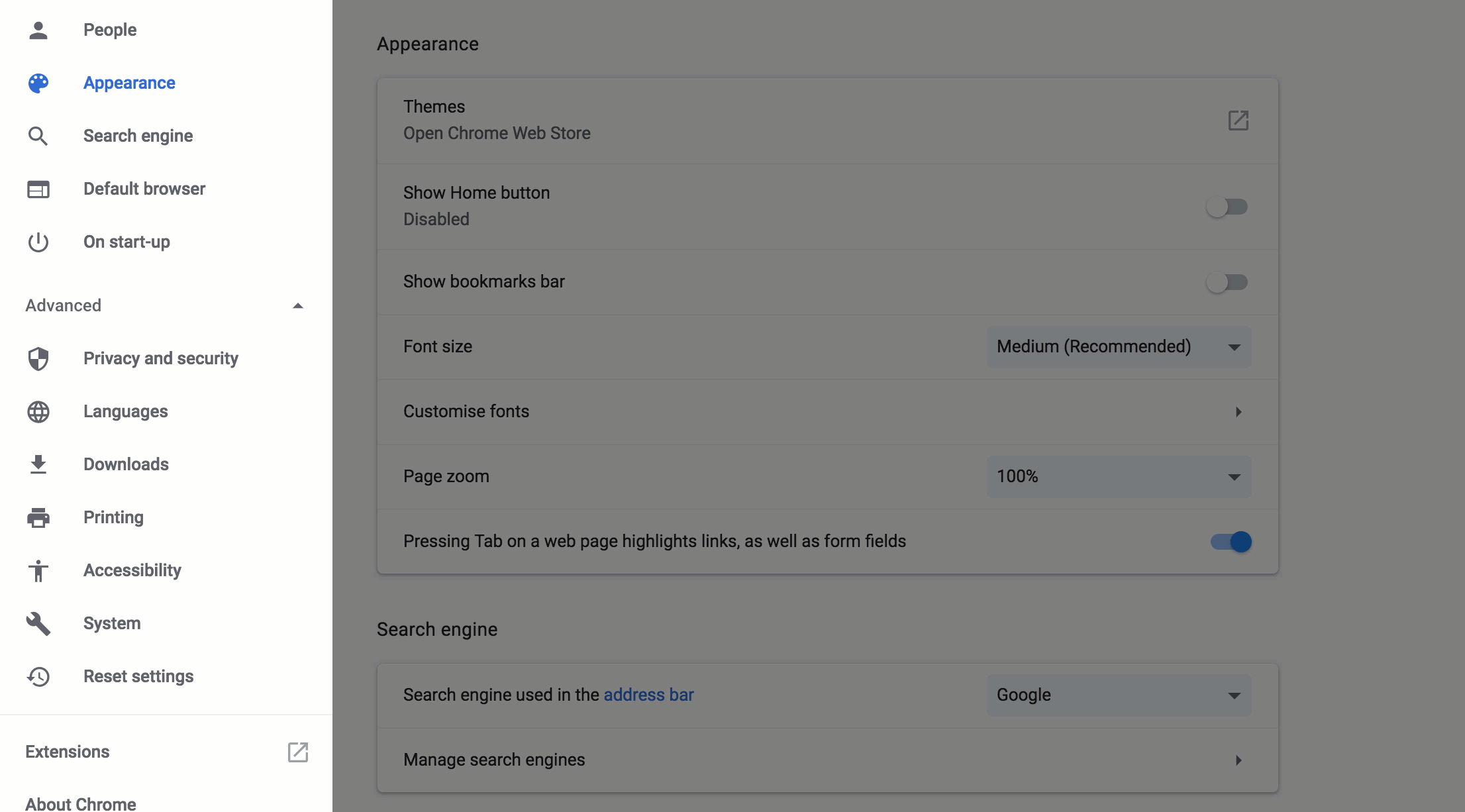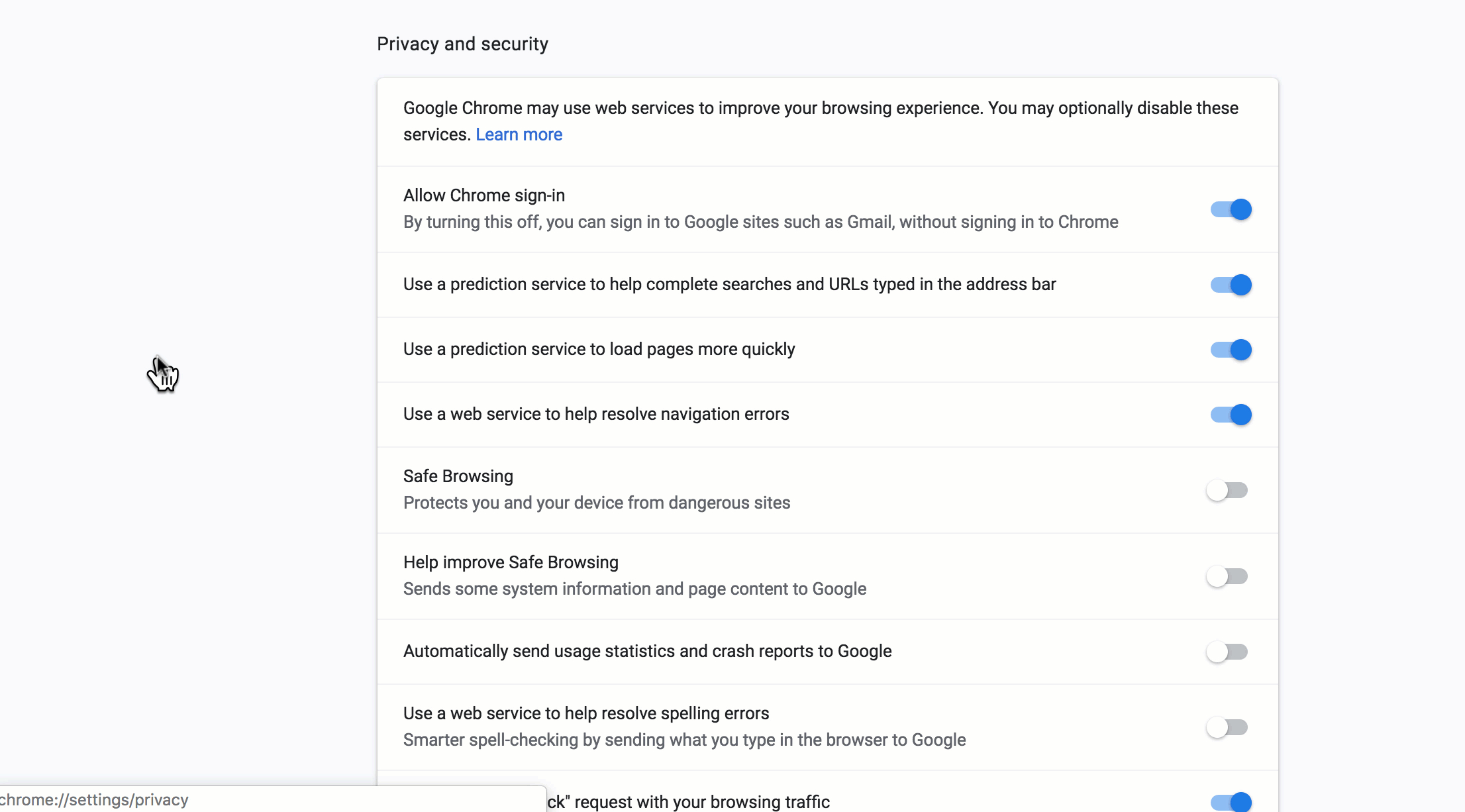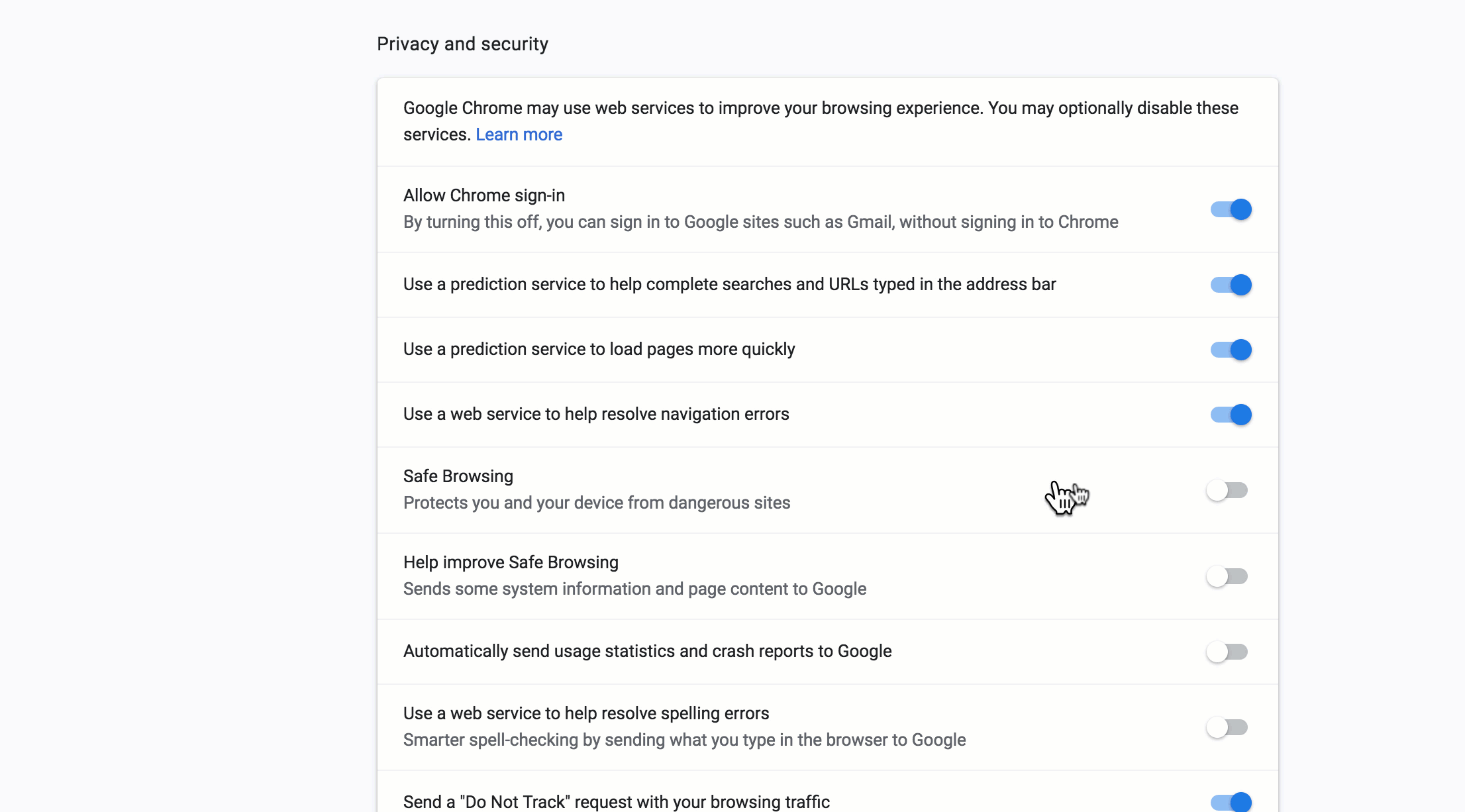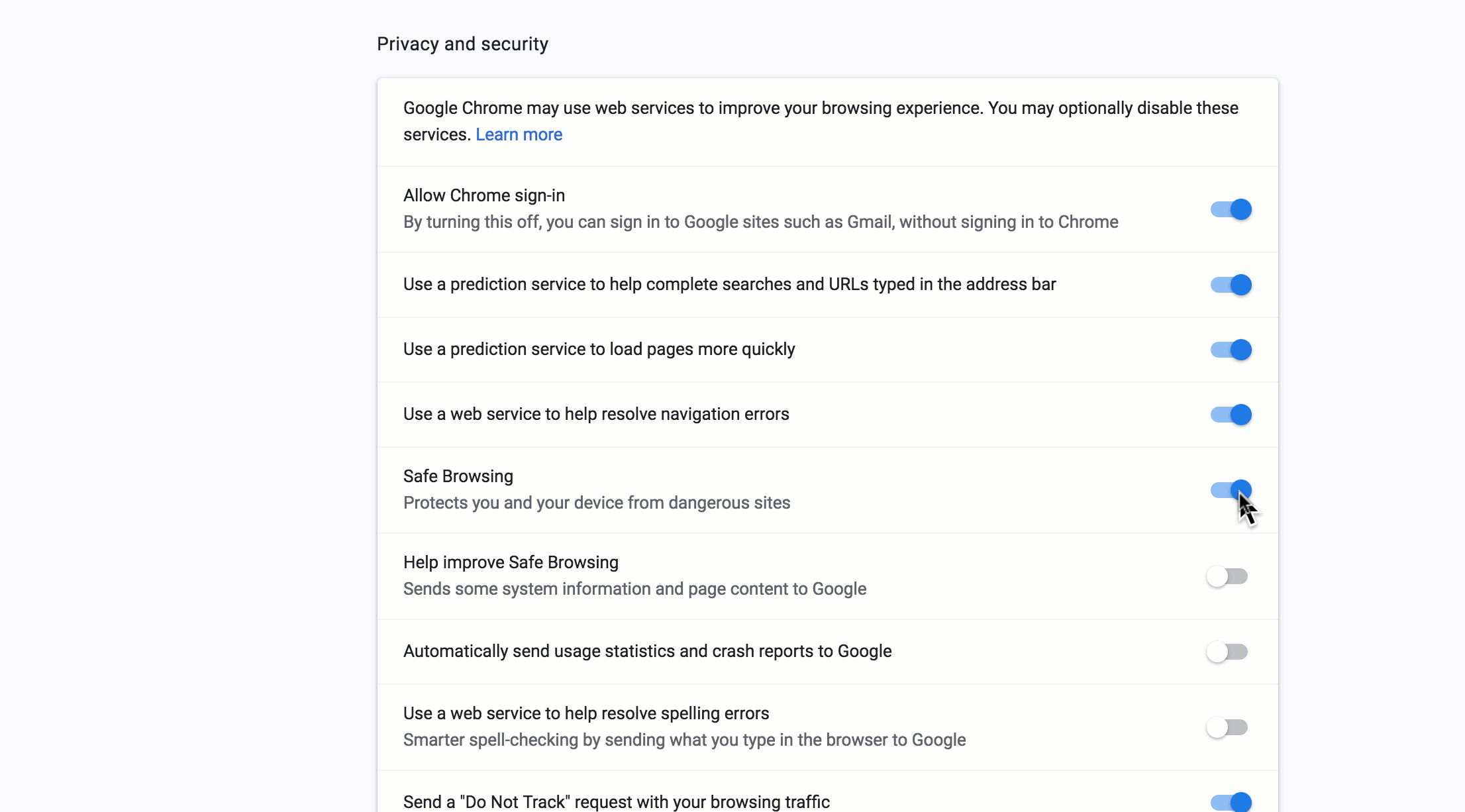
It helps to ensure your browser preferences show full website addresses and that your Safe Browsing prefs in ‘Privacy & Security’ are turned on.
5. Fake Updates
Keen to share and join in the fun, we’re all prone to clicking on a video shared across social media, text message or email, particularly during the festive season. But beware of those that pop up a message telling you that you need to update or download some kind of media player – fake Flash players are a favorite of adware and malware scammers – in order to view it.
These are almost always the first sign of a scam in which the fraudsters aim is to infect your device either with a PUP/adware installer or a more serious Emotet, Trickbot or other trojan platform.
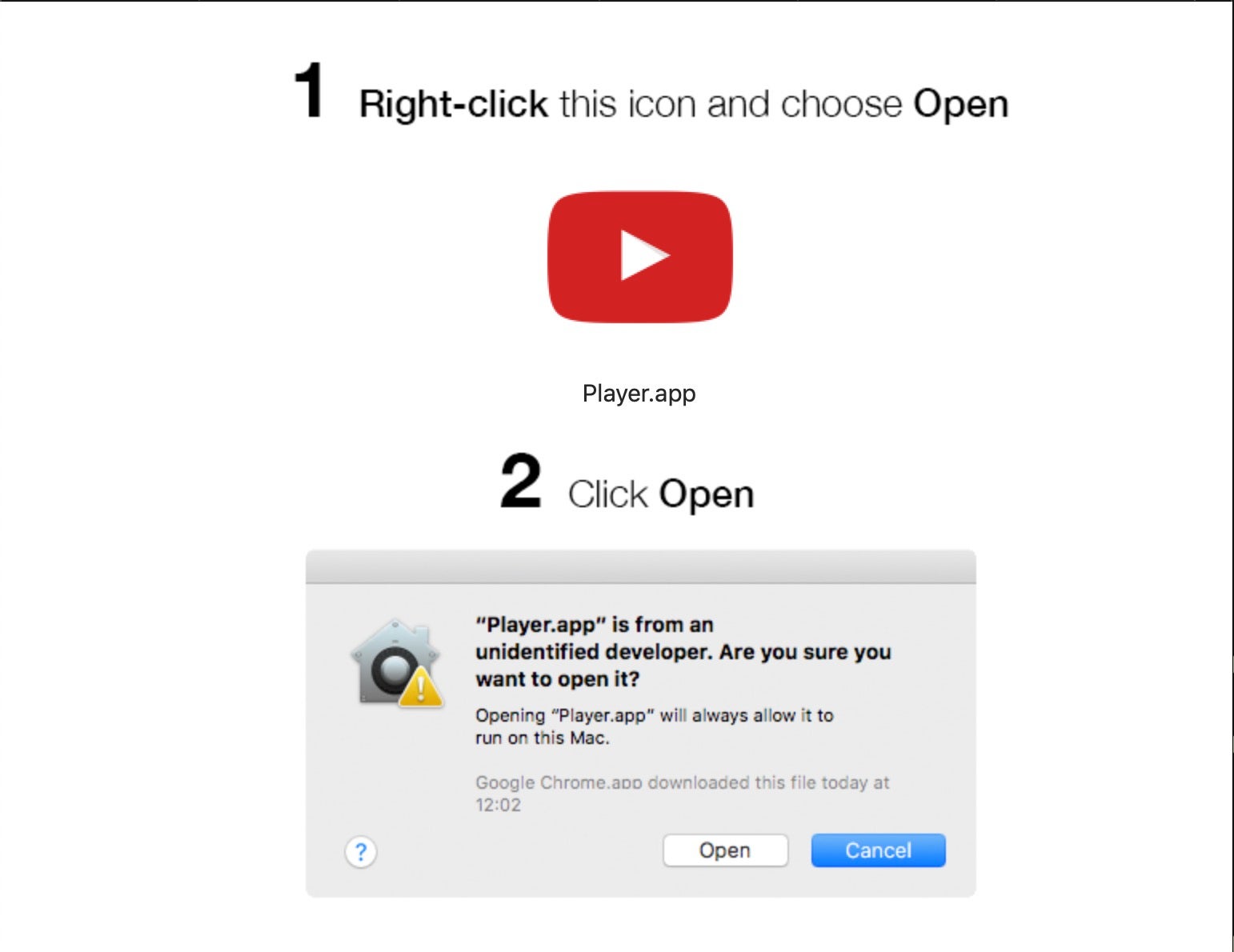
