Are you relatively new to the Mac platform and wondering what kind of tools are available for security research, malware analysis, reverse engineering and Mac infosec in general? While Macs share a heritage with Linux and thus have many common tools (although often with different implementations), there is also a whole bunch of macOS specific tools that you might not be aware of yet. In this post, I cover some of the essential tools that will help you with security-related work on macOS, from text editors and process monitors to disassemblers and networking tools. Most are free or inexpensive, and all are tools that I use on a regular basis.

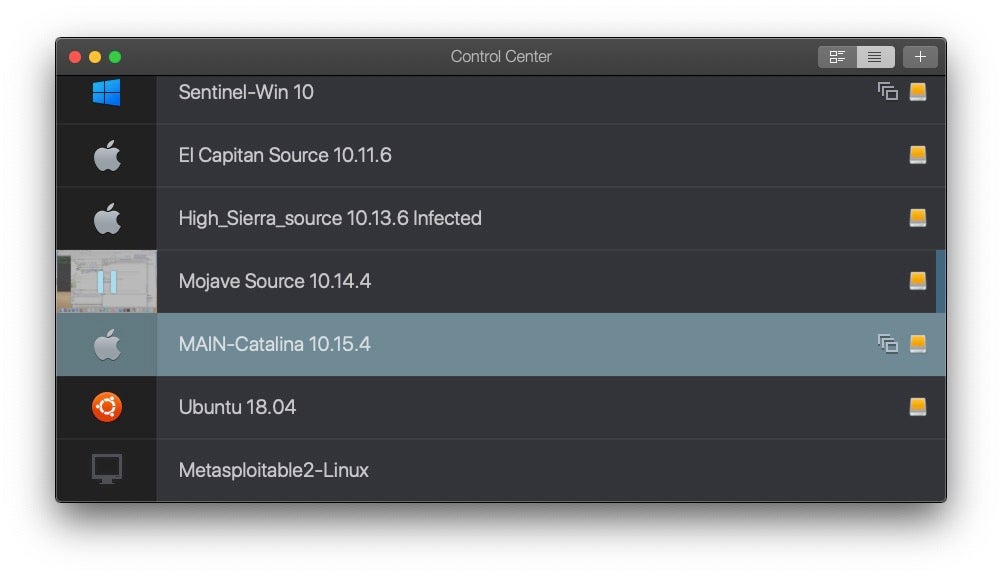
Running macOS on a Virtual Machine
If you’re planning on doing any kind of investigation into Mac malware, want to set up a lab for attacking Mac clients or simply want to investigate macOS internals with System Integrity Protection turned off, then you’re going to need to set up some VMs (Virtual Machines), and for that you need some good virtualization software.
VMWare is probably the most well-known commercial virtualization product out there, and of course it has a Mac version, called Fusion. Oracle’s VirtualBox is a capable alternative if you’re looking for free, but has some serious limitations, such as no snapshot feature. If you’re primarily interested in running Mac VMs on a Mac host, my personal recommendation is Parallels. Although VMWare Fusion runs macOS guests perfectly well, I find Parallels has somewhat smoother graphics performance. It’ll also run Windows and Linux guests just as well as VMWare. The price and feature set are otherwise comparable.
General Purpose Text Editors for Mac
Nothing causes more controversy than a debate on “which is the best text editor”, so let’s get this one out of the way early! If you already have a favorite text editor you’ll hopefully find it’s already available on macOS. Atom, Brackets, and Sublime are all available on Apple’s desktop platform, but if you haven’t picked a favorite yet, then I’d recommend BBEdit from Bare Bones software. This Mac-specific text editor comes in a free version with no time restrictions, and offers a polite upsell for the extra features if you want them. I say ‘polite’ because there are no nags or reminders once you’ve passed the initial “trial” stage during which time all the extra features are enabled. You’ll only want to pay for it if you find the extra features are things you need (or you want to support the developers good work!).
BBEdit has lots of useful features, like easy diffing, multi-file search, line processing, grep and project workspaces, to name a few. Of course, it has all the usual things you’d expect in a good text editor from column selection and multiple cursors to syntax highlighting, cold folding and snippet management. It also has great automation features with Python-based text filters and the ability to run user-defined scripts on selected text or the entire document. Conveniently, you can also run scripts that you’re editing within BBEdit itself. This editor has pretty much every feature I can imagine. A true workhorse.
It’s also worth-mentioning for those that are not familiar with the Mac that you also have the powerful Vi text editor built-in for free on the command line. Vi is a multi-purpose tool that’s great for coding and reverse engineering. Because it includes a command line interface, you can call shell commands within (and on) your current editing session, which is extremely useful. For example, if you open a binary file in Vi, you can dump it to hex without leaving the editor by issuing the command
:%!xdd
After making your edits, revert back to binary before saving:
:%!xxd -r
The % character ensures that the command is applied to the contents of the file, while the ! is used to call the external command line utility xxd. We use xxd‘s -r switch to revert the hex dump back to binary format. Vi can have a steep learning curve, but it will pay you back in spades. Start here for a quick intro.
