Hold On to Your Hats! Black Hat 2019 Takes Off!
And here we go! It’s that time of the year again, when hackers, researchers, gurus, executives, marketers and other assorted animals emerge from their burrows and blink into the bright lights, smoke, noise and crowds of Las Vegas and Black Hat 2019! So much to do, so much to see, so many amazing people, stories and technical innovations to discover. Quite a few of you discovered the SentinelOne booth at #222 today, and it was certainly a delight for us to discover you, too! If you didn’t quite make it today or you dropped by and need a reminder of what you saw after taking in the rest of a busy day, here’s a quick run down on what went on.

SentinelOne Announcement – Protecting Cloud Workloads
Today’s enterprise is all about the cloud, but other security solutions are behind the curve. When you are constantly spinning up multiple containers and web applications, evolving as your business grows, you need the same kind of visibility into what’s happening across your cloud workloads as you enjoy on your physical endpoints. SentinelOne’s Linux agent provides that visibility along with our best-of-class protection on every cloud workload, container and virtual machine on the network. You also need to know which web applications are vulnerable without impacting your productivity. SentinelOne’s Linux agent delivers that and more.
SentinelOne Disrupts the EDR Paradigm
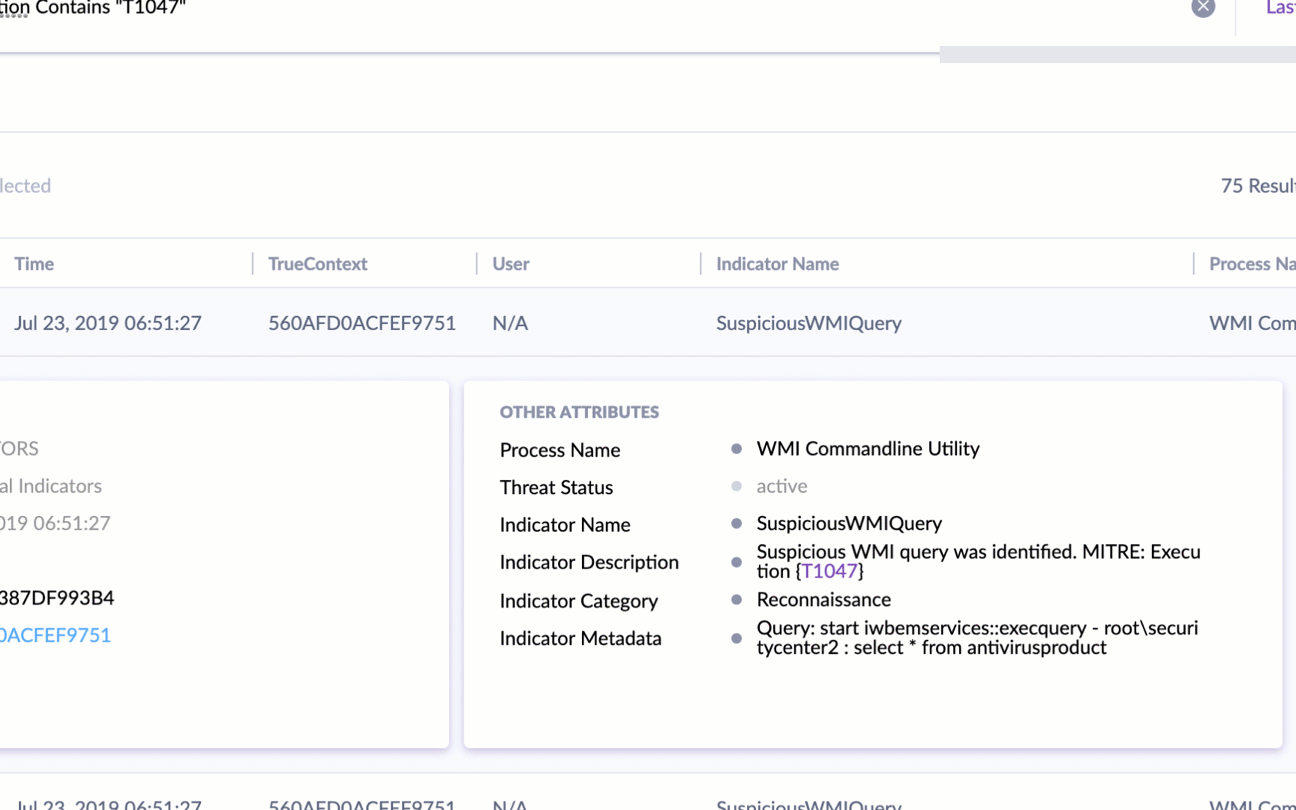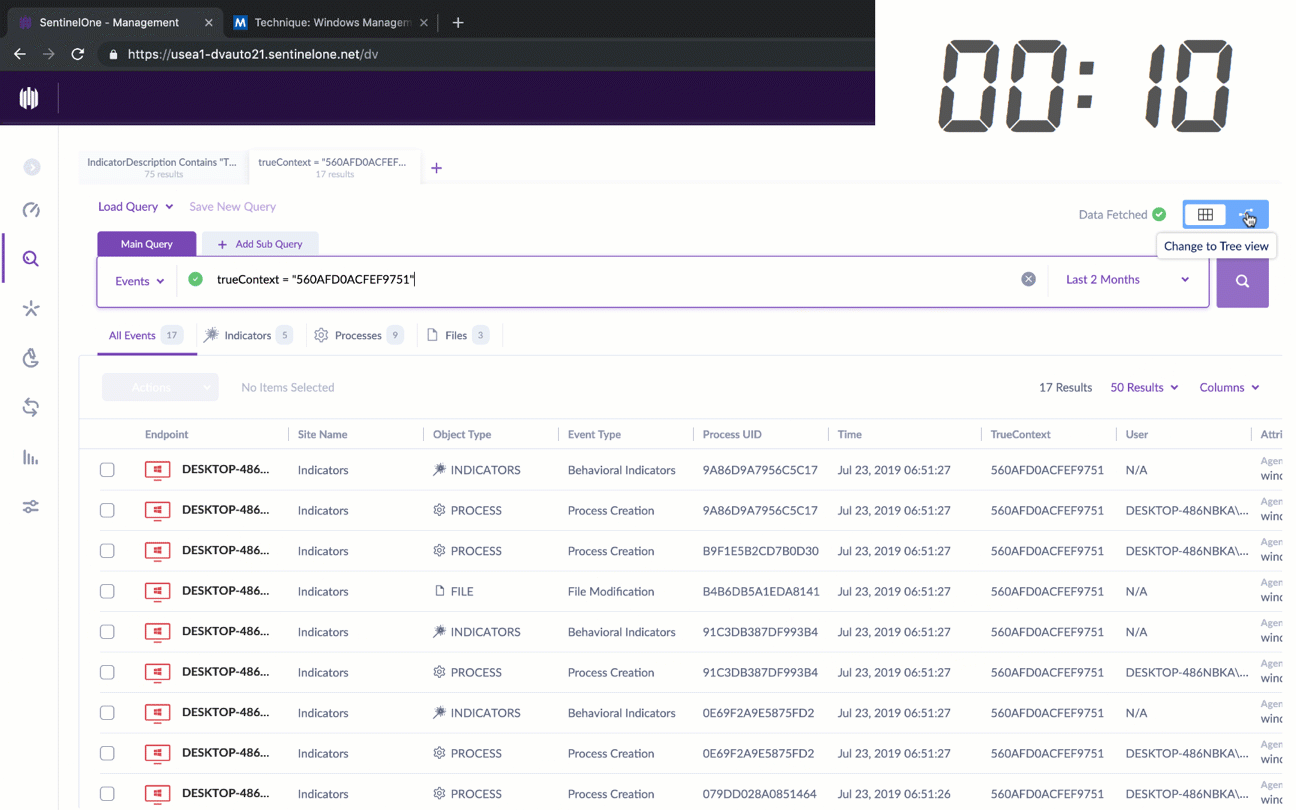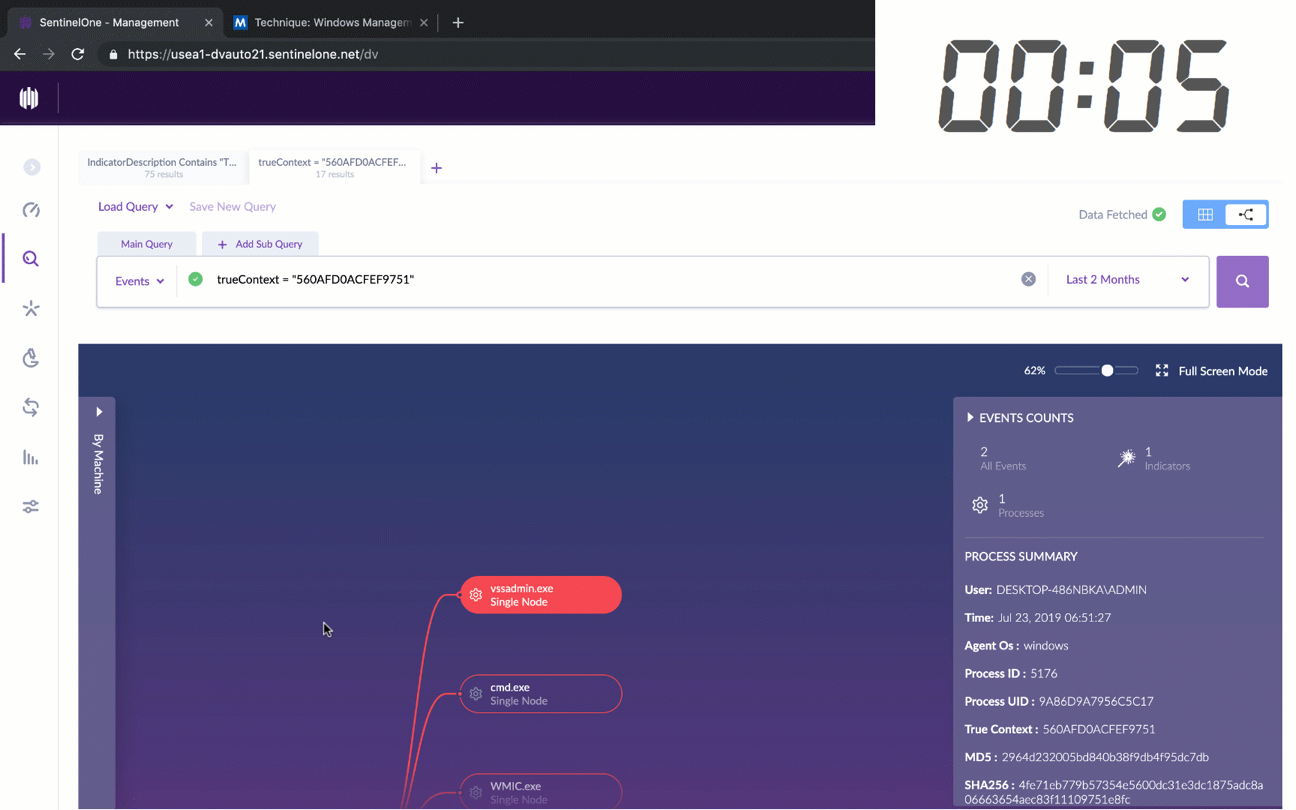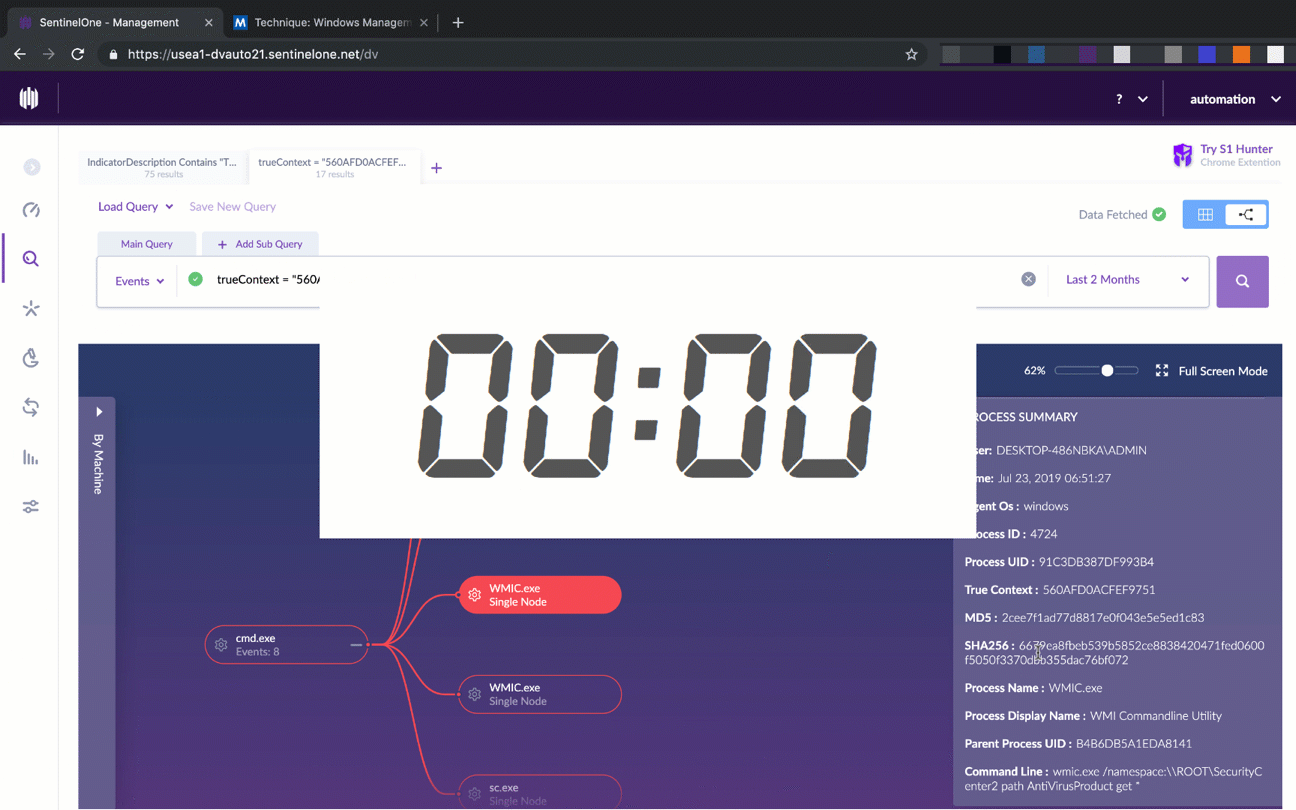
Security teams appreciate the power of the MITRE ATT&CK framework, but SentinelOne is the first and only solution to make this framework the new language of threat hunting by integrating MITRE tactics, techniques and procedures into the threat hunting query workflow.