To stay safe from these kinds of threats, always dismiss any such pop-up alerts. Launch your usual media player from the Dock or Taskbar and check if it really needs an update.
Note that if your media player won’t play the media file of a type it should, assume the offending file is malicious and send it to the Trash. Again, a good security solution can protect you from this kind of threat.
6. Fake Coupon & Discount Apps
Fraudsters don’t only restrict themselves to setting up fake websites; they’ll even build entire fake applications and distribute those through unofficial app repositories in the aim of getting users to download malware. These apps typically offer users multiple discounts or coupons promising great deals on many popular products.
In general, you’re safer sticking to apps distributed from reputable app stores, but it’s worth bearing in mind that these have also become increasingly targeted by malicious actors. Apple’s iOS App Store has had a few high-profile cases of data exfiltrating malware and spyware, and problems with Google’s Play Store are a common news item.
To stay safe, only download and install applications that you have a genuine need for, and always check out the details of the developer.
Most ‘free apps’, particularly those offering shopping discounts are going to be at best plaguing you with in-app advertisements in order to generate their income. At worst, they may be delivering malware or stealing you data.
7. Fraudulent Ads
Encountered all year round but descending like a plague between November and January, scam ads can be found not only on sketchy websites but also circulated through social media like Facebook, Twitter, and other sharing platforms. With billions of users, these platforms make attractive targets for ads containing malicious links.