For Hex editing specifically, I find the native hexdump and xxd utilities sufficient for my needs, but Hex Fiend is a useful GUI alternative.
IDEs and Code Editors on the Mac
All of the above text editors can be used for coding, but if you’re looking for a rich-featured development environment there are other options. The default on the Mac is of course Xcode, which is free and available for download from the Apple Mac App Store. As I’ll say more about later, you will want to install Xcode’s command line tools regardless of whether you have a need for the IDE or not.
Microsoft’s Visual Studio Code is also available on the Mac (and is also free) and provides a very nice, slick and powerful editor with tonnes of plug-ins. If you’re coming to macOS from the Linux world, you’ll be pleased to know that Geany is also available on the Mac.
I don’t really have a favorite among these. I use all three of them from time to time depending on what language I’m working with: typically, Xcode for Objective C and Swift; Geany for pure C and Go; Visual Studio for Python, PowerShell (yes, PowerShell is available on the Mac, too!), JavaScript and everything else.
Finally, if you plan on working with AppleScript in any shape or form, and there’s a few good reasons for doing that from a security perspective, ignore the built-in Script Editor (located at /Applications/Utilities/Script Editor if you can’t!) and grab a copy of Script Debugger, which will save you endless hours of headaches. Like BBEdit, this software has an open-ended free version and non-aggressive upsell for the extra features.
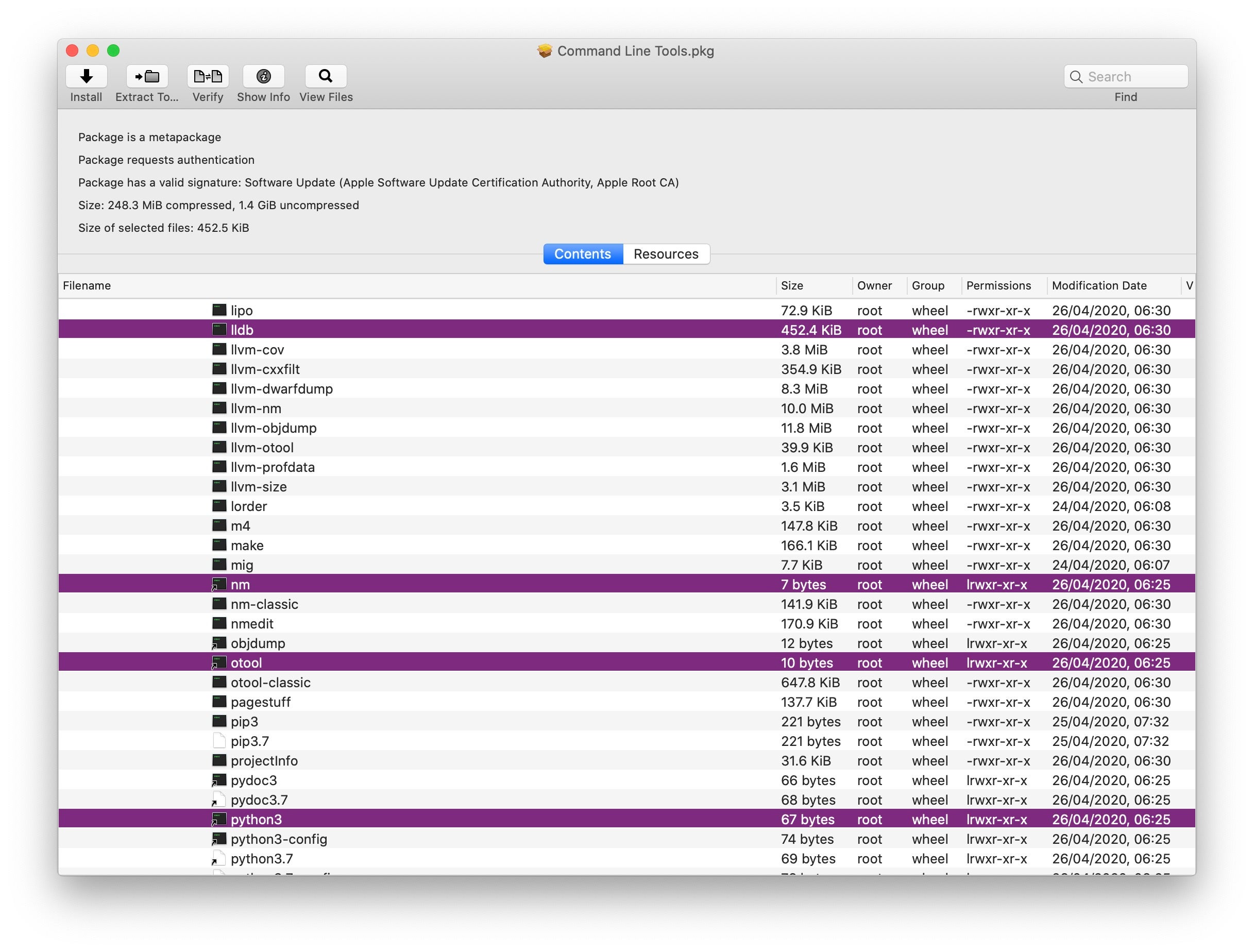
How to Install Xcode Command Line Tools
The Xcode Command Line Tools are an absolute must-have and one of the first things I always load up on any macOS install, virtual or bare metal. Installing the command line tools is simple. Just open a Terminal window and type:
$ xcode-select --install
Click “Install” to download and install Xcode Command Line Tools. You can choose to include or ignore downloading the Xcode IDE at the same time.