Analysts can now put behind them the laborious manual work other solutions need in order to correlate and investigate findings. With SentinelOne, just a few clicks will allow security personnel to discover where an attack is coming from, what it is trying to do, and how to fix it.
When an analyst sees an indicator of attack on the network, one or two clicks will reveal the entire context around the TTP: on which devices was it seen? Where did it come from? What else was it trying to do? With SentinelOne, threat hunting is as simple as the click of a button.
Zero Trust: Networks Protecting Endpoints
Our first guest of the day was Amit Bareket, Platform 81 co-founder who came to talk about how Perimeter 81’s Zero Trust Network will integrate with SentinelOne’s autonomous endpoint protection platform to offer business networks a unique and unrivalled protection. Legacy firewalls and VPNs cannot cope with today’s highly mobile users and cloud-based services.

With the help of Perimeter 81, corporate resources and services can be configured to only allow connections to SentinelOne-protected endpoints with no active threats, ensuring that your network and all connected endpoints stay clean of infections. A bad day for worms and attackers intent on lateral movement.
Targeted Content, Behavioral Analytics
Shortly after, we were pleased to welcome Splunk’s Don Leatham to the party, where visitors to Booth 222 were treated to an insightful presentation on how SentinelOne and Splunk work together to provide the essential data that helps keep businesses safe.

With the help of Splunk’s Security Operations Suite, SOC teams and analysts can get ahead of current and emerging threats through targeted content covering everything from insider threat detection to compliance and more. Don also explained how user behavior analytics can help security teams track anomalous behavior across users, devices and applications.
Context is King
Our third guest of the day was Wendy DeLuca from Recorded Future. Wendy explained how, through integration with the SentinelOne platform, SOC teams could save real time by triaging alerts with real-time context. We’re all aware of the pain felt by SOC teams struggling with security solutions that overwhelm them with too many alerts. Adding to the burden is the difficulty of classifying those alerts in meaningful ways. Without context, analysts are forced to spend precious time on inefficient manual research and threat hunting. And all that noise can lead to the worst possible outcome for the business: a genuine threat that is missed, precisely as happened to Target, resulting in a massive data breach.

With Recorded Future integrated within the SentinelOne management console, SOC teams can wave goodbye to the bad old days and let the software do the grunt work, freeing up the skilled analyst to concentrate on the tasks that only a human agent can do. Aside from faster response times, the business can also look forward to better ROI on existing security tools as data from, and to, these tools becomes more focused and more relevant.
There’s Parties? Of Course, There’s Parties!
Yeah, right, like you didn’t know…! All work and no play, makes for a dull con, we know that. But while we’re all trying to keep a lid on it and function at our best to get the most out of Black Hat 2019, letting off steam is an essential part of the yin/yang of a good hacker con. On Tuesday, we invited you to let your hair down and join us for a Sin City party with golf, gaming and more. And you all turned up in style!

Conclusion
It was a great first day in the Business Hall and we’re already excited about the response from many of you who came to visit the SentinelOne booth, #222. If you’re around tomorrow, drop in as we’ve got some amazing demos to show including ActiveEDR, device rollback and, the one that’s got all the networking gurus buzzing, Ranger IoT. We can’t wait to see you there!
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.



Leave a Reply
Want to join the discussion?Feel free to contribute!