The Coronavirus has prompted thousands of information security professionals to volunteer their skills in upstart collaborative efforts aimed at frustrating cybercriminals who are seeking to exploit the crisis for financial gain. Whether it’s helping hospitals avoid becoming the next ransomware victim or kneecapping new COVID-19-themed scam websites, these nascent partnerships may well end up saving lives. But can this unprecedented level of collaboration survive the pandemic?
 At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the COVID-19 Cyber Threat Coalition (CTC), which comprises rough 3,000 security professionals who are collecting, vetting and sharing new intelligence about new cyber threats.
At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the COVID-19 Cyber Threat Coalition (CTC), which comprises rough 3,000 security professionals who are collecting, vetting and sharing new intelligence about new cyber threats.
Nick Espinosa, a self-described “security fanatic,” author and public speaker who’s handling communications for the CTC, said the group does most of its work remotely via a dedicated Slack channel, where many infosec professionals seem eager to counter the gusto with which the cybercriminal community has sought to profit by exacerbating an already difficult situation.
“A nurse or doctor can’t do what we do, and we can’t do what they do,” Espinosa said. “We’ve seen a massive rise in threats and attacks against healthcare systems, but it’s worse if someone dies due to a malicious cyberattack when we have the ability to prevent that. A lot of people are involved because they’re emotionally attached to the idea of helping this critical infrastructure stay safe and online.”
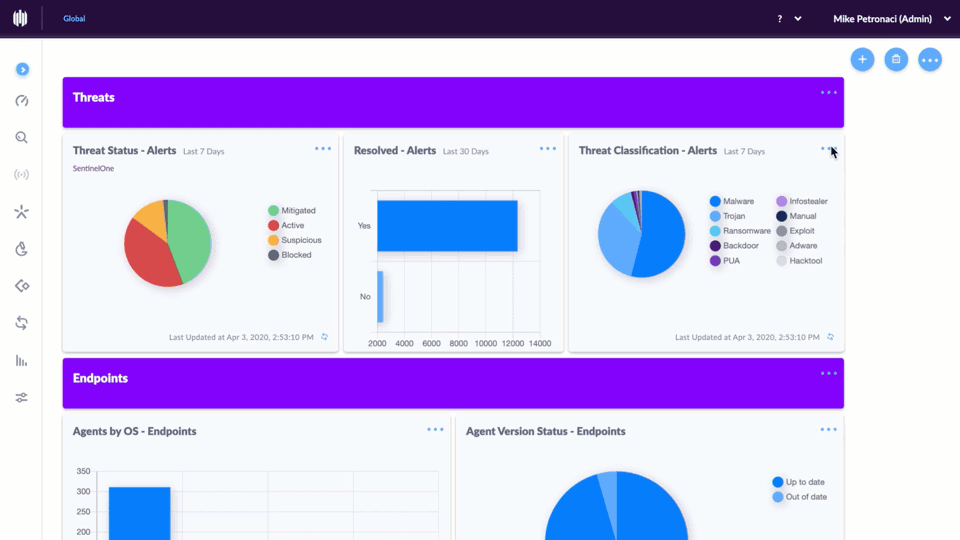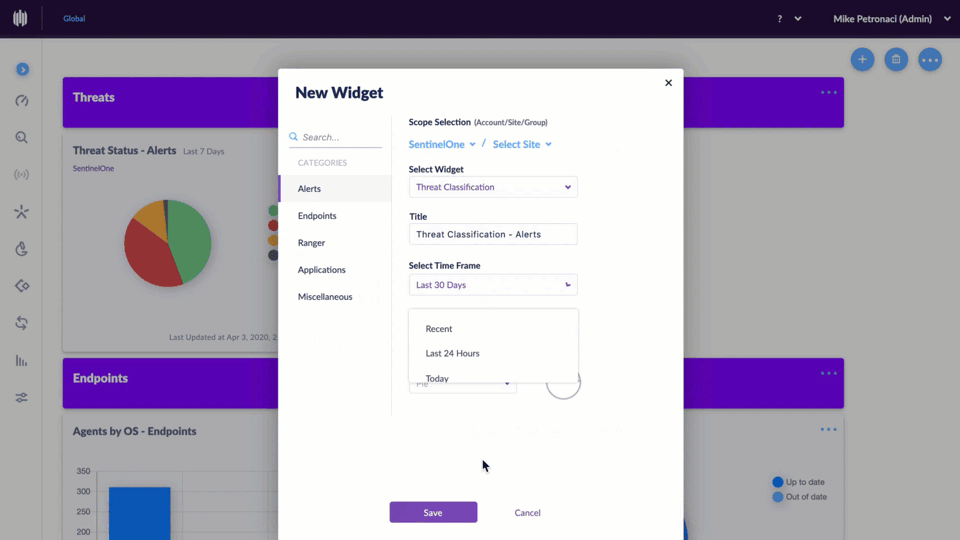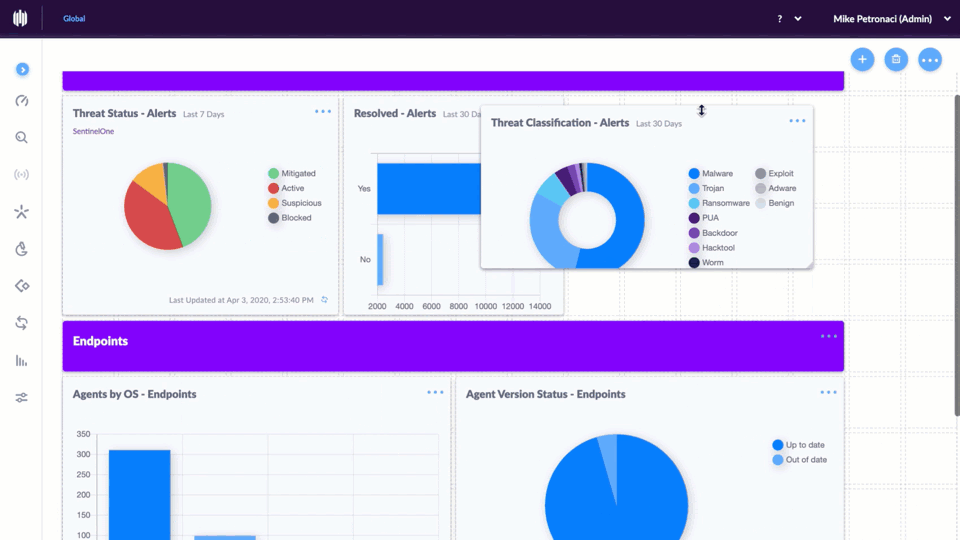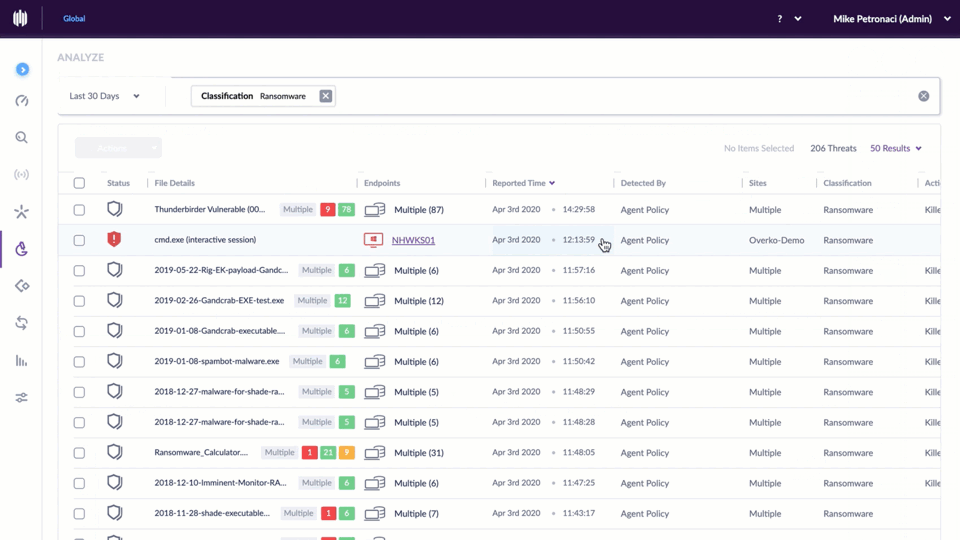