There’s over a hundred tools packaged here, including such essentials as strings, nm, python3, otool and lldb.
Package, Archive and Disk Image Inspectors
If you were wondering what tool I used in the previous screenshot to inspect the Command Line Tools package, let me introduce you to Pacifist, one of two essential tools for inspecting packages, archives and disk images. Pacifist is shareware and free to use with a time delay on launch, but only costs $20 to support.
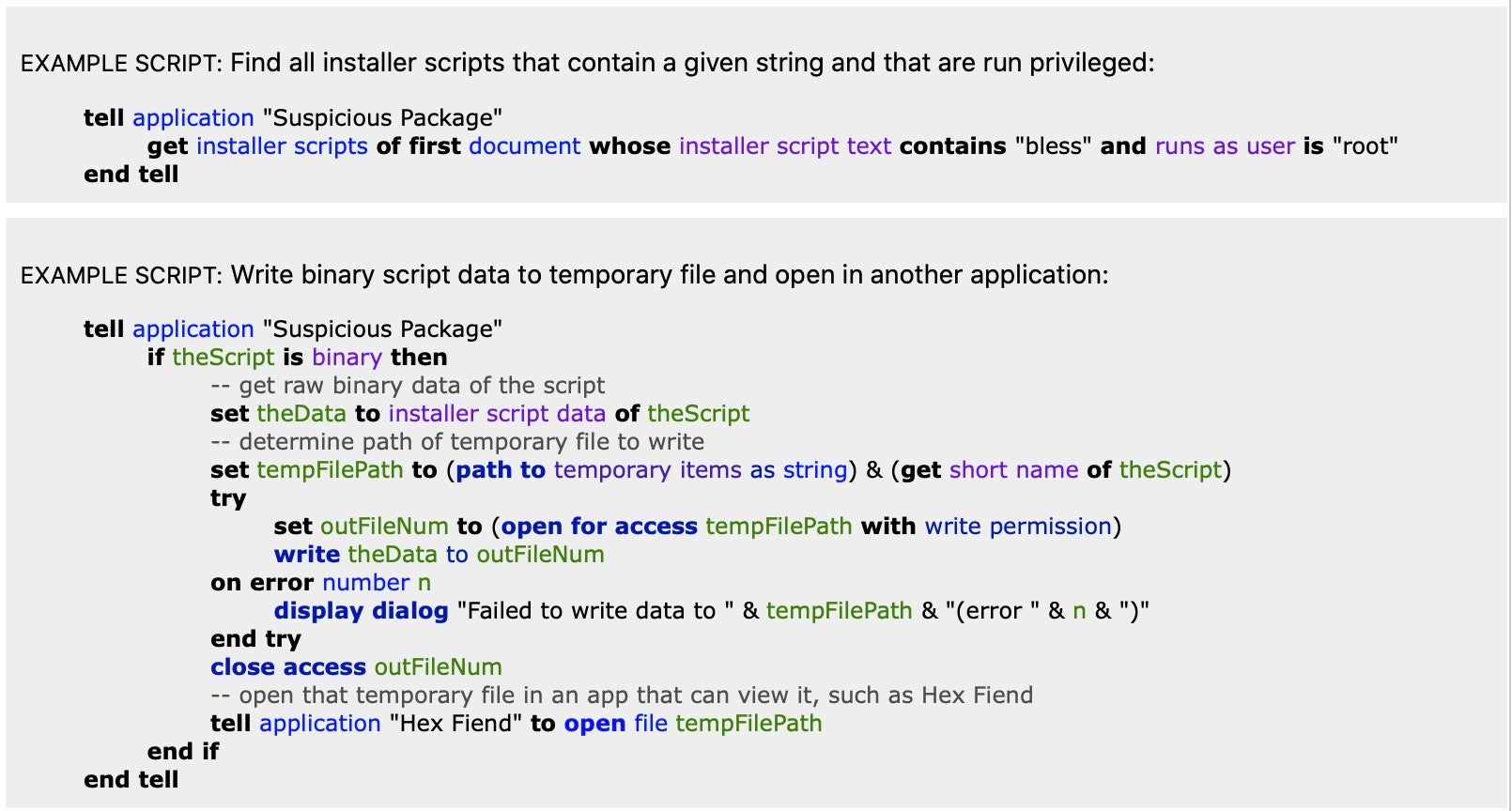
Another useful tool you should have in your armoury for inspecting .pkg files is the free SuspiciousPackage tool from developers Mothers Ruin software. What I particularly love about this application is the robust AppleScript support, which makes it possible to automate searching packages for specific capabilities, items and strings.