In some cases, these fake ads may show multiple items, with several listed at normal prices but one item at some incredibly low price. They may even contain text such as “Due to a pricing error, this item is now on sale at half it’s RRP, but it won’t be for long!” The aim is to make people click immediately to take advantage of what they think is a mistake. Of course, it’s all a scam and the link takes the user to a fake sale site with credit card skimmers embedded in the code.
Ads run by scammers can be difficult to spot, since they use many of the same marketing tricks as legitimate ads. And although there is a breed of such ads that use poor quality, blurred images, others simply steal glossy, highly-produced photos from real products. If you are tempted into clicking on an ad placed through social media, check all the details carefully. Does the website offer comprehensive information about product details, shipping costs, returns and customer support? Is the language on the website error-free?
Use a whois lookup to see how long the website has been around (scam sites are usually less than a few months old). And ultimately, is the deal “too good to be true?” The best defence against fraudulent ads is buyer caution.
Conclusion
The holiday season is a time for giving and reflection, and not a little relaxation. Unfortunately, there’s plenty of scammers and fraudsters out there intent on selfishly exploiting this time of year for their own ends and ruining the festivities for others. We hope that the tips above will help you to avoid becoming a victim and wish everyone a safe and happy festive season.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
![]()




 Stories here have exposed countless scams, data breaches, cybercrooks and corporate stumbles. In the ten years since its inception, the site has attracted more than
Stories here have exposed countless scams, data breaches, cybercrooks and corporate stumbles. In the ten years since its inception, the site has attracted more than 