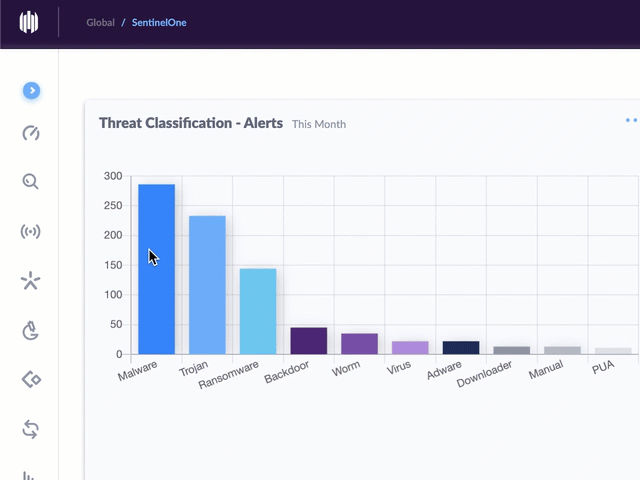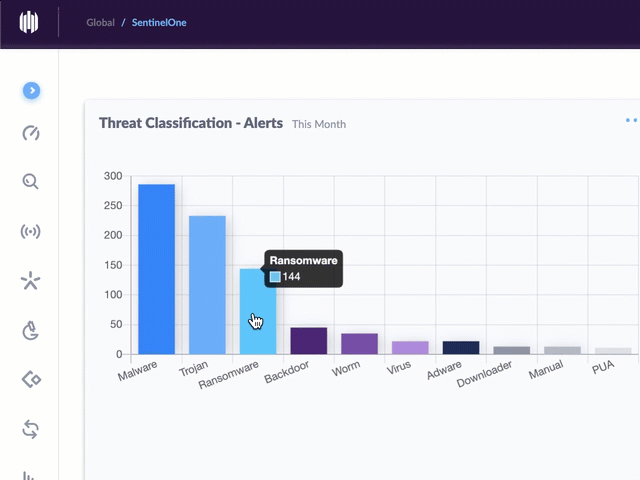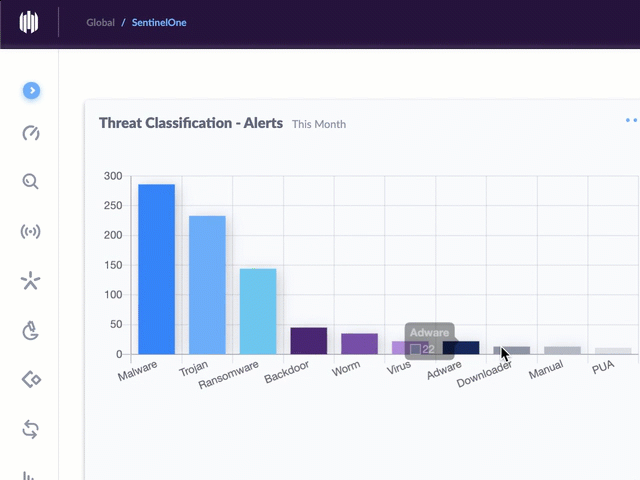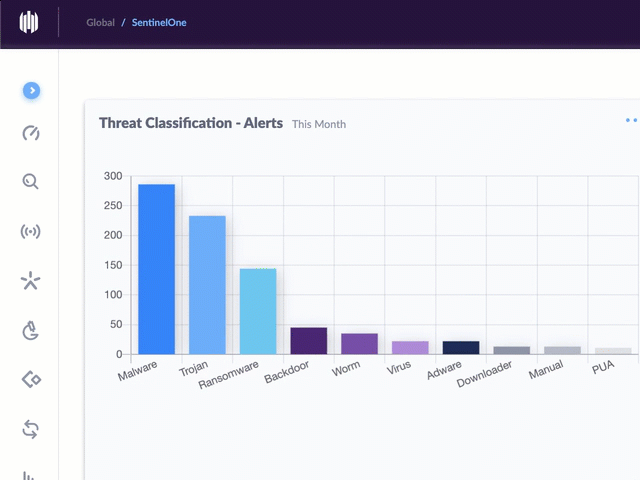
Using threat intelligence feeds donated by dozens of cybersecurity companies, the CTC is poring over more than 100 million pieces of data about potential threats each day, running those indicators through security products from roughly 70 different vendors. If at least 10 of those flag a specific data point — such as a domain name — as malicious or bad, it gets added to the CTC’s blocklist, which is designed to be used by organizations worldwide for blocking malicious traffic.
“For possible threats, meaning between five and nine vendors detect an indicator as bad, our volunteers manually verify that the indicator is malicious before including it in our blocklist,” Espinosa said.
Another Slack-based upstart coalition called the COVID-19 CTI League spans more than 40 countries and includes professionals in senior positions at such major companies as Microsoft Corp and Amazon.com Inc.