Disassemblers and Debuggers for macOS
All the major reversing tools from other platforms are available on macOS. These include Ida Pro, radare2, Binary Ninja and Ghidra. There’s also the built-for-Mac Hopper disassembler.
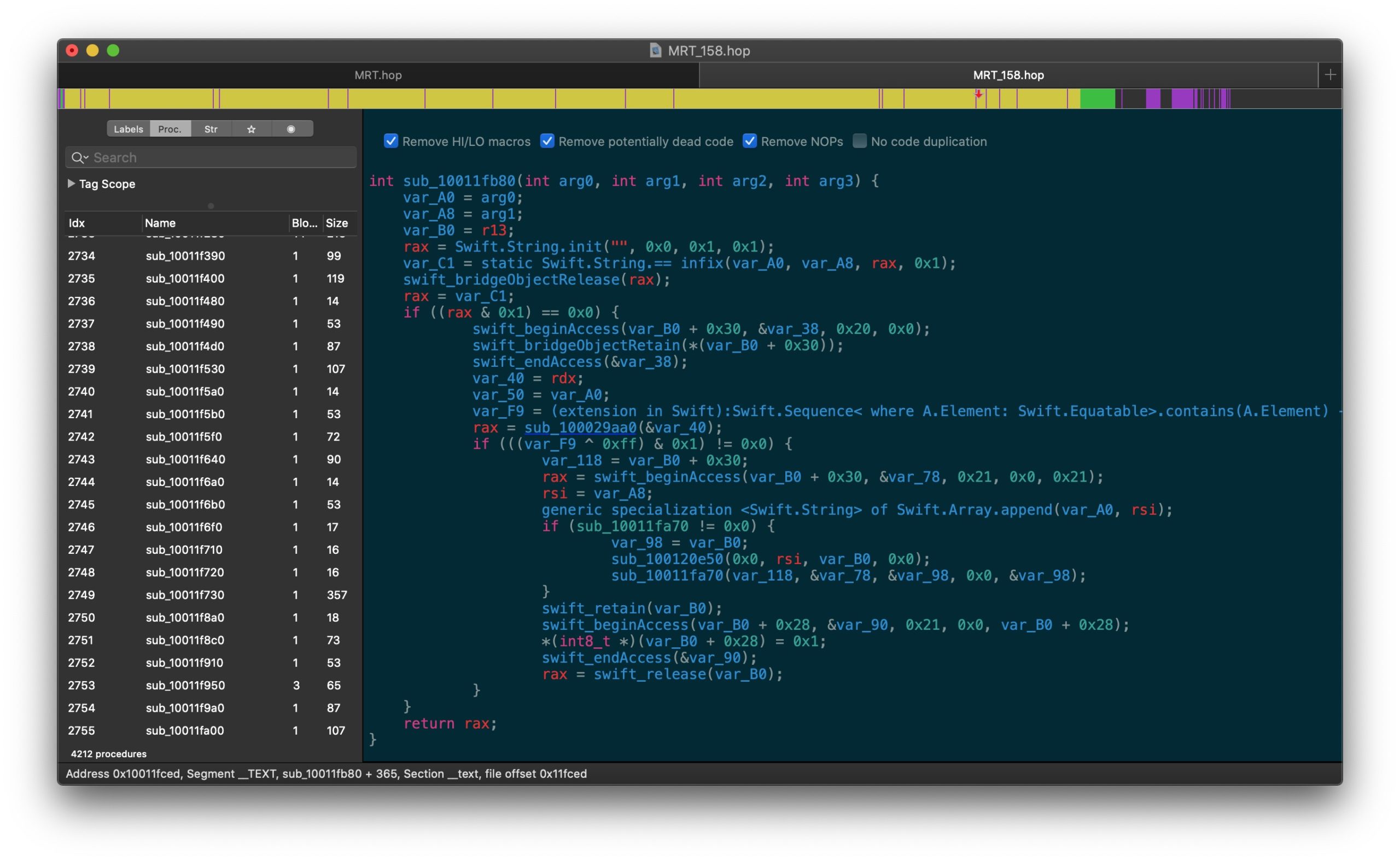
There’s also the GUI version of radare2, Cutter, as yet another alternative.
