CTO.ai’s developer shortcuts eliminate coding busywork
There’s too much hype about mythical “10X developers.” Everyone’s desperate to hire these “ninja rockstars.” In reality, it’s smarter to find ways of deleting annoying chores for the coders you already have. That’s where CTO.ai comes in.
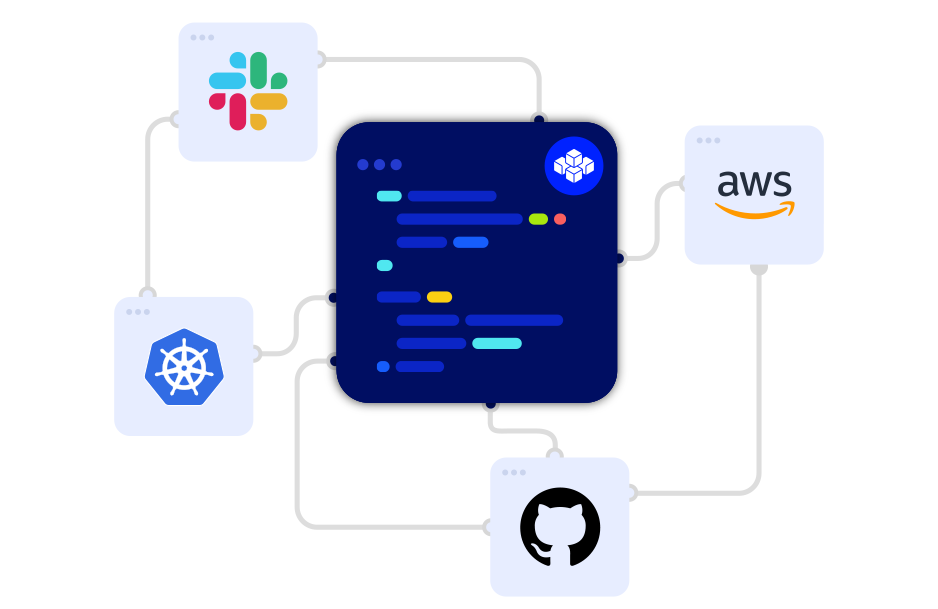
Emerging from stealth today, CTO.ai lets developers build and borrow DevOps shortcuts. These automate long series of steps they usually have to do manually, thanks to integrations with GitHub, AWS, Slack and more. CTO.ai claims it can turn a days-long process like setting up a Kubernetes cluster into a 15-minute task even sales people can handle. The startup offers both a platform for engineering and sharing shortcuts, and a service where it can custom build shortcuts for big customers.

What’s remarkable about CTO.ai is that amidst a frothy funding environment, the 60-person team quietly bootstrapped its way to profitability over the past two years. Why take funding when revenue was up 400% in 18 months? But after a chance meeting aboard a plane connected its high school dropout founder Kyle Campbell with Slack CEO Stewart Butterfield, CTO.ai just raised a $7.5 million seed round led by Slack Fund and Tiger Global.
“Building tools that streamline software development is really expensive for companies, especially when they need their developers focused on building features and shipping to customers,” Campbell tells me. The same way startups don’t build their own cloud infrastructure and just use AWS, or don’t build their own telecom APIs and just use Twilio, he wants CTO.ai to be the “easy button” for developer tools.

Teaching snakes to eat elephants
“I’ve been a software engineer since the age of 8,” Campbell recalls. In skate-punk attire with a snapback hat, the young man meeting me in a San Francisco Mission District cafe almost looked too chill to be a prolific coder. But that’s kind of the point. His startup makes being a developer more accessible.
After spending his 20s in software engineering groups in the Bay, Campbell started his own company, Retsly, that bridged developers to real estate listings. In 2014, it was acquired by property tech giant Zillow, where he worked for a few years.
That’s when he discovered the difficulty of building dev tools inside companies with other priorities. “It’s the equivalent of a snake swallowing an elephant,” he jokes. Yet given these tools determine how much time expensive engineers waste on tasks below their skill level, their absence can drag down big enterprises or keep startups from rising.
CTO.ai shrinks the elephant. For example, the busywork of creating a Kubernetes cluster such as having to the create EC2 instances, provision on those instances and then provision a master node gets slimmed down to just running a shortcut. Campbell writes that “tedious tasks like running reports can be reduced from 1,000 steps down to 10,” through standardization of workflows that turn confusing code essays into simple fill-in-the-blank and multiple-choice questions.

The CTO.ai platform offers a wide range of pre-made shortcuts that clients can piggyback on, or they can make and publish their own through a flexible JavaScript environment for the rest of their team or the whole community to use. Companies that need extra help can pay for its DevOps-as-a-Service and reliability offerings to get shortcuts made to solve their biggest problems while keeping everything running smoothly.
5(2X) = 10X
Campbell envisions a new way to create a 10X engineer that doesn’t depend on widely mocked advice on how to spot and capture them like trophy animals. Instead, he believes one developer can make five others 2X more efficient by building them shortcuts. And it doesn’t require indulging bad workplace or collaboration habits.
With the new funding that also comes from Yaletown Partners, Pallasite Ventures, Panache Ventures and Jonathan Bixby, CTO.ai wants to build deeper integrations with Slack so developers can run more commands right from the messaging app. The less coding required for use, the broader the set of employees that can use the startup’s tools. CTO.ai may also build a self-service tier to augment its seats, plus a complexity model for enterprise pricing.

Now it’s time to ramp up community outreach to drive adoption. CTO.ai recently released a podcast that saw 15,000 downloads in its first three weeks, and it’s planning some conference appearances. It also sees virality through its shortcut author pages, which, like GitHub profiles, let developers show off their contributions and find their next gig.
One risk is that GitHub or another core developer infrastructure provider could try to barge directly into CTO.ai’s business. Google already has Cloud Composer, while GitHub launched Actions last year. Campbell says its defense comes through neutrally integrating with everyone, thereby turning potential competitors into partners.
The funding firepower could help CTO.ai build a lead. With every company embracing software, employers battling to keep developers happy and teams looking to get more of their staff working with code, the startup sits at the intersection of some lucrative trends of technological empowerment.
“I have a three-year-old at home and I think about what it will be like when he comes into creating things online,” Campbell concludes. “We want to create an amazing future for software developers, introducing automation so they can focus on what makes them such an important aspect. Devs are defining society!”
[Image Credit: Disney/Pixar via WallHere Goodfon]