Mark Rogers, one of several people helping to manage the CTI League’s efforts, told Reuters the top priority of the group is working to combat hacks against medical facilities and other frontline responders to the pandemic, as well as helping defend communication networks and services that have become essential as more people work from home.
“The group is also using its web of contacts in internet infrastructure providers to squash garden-variety phishing attacks and another financial crime that is using the fear of COVID-19 or the desire for information on it to trick regular internet users,” wrote Reuters’ Joe Menn.
“I’ve never seen this volume of phishing,” Rogers told Reuters. “I am literally seeing phishing messages in every language known to man.”
Among the more mature organizations working to counter the threat from COVID-19 scammers is the Cyber Threat Alliance, a industry group founded in 2017 that counts among its members more than two dozen major cybersecurity firms that are all required to regularly share threat intelligence with other members.
“One thing we’re paying attention to in addition to phishing and malware attacks is anything targeting stuff involved in the pandemic response, such as the manufacturers of protective gear, testing kits, or hospitals,” CTA President Michael Daniel told KrebsOnSecurity. “One of those organizations getting hit with ransomware now would be really bad, and we want to make sure if we see that we’re alerting and working with law enforcement.”
Earlier this month, the international police network INTERPOL issued a warning to law enforcement in nearly 200 member countries, saying it had detected “a significant increase in the number of attempted ransomware attacks against key organizations and infrastructure engaged in the virus response.”
The alert came after several top ransomware gangs pledged a moratorium on attacking hospitals and other care centers for the near future. Nevertheless, these group have continued to target companies on the periphery of the pandemic response, including virus testing labs, N95 mask production facilities, and companies engaged in vaccine research.
The CTC’s Espinoza said it would be a potentially fatal mistake to assume all cybercriminal groups might observe such a cease-fire.
“We might have independent criminal groups saying they won’t hit hospitals but they’ll hit everyone else, but that doesn’t prevent them from sending phishing emails and masquerading as the World Health Organization or the Centers for Disease Control,” he said. “These are people who have no problems locking out little old ladies out of their computers for 800 bucks, and of course there are state-sponsored hackers who love any opportunity to sow discord and disrupt things.”
SURVIVING THE PANDEMIC
The CTA’s Daniel said while it’s great to see so much voluntary collaboration between the cybersecurity industry, governments and law enforcement, he’s been thinking a lot lately about how to sustain these relationships and networks once the urgency of the pandemic subsides.
Formerly special assistant to President Obama and cybersecurity coordinator on the National Security Council, Daniel said he sees preserving and enhancing this information sharing effort post-COVID as one of the biggest policy issues facing the federal government over the next few years.
“Information sharing is easy to talk about, and hard to do in practice,” Daniel said. “I don’t use the term ‘public-private partnership’ because it’s been bandied about so much over the years that I don’t know what it means anymore. It’s probably best described as ‘working together on an operation.’”
What prevents private companies from working more closely and frequently with governments on operations to target cybercrime organizations and networks? Daniel said on the government side, there are real concerns that working with one or two particularly clueful or effective companies (versus all of them) might give the impression that the government is showing favoritism, or picking winners and losers in the market.
“But you have to do that to some extent because the truth is some companies matter in this space, and a lot don’t,” Daniel said. “The government has to accept that, determine what are the objective rules, and establish transparency so that [their efforts] aren’t seen as some secret club but as part of a normal process.”
Daniel said governments in general also need to get more comfortable sharing information about operations targeting specific crime groups in advance of those actions.
“The government has to figure out how to let the private sector in on some of the planning and preparation,” he said. “If you want [the cybersecurity industry’s] help against certain targets, you have to tell us who they are ahead of time. But this goes against how governments operate in almost every way.”
On the private sector side are issues of how for-profit companies can closely collaborate with the government without being perceived as potentially compromising the privacy and security of their customers, or as simply an agent of the government.
“For companies, the question is how do you deal with the liability and other questions that come with that,” Daniel said. “These are very real impediments, and why I think we need to get past the endless discussions of public-private partnerships and start talking about what we can do to coordinate actions against these groups so we can have a more strategic impact on the adversary.”
![]()





 At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the
At least three major industry groups are working to counter the latest cyber threats and scams. Among the largest in terms of contributors is the 


 Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.
Nineteen of the weaknesses fixed on this Patch Tuesday were assigned Microsoft’s most-dire “critical” rating, meaning malware or miscreants could exploit them to gain complete, remote control over vulnerable computers without any help from users.