If you download the free Xcode Command Line tools as suggested above, you’ll gain access to otool and lldb, which along with Hopper and radare2, are my personal favorites for macOS static and dynamic reversing work.
Mac Tools for Process and File Monitoring
Process and File monitoring are basic functions you need for any kind of malware dynamic analysis, bug hunting or software reverse engineering. If you execute
$ apropos snoop
on the command line, you’ll see there’s a few built-in utilities based on DTrace for file and process monitoring.
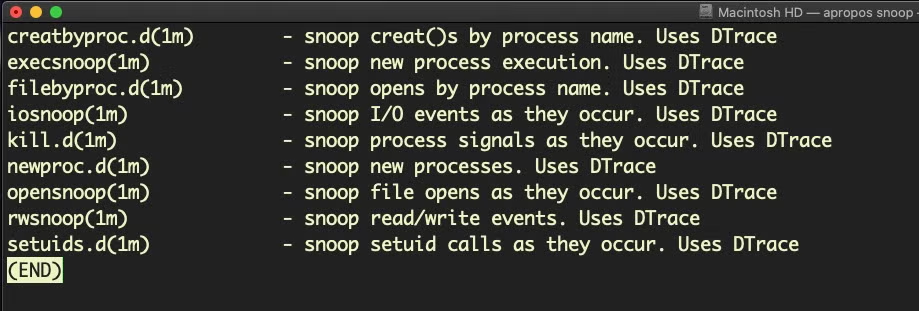
Unfortunately, these have been somewhat castrated by System Integrity Protection, so you really have to run them on a SIP-less VM client to get much value out of them on recent versions of macOS.
The native command line fs_usage utility is still useful for displaying system calls relating to the filesystem, and to that end FSMonitor provides a convenient graphical interface. Once free, the tool is now proprietary, but it’s very reasonably priced (~$19 at the time of writing).
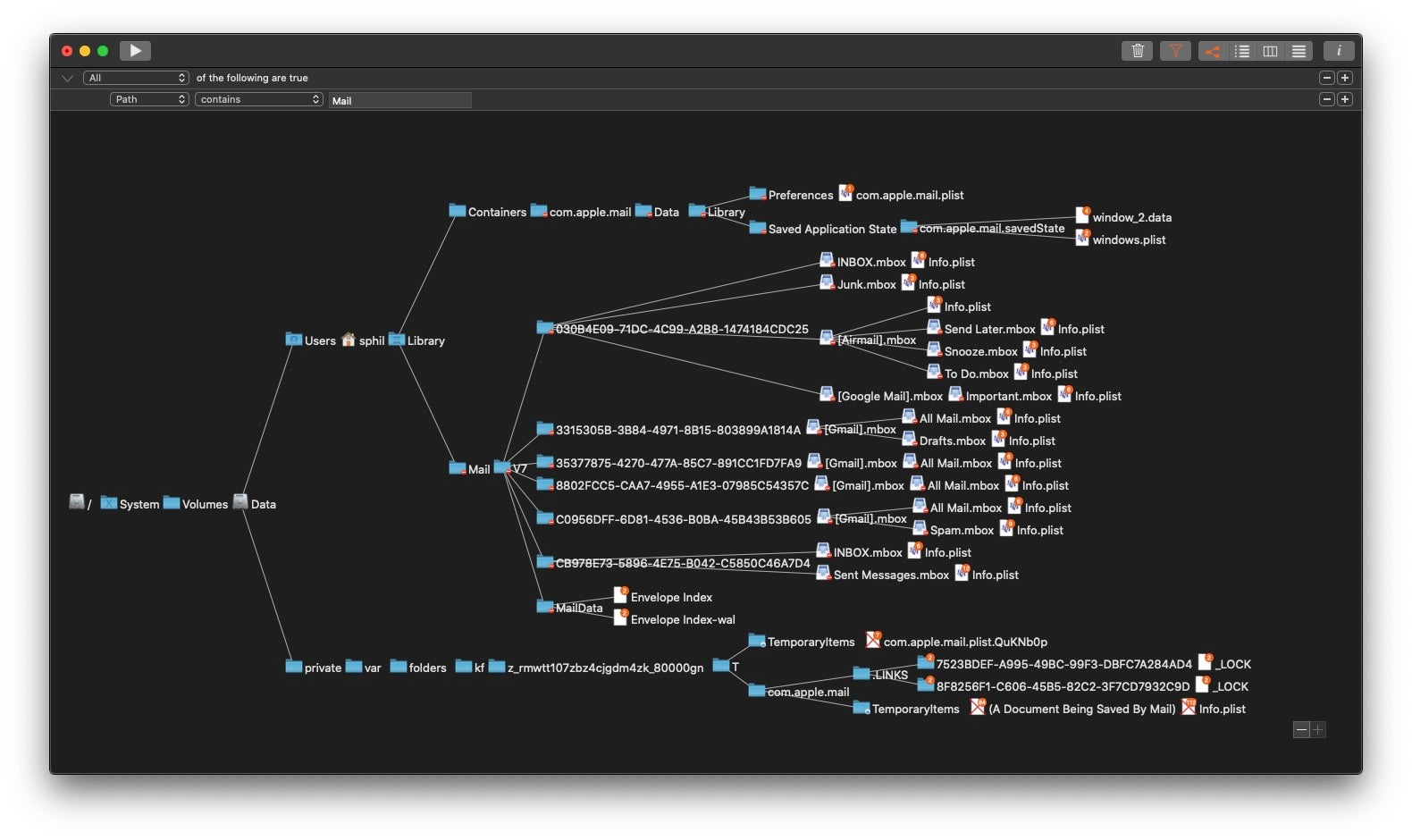
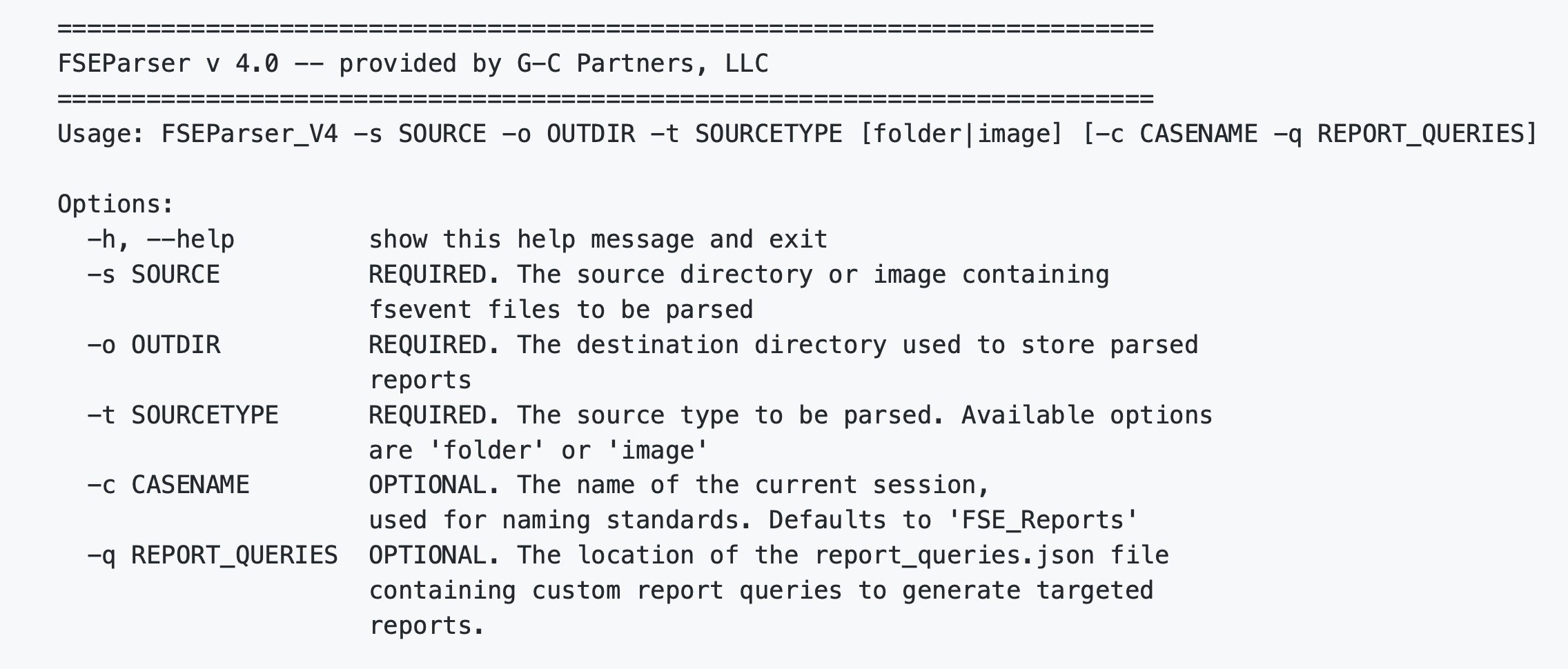
FSEvents are written to disk by the OS and can be found in the root of each volume in a hidden directory called /.fseventsd. In order to access them, you’ll have to drop down to root and CD in to the dir, but inside you’ll be met by some very unfriendly gzip compressed data. Fortunately, FSEventsParser comes to the rescue here. This free tool allows you to parse and extract data relevant to specific enquiries. You can define your own but lots of pre-made queries are available that will help you to report on most aspects of file activity.
Process monitoring on the Mac can of course be achieved through Activity Monitor.app and the command line tools ps and top. Jaron Bradley’s TrueTree repo offers a more nuanced look at process hierarchies while Patrick Wardle’s TaskExplorer offers a convenient way to explore processes and see the signature status, loaded dylibs, open files, network connections and even VirusTotal status for each file backing a running process.
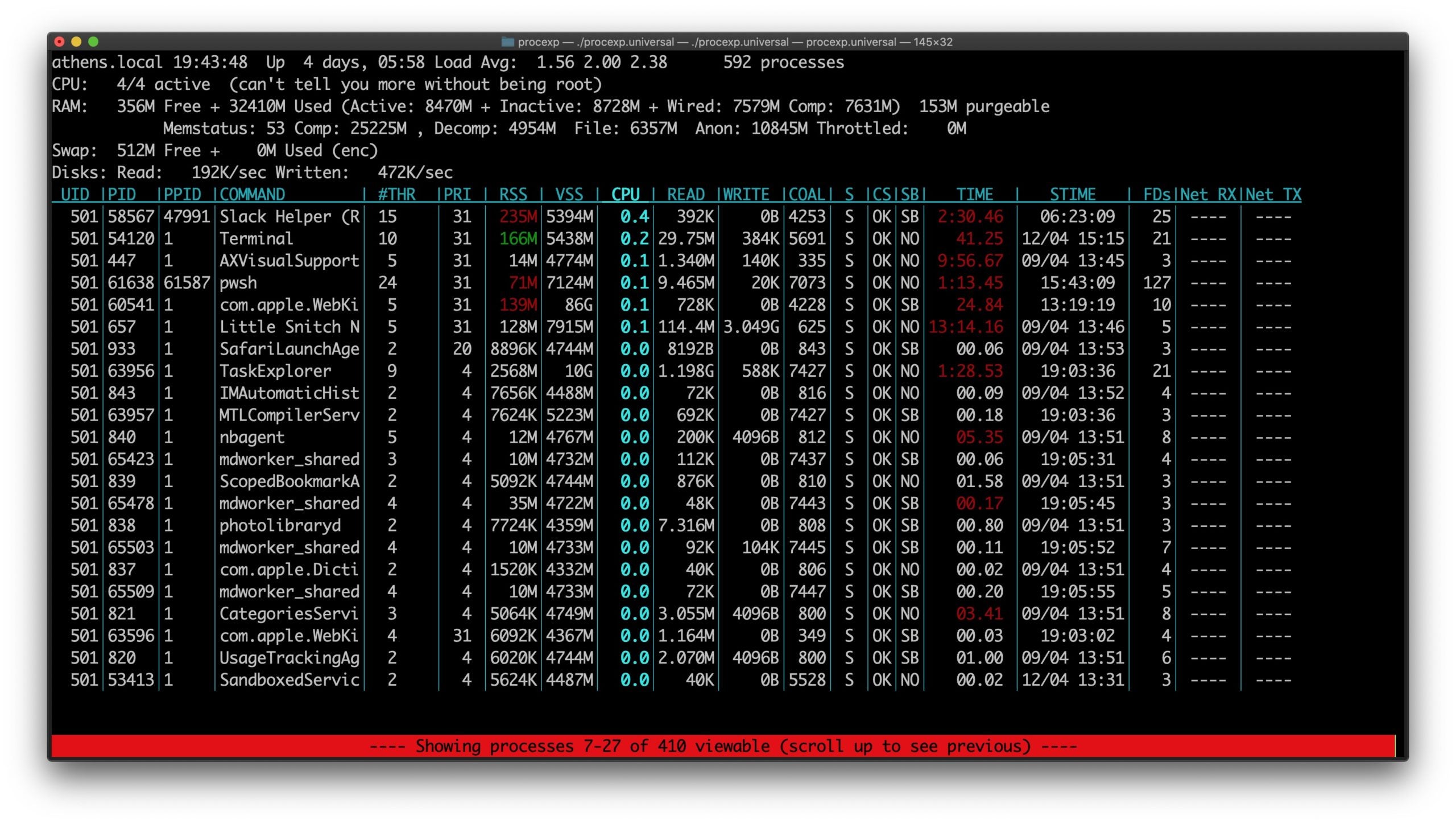
For a far more informative utility than the native top, try Jonathan Levin’s Process Explorer, which has a more useful interactive mode than the native tool. For example, pressing the Enter key on a process line will reveal more details about it, and processes can be filtered by name using the “/” key and specifying the process name.
Networking Tools For macOS
Being Unix based, you’ll find most of the standard network tools already present in macOS, including nc (aka netcat), ping, trace, ipconfig and so on. Note that both ftp and telnet are not available by default on the Mac since 10.13, High Sierra.
There is a useful built-in utility Network Utility.app (located at /System/Library/CoreServices/Applications/Network Utility.app) that combines a number of useful functions like Netstat, Whois and Port Scanning.
A version of the packet analyzer Wireshark is available for the Mac, and there is also the free, Mac-specific CocoaPacketAnalyzer tool as an alternative.
The venerable Little Snitch undoubtedly remains the de facto standard firewall / network monitoring tool on the platform. Although it isn’t free, it’s not expensive either (less than $50 at the time of writing), and even if you never use its many excellent features, just having it running on your system is a good deterrent for a number of macOS malware strains that exit when they detect that Little Snitch is present.
SQL Database Viewers
If you’re doing any kind of investigation into macOS itself or Incident Response, you’re going to need to be comfortable with SQLite. The Mac comes with a sqlite3 command line utility built-in, a front-end to the SQLite library that can evaluate queries interactively and display the results in multiple formats.
For GUI interfaces, the commerical TablePlus offers a modern, slick interface and can be used for free, but the free version limits you to no more than three open databases at a time. Personally, I prefer the open source DB Browser for SQLite. Though not particularly pretty, it’s robust, feature-rich and is well-maintained.
Miscellaneous Tools
In this section I list a few other utilities that I find very useful but which don’t fall into an easy category.
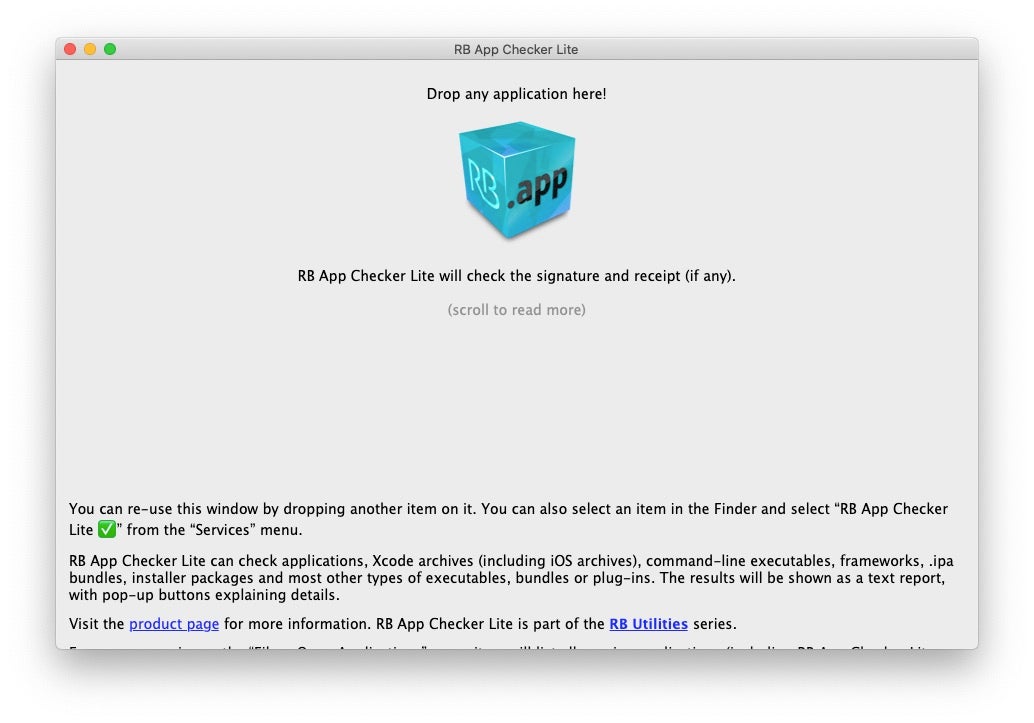
The first is a free little application called RBAppChecker Lite. This provides a GUI front end to system codesign and spctl utilities, and provides a very quick, nice and informative overview of the validity of an application bundle’s codesigning status. Unfortunately, the app appears to be in legacy status, but it still works well enough on the current version of macOS Catalina.
The Mach-O Explorer is a graphical Mach-O viewer for macOS that aims to provide a feature set similar to the venerable MachOView application.
In similar vein, dsdump is a modern replacement for the older class-dump utility for displaying the compiled Swift types and Objective-C classes in a Mach-O binary.
Finally, one of every reverse engineer’s basic tools is the strings utility. It’s worth noting that the macOS version of this tool is a little different from its Linux cousin, and in particular does not handle the same range of encodings. Fortunately, there is a great, free alternative called Floss that will serve you much better.
Conclusion
In this guide, I’ve tried to focus on tools that are particularly useful for those engaged in security research and infosec on the Mac platform. I’ve covered some tools that may be familiar from other platforms, but tried primarily to highlight macOS-specific tools that newcomers to the platform might not be familiar with yet or might not easily discover on their own. There should be enough here to get you set up with most of what you need for any macOS security research task, but of course, there’s plenty more to be discovered. Undoubtedly, as with any guide of this nature, I’ll have overlooked someone’s favorite essential tool (sorry!). If so, by all means hit me up on Twitter and let me know, and perhaps we can include it in an update to this guide.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security























